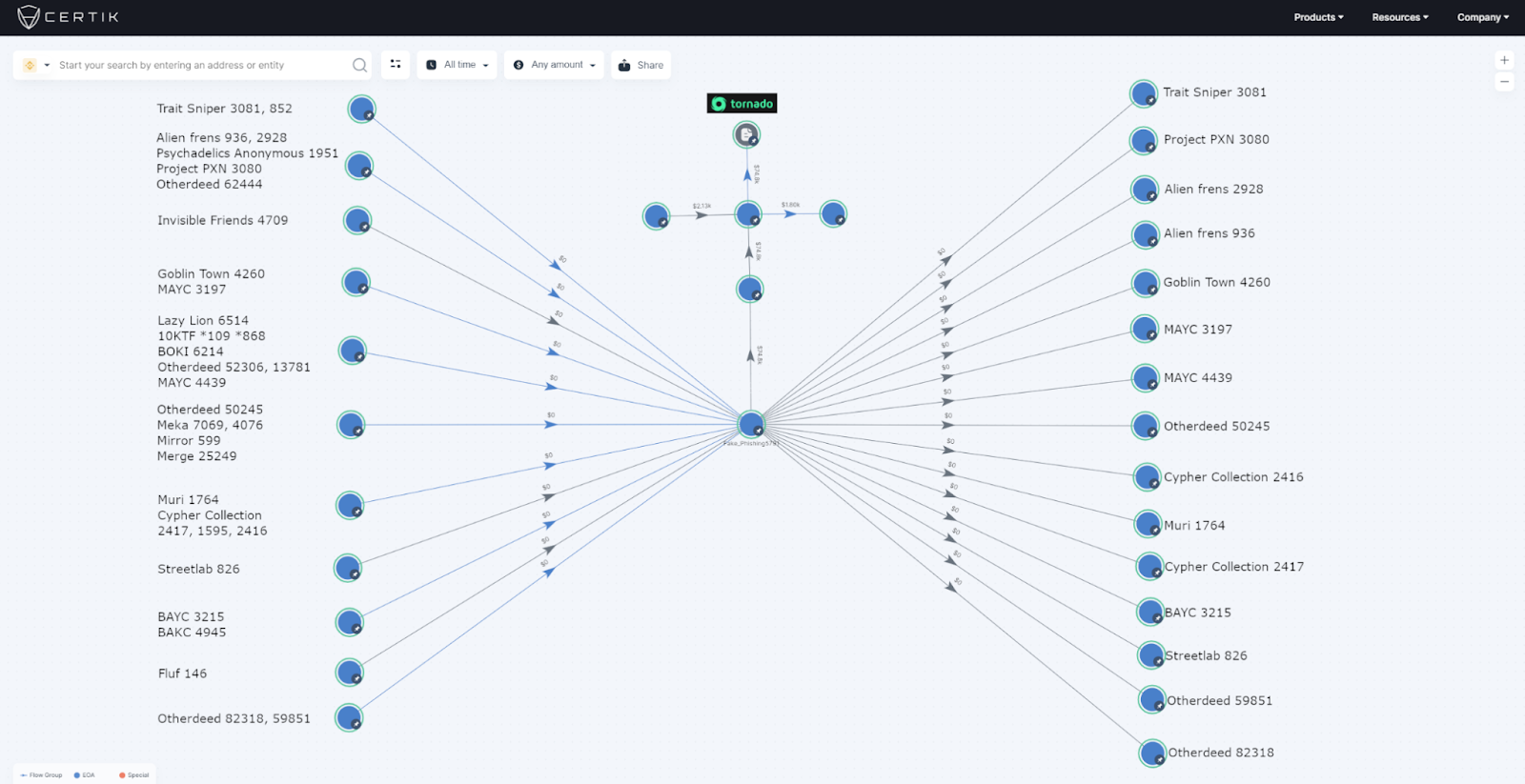
On 04 June 2022, Bored Ape Yacht Club (BAYC) was compromised for the second time this year, with the hacker specifically targeting BAYC, MAYC and OthersideMeta holders. In total, 32 NFTs were stolen from a variety of projects which included 2 MAYC, 1 BAYC, 1 BAKC and 5 Otherdeed. Overall, ~142 ETH was deposited to Tornado Cash through associated EOA’s.
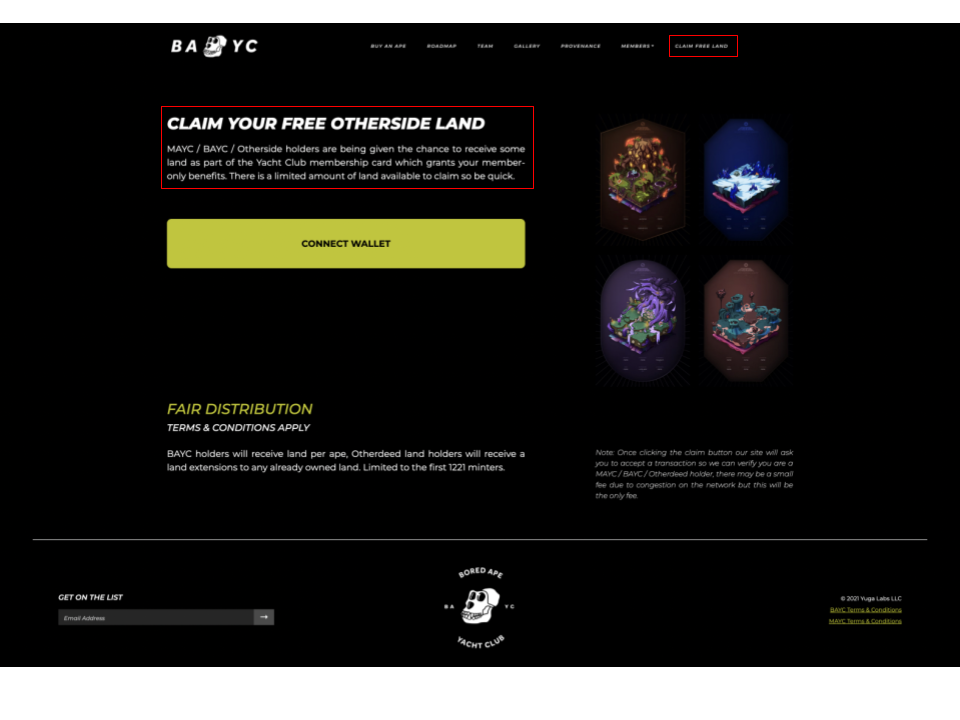
The phishing site posted on the BAYC Discord was a carbon copy of the official projects website, yet with subtle differences. Firstly, there were no links to social media accounts on the phishing site. There was also an added tab titled “claim free land” that specifically advertised to holders of popular NFT projects.
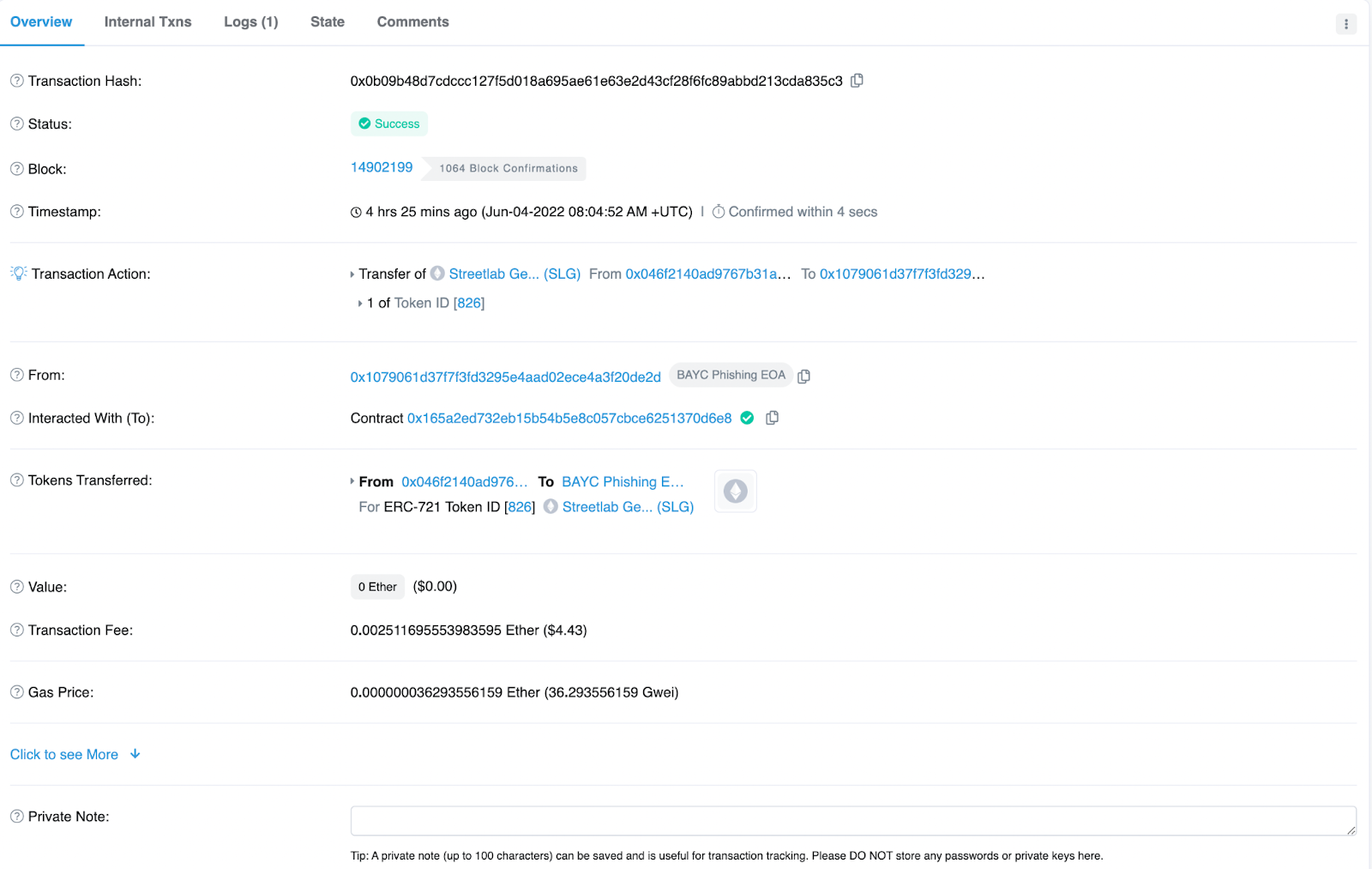
In todays attack (June 4th), the EOA related to the phishing site was identified as EOA 0x10790 OpenSea account (Now blocked). We can see the first stolen NFT coming into the wallet at 08:04:52 AM UTC in the following txn:
Following an influx of stolen NFTs, the attacker began to sell the collected assets at 08:25:42 AM UTC. The first asset, Goblintown #4260 was sold for 5.3 ETH ($9.3k).
Once the attacker had sold all the stolen NFTs, they transferred ~142 ETH into two different EOAs
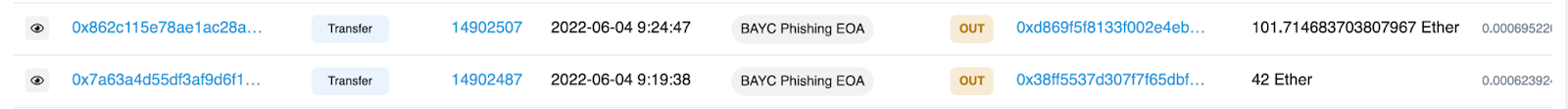
EOA 0xd869… then deposits 100 ETH into Tornado Cash with EOA 0x38ff… transferring 41.9 ETH to EOA 0x15331 which then begins to deposit the ETH to the mixer.
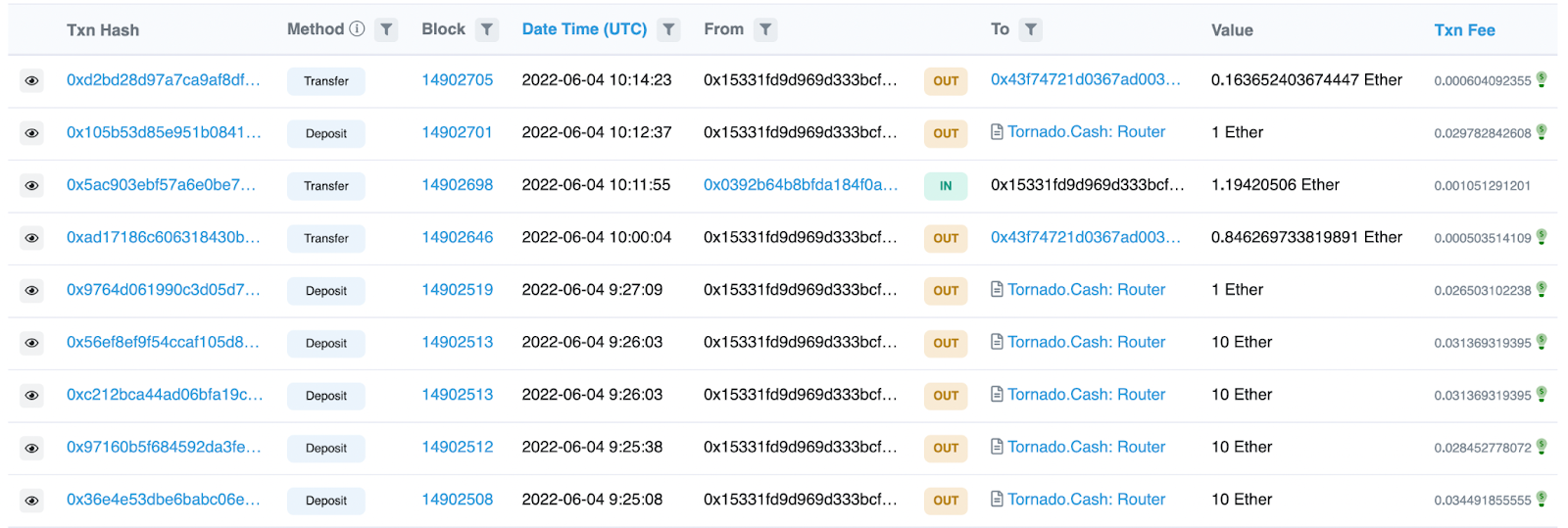
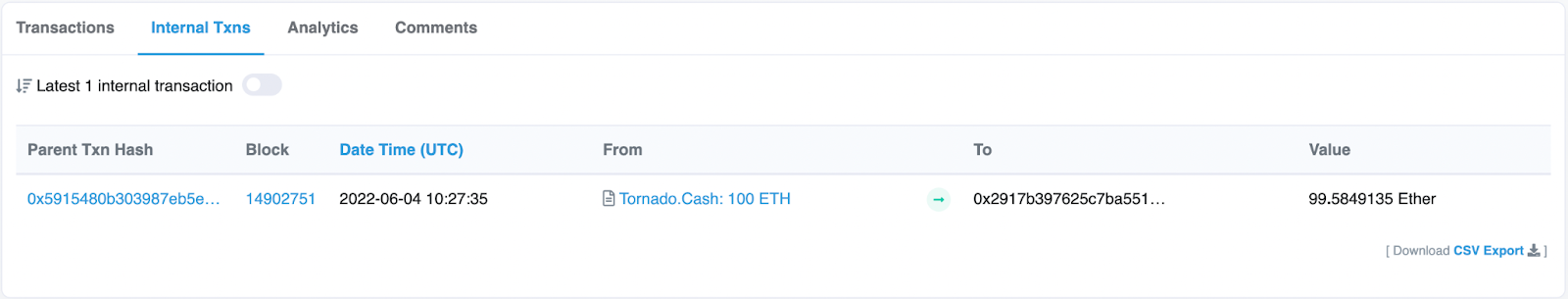
In addition to this on-chain evidence, another EOA was discovered that likely redeemed the 100 ETH deposited into Tornado Cash by 0xd869... We can see that 100 ETH was sent to the mixer at 09:24:47 AM UTC followed by EOA 0x2917B at 10:27:35 AM UTC receiving 99.5 ETH from Tornado Cash in the below txn:
EOA 0x2917… then sends the redeemed ETH to 3 wallets, with 20 ETH going to the same EOA that deposited the 100 ETH at 09:24:47 AM UTC, demonstrating the connection between the depositor and redeemer.
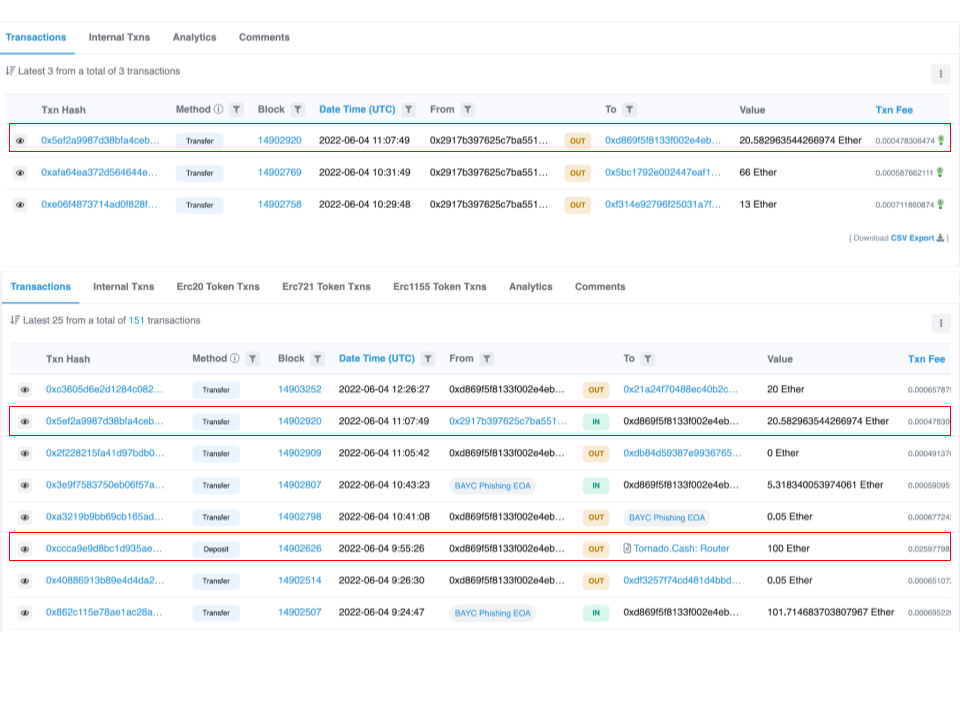
Whilst it’s impossible to be certain that the 99.5 ETH redeemed by 0x2917… are the funds associated with today's attack, it is certainly probable that these are the stolen funds post mixer due to the 20.5 ETH being sent to the depositor address. The majority of the funds were sent to EOA 0x5bC17, which is where they remain at the time of writing.
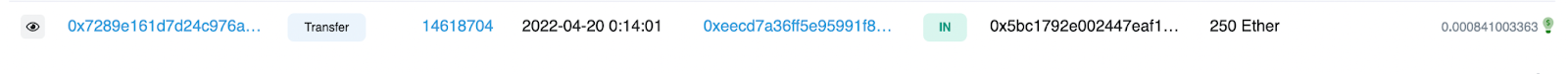
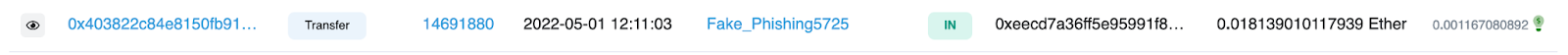
When looking through the previous transactions in 0x5bC1… we can see a transaction coming in from EOA 0xEECd7 for 250 ETH. When looking into the transactions of 0xEECCd… we can see one particular incoming transaction from 0x29D83 labeled here as Fake_Phishing5725, which was involved in the a previous phishing scam.
Furthermore, the incoming transactions to 0x5bC1… have their funds originating from Tornado Cash in multiple instances, for example from EOA 0xE5013 and 0x13E52.
Because of these links, it is likely that EOA 0x5bC1… is not only associated with the BAYC phishing attack today, but also previous phishing attacks. The established link between the Tornado Cash depositor and redeemer is clear. Furthermore, the majority of the ETH redeemed from EOA 0x2917… was sent to an address where funds it receives originate from Tornado Cash, as well as one link to an EOA associated with a previous phishing scam.
This is the second time this year that BAYC has been compromised by phishing attacks, with their Instagram account being hacked on April 25, 2022 leading to a total of 91 NFTs being stolen worth approx $2.6 Million or 888 ETH. The hacker leveraged access to BAYC’s Instagram and posted a fraudulent link to a copycat of BAYC’s website with a fake Airdrop, where users were prompted to sign a ‘safeTransferFrom’ transaction. This in turn transferred the users NFT’s to the scammer's wallet. Back then, the assets were transferred to address 0x8c793.
Skytrace