Introduction
On 6th January 2024, the MangoFarmSOL project conducted an exit scam leading to losses estimated around ~$1.32 million which is the largest exit scam that we have investigated in 2024 so far. The stolen funds primarily consisted of SOL tokens, which were then laundered through various channels, first bridging to the Ethereum network via wormhole and allbridge and then deposited into platforms such as Railgun (mixer), eXch and FixedFloat (instant exchanges).
Event Summary
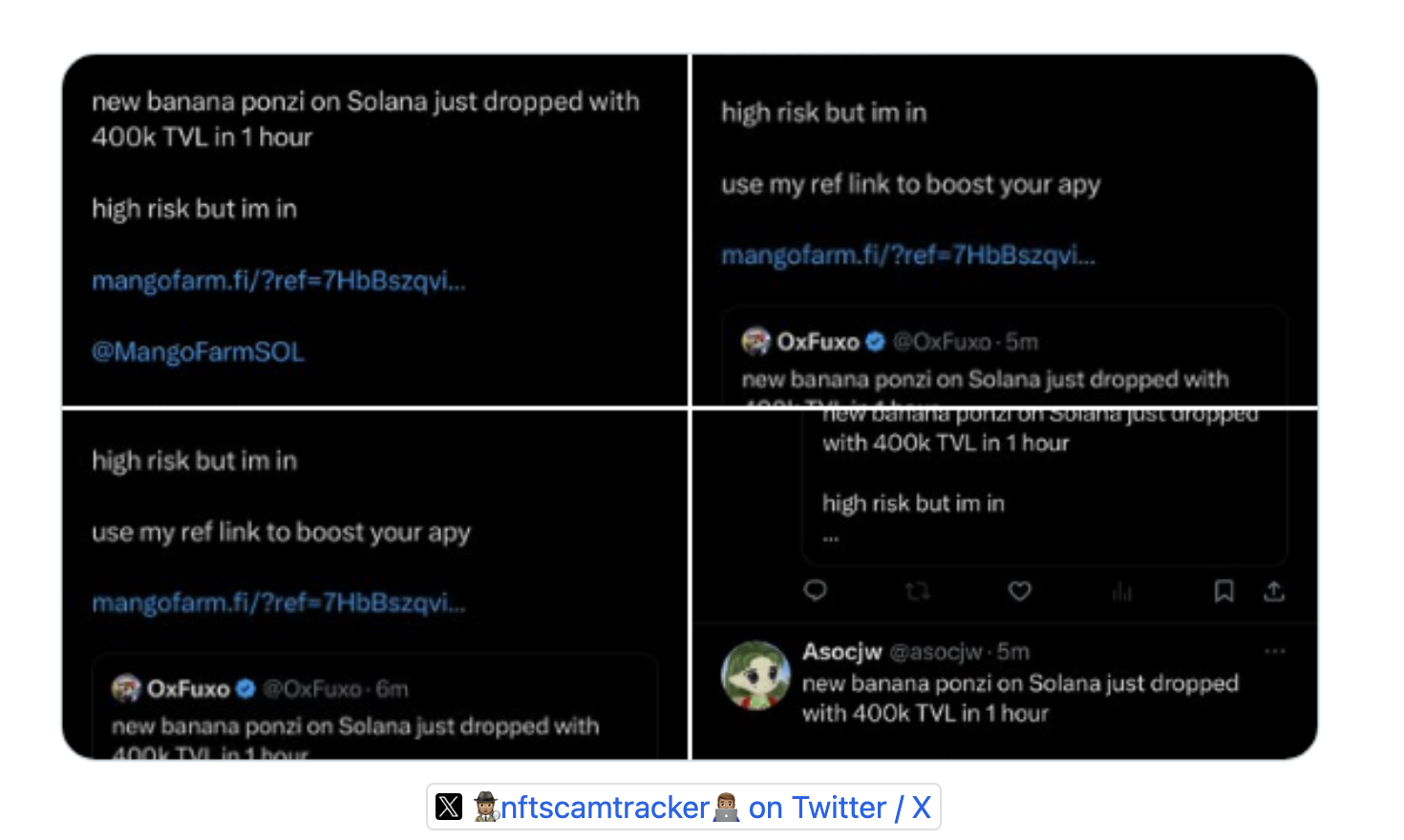
MangoFarmSOL marketed itself as a farming protocol on the Solana blockchain, promising high yields and a lucrative MANGO token airdrop. To participate, users were encouraged to deposit Solana tokens. The project gained traction through a coordinated influencer campaign and the promise of a $MANGO token airdrop scheduled on the 10th January.
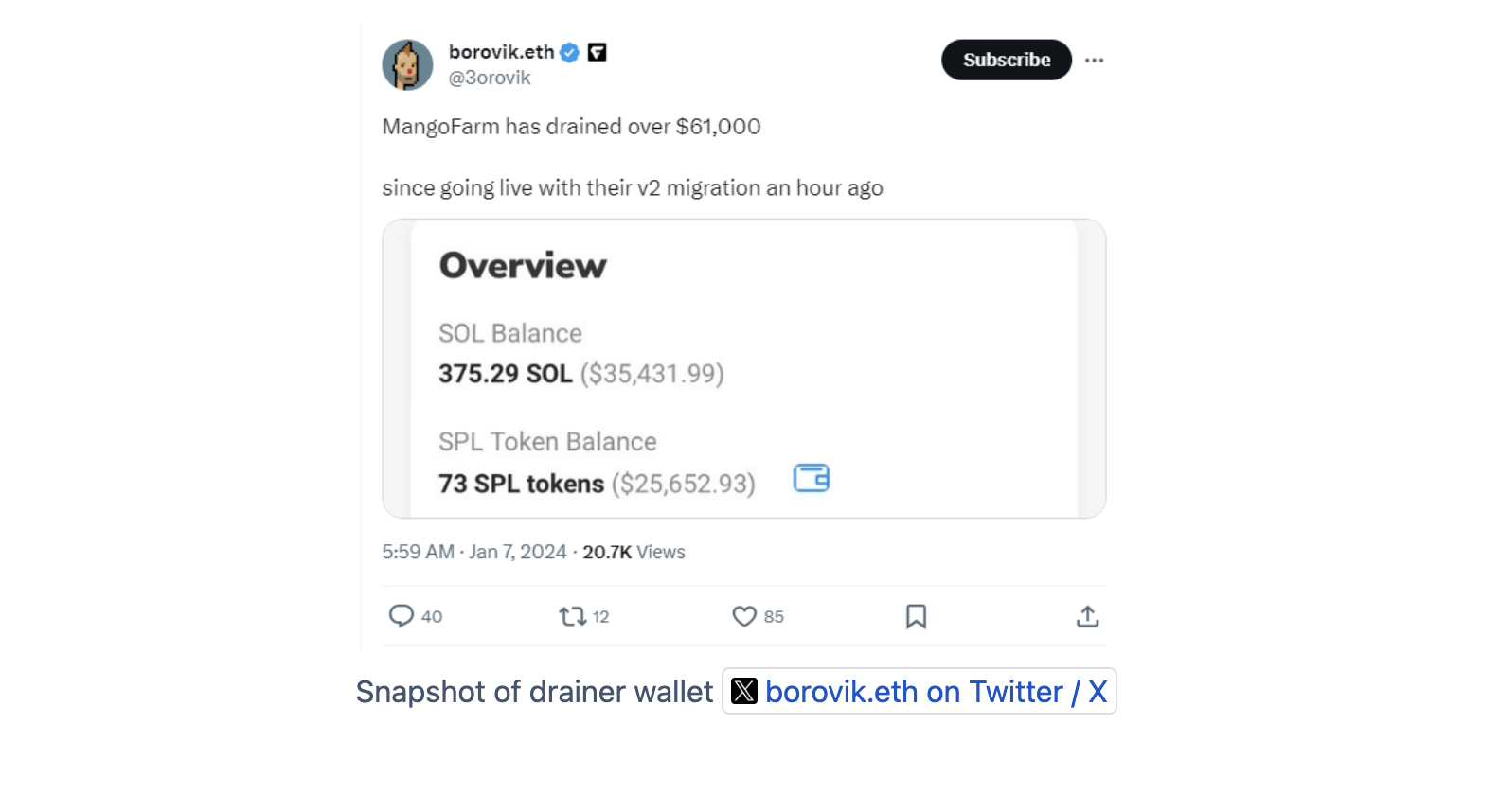
However, the MangoFarmSOL team executed an exit scam, transferring 13,512 SOL tokens (~$1.26 million at the time) from users' deposits in the project's contract. Additionally, a malicious frontend was deployed, misleading users into an "EmergencyMigration" and tricking them into transferring their assets, leading to a further theft of ~$60k. Following these actions, MangoFarmSOL deactivated its social media accounts and website, leaving many in the community at a loss and highlighting the risks inherent in the DeFi space.
Detailed Analysis of the Exit Scam
The Build-up:
(3 Jan) Social Media Campaign: The project utilized social media influencers to boost its credibility and attract a larger audience.
(5 Jan) $MANGO Token Launch Info: The team published a piece on Medium claiming that an airdrop of $MANGO token will be scheduled on the 10th, with rewards determined by points gained from SOL deposited and users referred.
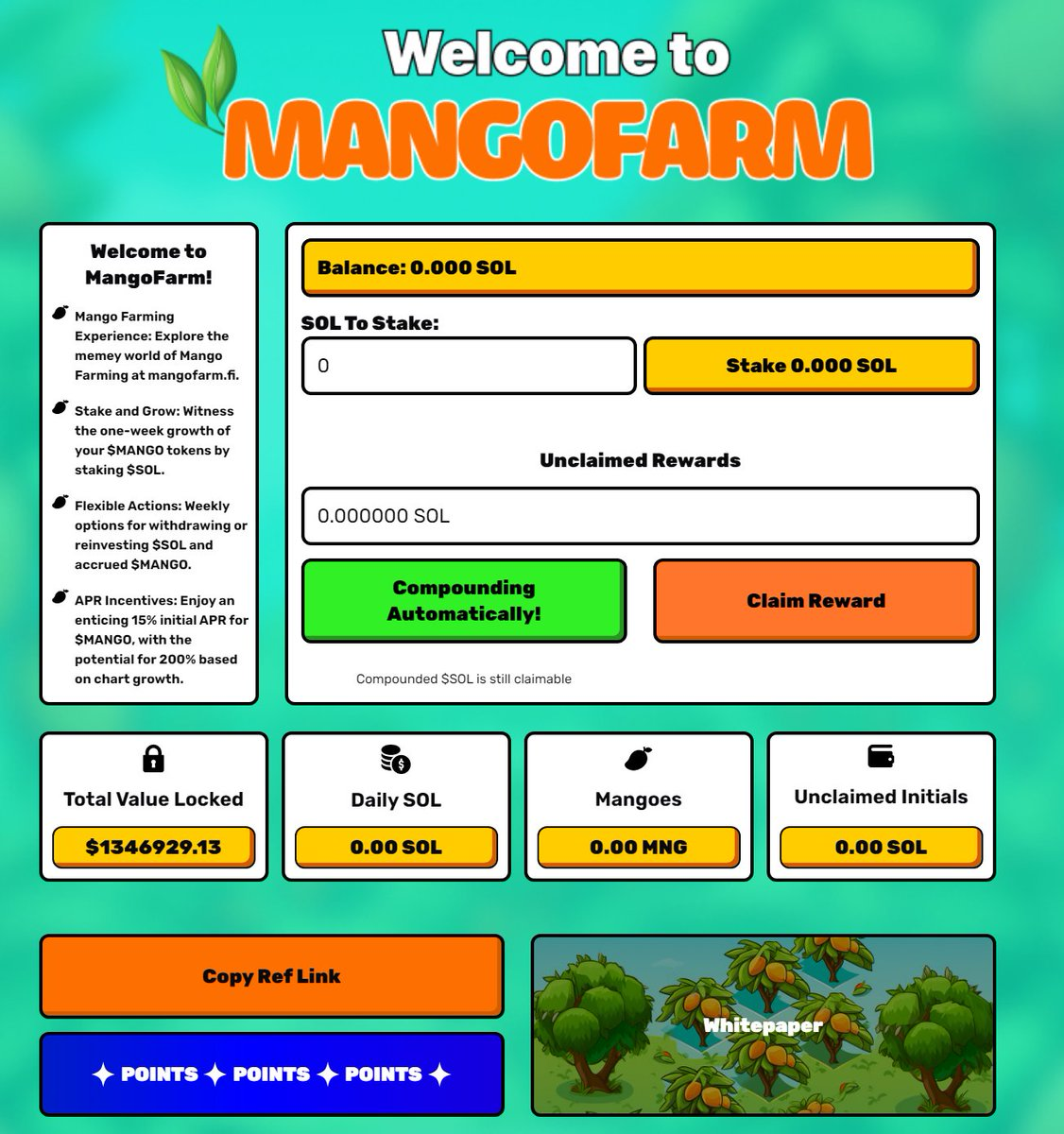
(3 Jan-7 Jan) User Deposits: Users deposited SOL into MangoFarmSOL's contract, enticed by the promise of the MANGO token airdrop and likely due to the marketing by influencers on twitter driving traffic. This led to over ~$1.3M in TVL as shown in the screenshot below.
The Exit Scam:
- Withdrawal of Funds: The MangoFarmSOL team initiated the exit scam by withdrawing a total of 13514 SOL (~$1.26M) tokens deposited by users into the Mango contract to the wallet 8ggvi.
 First transaction of 135 SOL transfer from Mango contract (Bfg5SM) to wallet 8ggvi
First transaction of 135 SOL transfer from Mango contract (Bfg5SM) to wallet 8ggvi
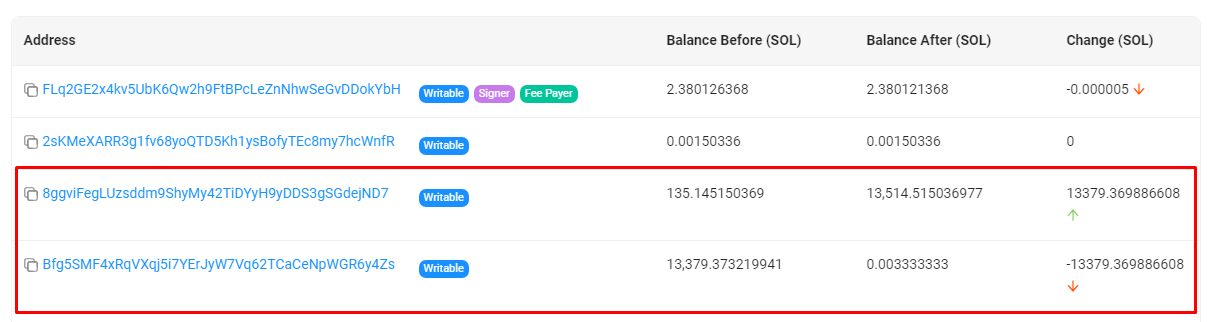 Second transaction of 13379 SOL transfer from Mango contract (Bfg5SM) to wallet 8ggvi
Second transaction of 13379 SOL transfer from Mango contract (Bfg5SM) to wallet 8ggvi
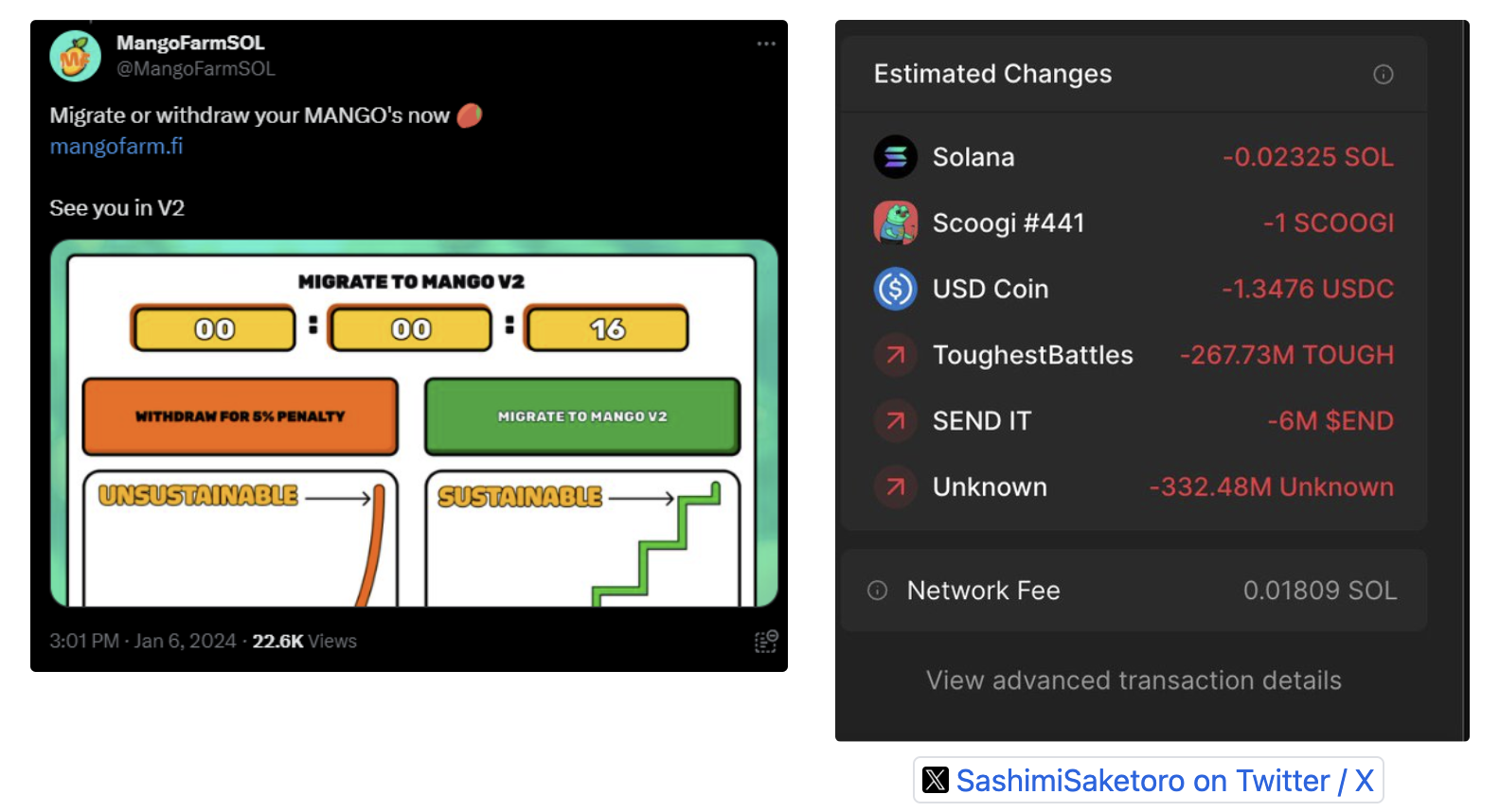
- Malicious Frontend: Subsequently, a malicious frontend was introduced under the guise of an "emergency migration," which was also tweeted by the projects official twitter account tricking users into further transactions that led to the theft of additional assets, estimated to be a total of ~$60k.
- Communication Shutdown: MangoFarmSOL then deactivated its twitter account & took down the website as well, making away with the stolen funds.
Movement of Funds:
Summary
The funds bridged to the Ethereum network ended up consolidating in three main areas
- eXch: ~292 ETH
- Railgun: ~263 ETH
- FixedFloat: ~26 ETH
Funds Stolen From Mango Contract
- Initial Theft Transaction:
- A total of 13.5K SOL, worth approximately $1.26 million, was stolen from the Mango contract and sent to the address 8ggviFegLUzsddm9ShyMy42TiDYyH9yDDS3gSGdejND7.
- Obfuscation and Conversion:
- 9,458 of the stolen SOL was sent to 4nBETJ to obfuscate the trail of funds.
- All SOL in both 8ggvi & 4nBE were subsequently swapped for USDC.
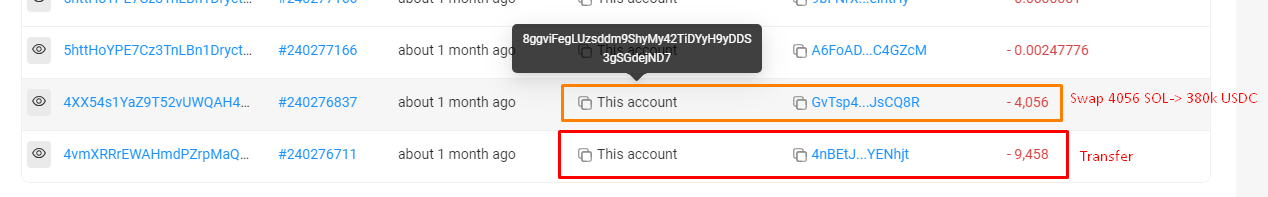 Account 8ggviFegLUzsddm9ShyMy42TiDYyH9yDDS3gSGdejND7
Account 8ggviFegLUzsddm9ShyMy42TiDYyH9yDDS3gSGdejND7
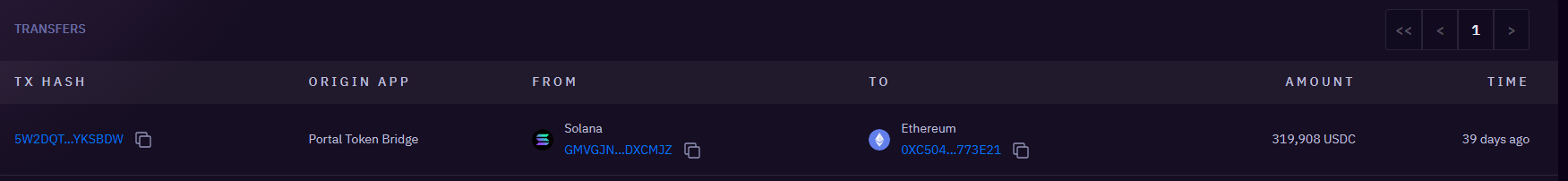
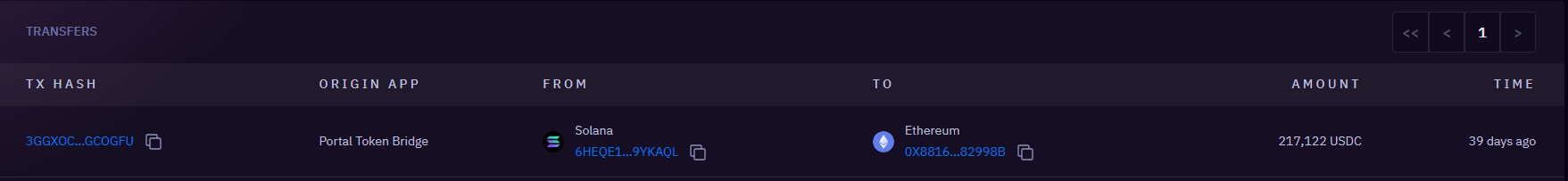
- Bridging to Ethereum via Wormhole:
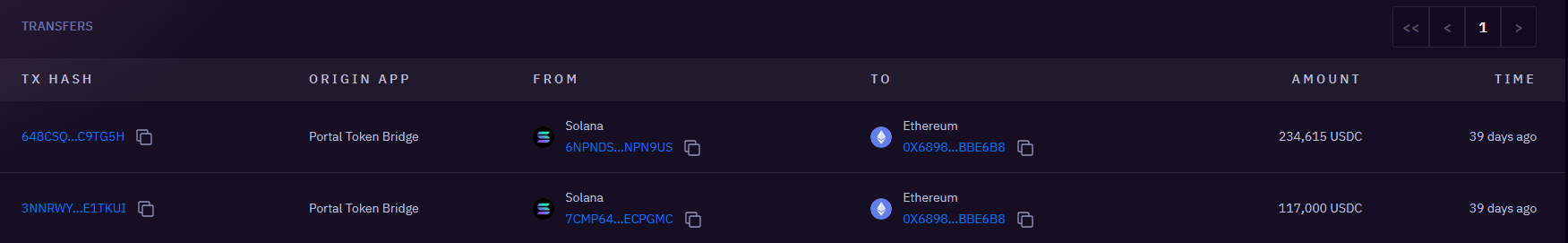
- The acquired USDC was bridged from the Solana network to Ethereum via the wormhole bridge, targeting multiple Ethereum addresses over multiple transactions to 4 different addresses on ETH
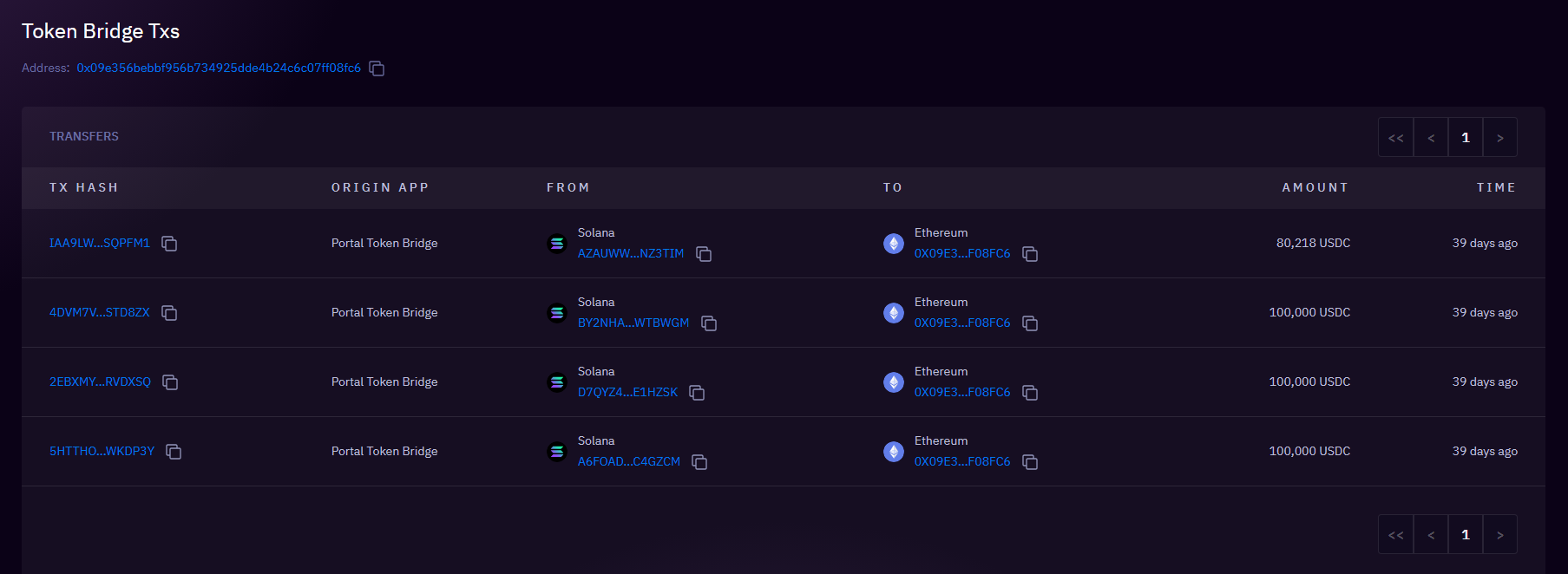 380k bridged over 4 transactions to 0x09e3
380k bridged over 4 transactions to 0x09e3
- Final Laundering Steps:
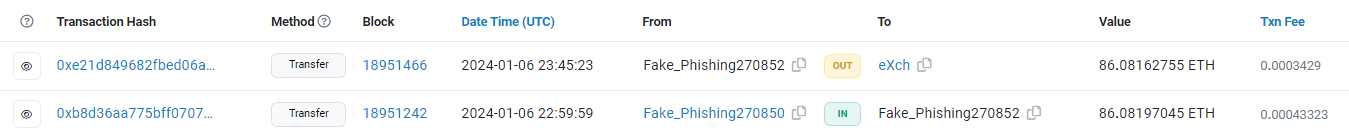
- Once on the Ethereum network, the USDC was swapped for ETH. The stolen funds were then laundered through Railgun (a privacy mixer) & also exchanged via eXch (instant exchange) to further obfuscate funds.
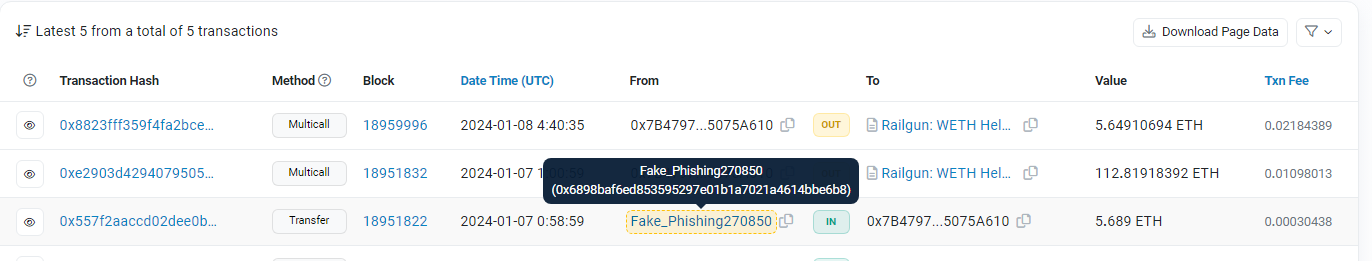 Example of transfers to railgun
Example of transfers to railgun
Funds Stolen From Malicious Frontend Drainer
- Consolidation and Conversion:
- Assets stolen through the malicious frontend exploit were consolidated into SOL, which was then swapped for approximately $58.6k in USDC.
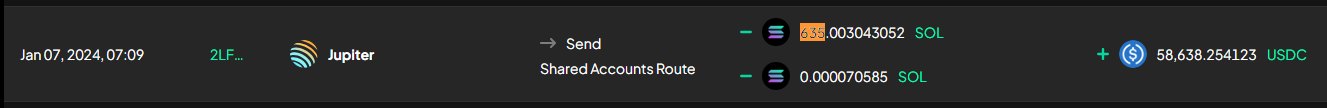
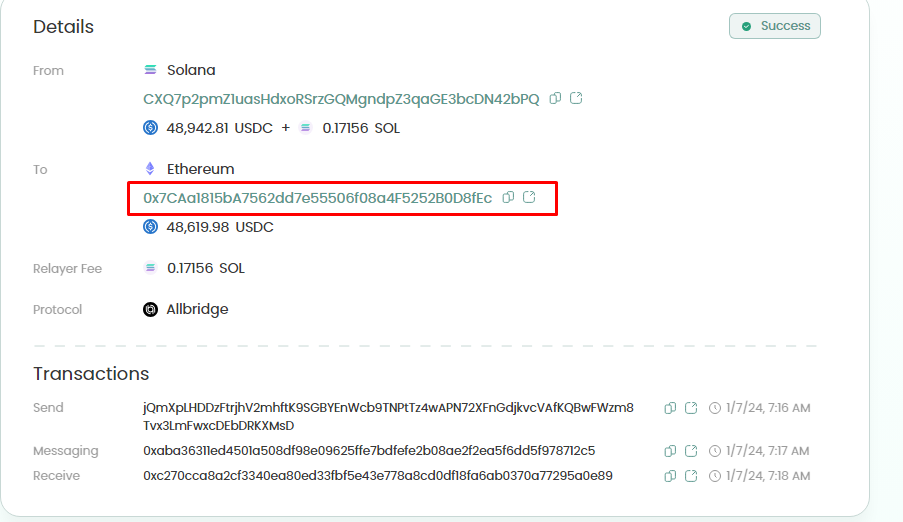
- Bridging to Ethereum via Allbridge:
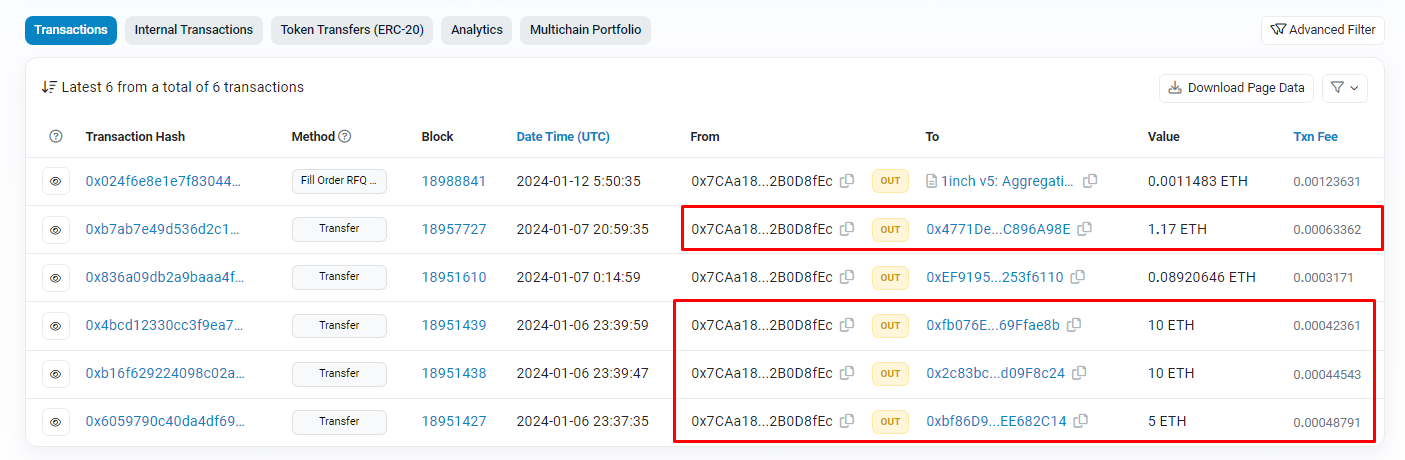
- The USDC obtained from the frontend exploit was bridged to the Ethereum network over 2 transactions using Allbridge, to the address 0x7caa1815ba7562dd7e55506f08a4f5252b0d8fec.
- Final Exchange and Deposit:
- The bridged USDC was swapped for 26 ETH. These funds were then deposited into FixedFloat (instant exchange) over several transactions, completing the laundering process for the assets stolen via the frontend exploit.
 https://etherscan.io/address/0x7caa1815ba7562dd7e55506f08a4f5252b0d8fec
https://etherscan.io/address/0x7caa1815ba7562dd7e55506f08a4f5252b0d8fec
Conclusion
The MangoFarmSOL exit scam is the largest exit scam that we have investigated in 2024. The methodology of the scam shares similar characteristics with an incident in 2023 involving a fraudulent project named Harvest Keeper. Both project’s updated their frontend which drained users funds as well as removing assets that victims had invested into the project.
The MangoFarmSOL exit scam, resulting in an estimated $1.32 million in losses, underscores the critical need for rigorous project vetting in the crypto space. CertiK addresses this issue with its KYC services, offering projects the opportunity to earn a KYC badge, signaling to investors a level of due diligence and transparency. This badge represents an essential step towards building trust within the blockchain ecosystem, encouraging engagement with projects committed to security and integrity. In a landscape where scams can significantly undermine investor confidence, CertiK's KYC process emerges as a vital tool for distinguishing legitimate projects from fraudulent ones.