
| Name | Security Score | Audits | Price / 24h % | Market Cap | Ecosystem | Category | Badge & Honor |
|---|---|---|---|---|---|---|---|
 Diamante Blockchain Diamante Blockchain | 94 .00 AAA | N/A | N/A | Infrastructure 3 | 4 | ||
 Gala Games Gala Games | 94 .73 AAA | $0.047 -0.08% | $1.4B | Gaming 7 | 4 | ||
 Undeads Undeads | 90 .93 AA | N/A | N/A | Gaming 5 | 4 | ||
 Particle Network Particle Network | 90 .71 AA | N/A | N/A | 9+ | Web3 4 | 4 | |
 WEMIX WEMIX | 94 .37 AAA | $1.7 -0.05% | $609M | Gaming 6 | 7 | ||
 Intella X Intella X | 90 .10 AA | N/A | N/A | Gaming 2 | 4 | ||
 FoxWallet FoxWallet | 86 .58 AA | N/A | N/A | 6 | Wallet | ||
 ReHold ReHold | 89 .04 AA | N/A | N/A | DeFi 2 | 3 | ||
 Cosmos Cosmos | 94 .25 AAA | $8.5 -0.04% | $3.3B | 5 | Infrastructure | ||
 Orochi Network Orochi Network | 87 .47 AA | N/A | N/A | Infrastructure 4 | |||
 ChainGPT ChainGPT | 93 .87 AA | $0.27 -0.06% | $115M | Infrastructure 3 | 6 | ||
 Particle Ink Particle Ink | 84 .14 A | N/A | N/A | Marketplace 4 | |||
 PAX Gold PAX Gold | 93 .61 AA | $2.3K -0.01% | $424M | 3 | DeFi | ||
 Tenderize Tenderize | 85 .94 A | N/A | N/A | DeFi 3 | |||
 Polygon Polygon | 93 .37 AA | $0.71 -0.05% | $7B | L2 Scaling 2 | 3 |
| Name | Security Score | Audits | Price / 24h % | Market Cap | Ecosystem | Category | Badge & Honor |
|---|---|---|---|---|---|---|---|
 Diamante Blockchain N/A | 94 .00 AAA | N/A | N/A | Infrastructure 3 | 4 | ||
 Gala Games $1.4B | 94 .73 AAA | $0.047 -0.08% | $1.4B | Gaming 7 | 4 | ||
 Undeads N/A | 90 .93 AA | N/A | N/A | Gaming 5 | 4 | ||
 Particle Network N/A | 90 .71 AA | N/A | N/A | 9+ | Web3 4 | 4 | |
 WEMIX $609M | 94 .37 AAA | $1.7 -0.05% | $609M | Gaming 6 | 7 | ||
 Intella X N/A | 90 .10 AA | N/A | N/A | Gaming 2 | 4 | ||
 FoxWallet N/A | 86 .58 AA | N/A | N/A | 6 | Wallet | ||
 ReHold N/A | 89 .04 AA | N/A | N/A | DeFi 2 | 3 | ||
 Cosmos $3.3B | 94 .25 AAA | $8.5 -0.04% | $3.3B | 5 | Infrastructure | ||
 Orochi Network N/A | 87 .47 AA | N/A | N/A | Infrastructure 4 | |||
 ChainGPT $115M | 93 .87 AA | $0.27 -0.06% | $115M | Infrastructure 3 | 6 | ||
 Particle Ink N/A | 84 .14 A | N/A | N/A | Marketplace 4 | |||
 PAX Gold $424M | 93 .61 AA | $2.3K -0.01% | $424M | 3 | DeFi | ||
 Tenderize N/A | 85 .94 A | N/A | N/A | DeFi 3 | |||
 Polygon $7B | 93 .37 AA | $0.71 -0.05% | $7B | L2 Scaling 2 | 3 |
Ethereum projects partner with CertiK for our innate understanding of the specific needs, risks, and knowledge around possible vulnerabilities that come with building on Ethereum. With a network as crucial Ethereum, the security of each Ethereum project is vital not only to the Ethereum Ecosystem, but to the staying power of the web3 space itself.
That’s why CertiK strives to secure the Ethereum network through its full range of web3 security tools, which extends beyond Ethereum smart contract audits to include essential blockchain analytics tools such as Skynet, as well contineous assessment through bug bounty programs.
Reach out to the CertiK team to take the next step in securing your project.
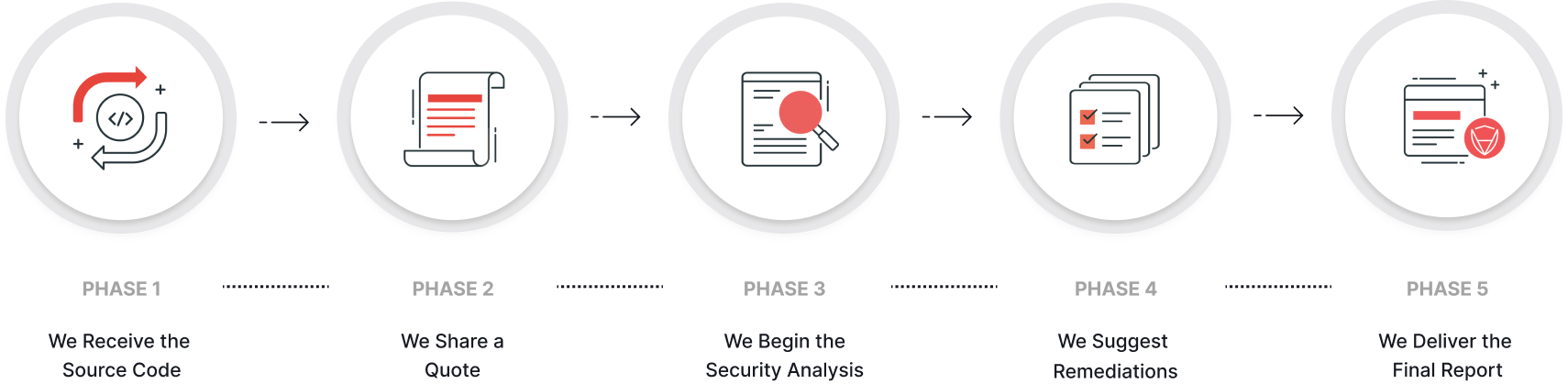
Our understanding of what's possible with Ethereum has been honed through our auditing of hundreds of Ethereum projects, which include titans in the space such as Shiba Swap, Aave, and The Sandbox. Given the diversity of the Ethereum ecosystem, providing security to each Ethereum project requires an intimate understanding of both the project's specific architecture, and also how these architectures intersect with other projects in the ecosystem.



