TL;DR
On May 15, 2022, the Space Dumpling token (SDUMP) was exploited, leading to a loss of 7.6 BNB around ~$2,000 at time of incident. The attacker took advantage of Space Dumpling anti-whale mechanism and drained funds from its liquidity pools. The attacker obfuscated the profits through Tornado Cash on June 1, 2022.
Summary
On May 15, 2022 at 9 AM UTC, Space Dumpling token (SDUMP) was exploited via flash loan attack. The attacker took advantage of SpaceDumplingToken's anti-whale mechanism and drained funds from its liquidity pools. The attacker deployer an attack contract which flash loaned WBNB which was swapped for SDUMP and transferred directly to the SDUMP-WBNB pool. Similar to Hackerdao attack vector, the attacker contract calls the skim() function and since the amount of SDUMP was a large quantity, the anti-whale mechanism triggered. The total loss was approximately 7.6 BNB which was about ~$2,000 USD at the time the profits were obfuscated via Tornado Cash.
The project itself had a stronger presence in the summer of 2021 where it was active on multiple social channels including but not limited to: Twitter, Telegram, Medium, and a website. Most of these channels have been deleted or wiped excluding their Medium page. Their GitHub and Whitepaper were also deleted. From what we can gather, the project experienced a slow death due to lack of traction. At the time of writing this article, Space Dumpling (SDUMP) has not seen strong activity on-chain since early prior to this incident in early May 2021.
This attack follows a similar pattern to that seen in the flash loan exploit which occurred on Hackerdao, which we also revisited earlier this week. The Space Dumpling attacker also attacked Musk Deer Coin, Dobecoin, Rescue Elon, ABC Token, Upstarr, and Rescue Musk using a similar attack vector.
Exploit Transactions
SDUMP-WBNB pool exploit: https://bscscan.com/tx/0xe4130dc8891a095576b2c4b89ab2f320bd310da5db5fff49c1d9a2caf1d0973f
SDUMP-BUSD pool exploit: https://bscscan.com/tx/0x6aa7f122d921ec52629339ab5309eaa50d347155f1ebc1f2d02ed215dc7a3e63
Related Addresses
Attacker: https://bscscan.com/address/0x74e878a538fde58860fd28c388599adecabe1eed
Attacker contracts
SDUMP-WBNB pool attacker contract: https://bscscan.com/address/0x038067bf7c8eeb378fe25746533635af6ed8bcfe
SDUMP-BUSD pool attacker contract: https://bscscan.com/address/0x5407719f2c2ff5fc81fee22e6691beb5e93b2658
SpaceDumplingToken contract address: https://bscscan.com/address/0x13f6751ba11337bc67abbdad638a56194ee133b8
Attacked contracts:
SDUMP-WBNB pool: https://bscscan.com/address/0x8b3c67ca3da1b389a1252af79f284d2faad07358
SDUMP-BUSD pool: https://bscscan.com/address/0x8b19bb58dbda8b5303abc96bb418e9bf4100f34b
Attack Flow
Take the exploit to SDUMP-WBNB pool as an example:
-
The attacker deployed an attacker contract and flash loaned WBNB from a flash loan provider.
-
The borrowed WBNB was swapped for SDUMP tokens through the SDUMP-WBNB pool.
-
The swapped SDUMP tokens were transferred directly to the SDUMP-WBNB pool
-
Then the attacker contract called the skim() function of the SDUMP-WBNB pool immediately to transfer the SDUMP back to the attacker contract. Since the amount of transferred SDUMP was large, Space Dumpling's anti-whale mechanism was triggered. An extra fee was applied to the transfer transaction.
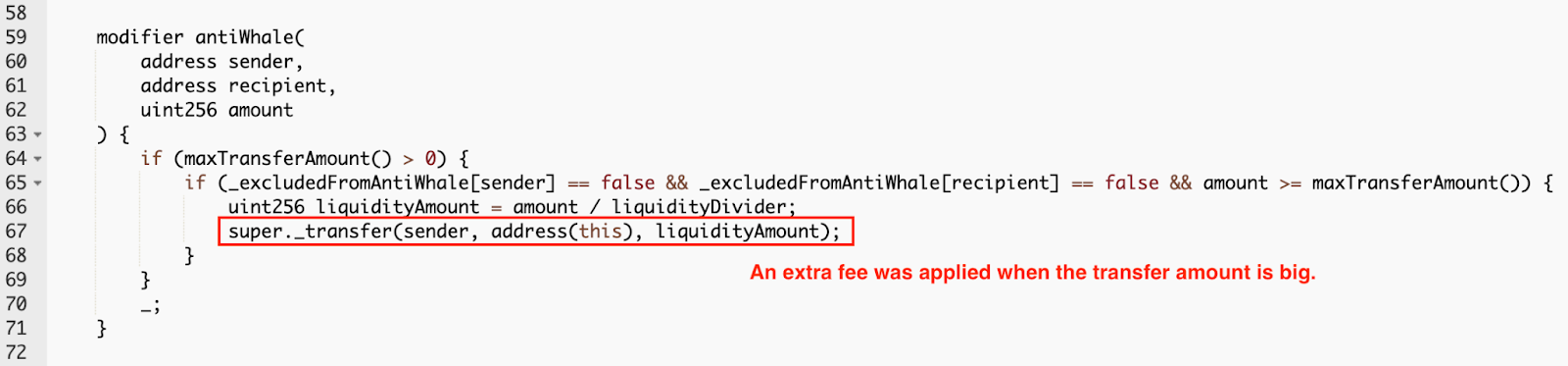 However, the anti-whale fee was not deducted from the transfer amount:
However, the anti-whale fee was not deducted from the transfer amount:
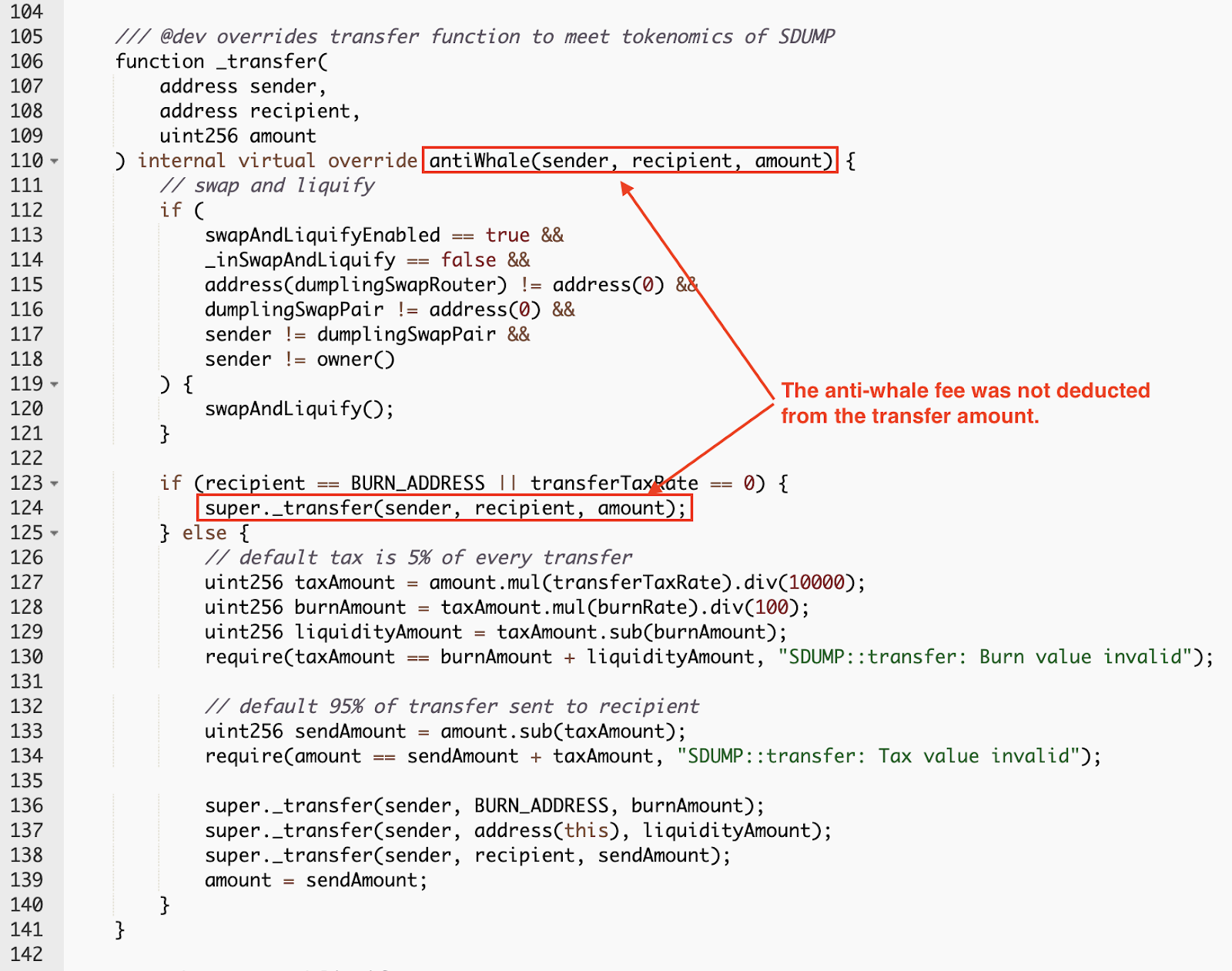 Which means if the pool wants to transfer the tokens back to the attacker contract, it has to pay more SDUMP.
Which means if the pool wants to transfer the tokens back to the attacker contract, it has to pay more SDUMP. -
The attacker contract repeated the previous two steps several times, which made the SDUMP-WBNB pool keep paying more SDUMP than it received. This process raised the price of SDUMP.
-
With the raised price, then the attacker contract swapped SDUMP back to WBNB. Because the price of SDUMP was higher than that in Step 2, the attacker contract received more WBNB than it paid in Step 2.
-
The attacker contract repaid the flash loan and sent the profit to the attacker.
Contracts Vulnerability Analysis
The Space Dumpling contract's anti-whale mechanism is the primary vulnerability. The anti-whale fee is not deducted from the transferred amount.


This mechanism could be used to drain funds from the UniswapV2Pair contract by the transfer-skim process.
Conclusion
The Space Dumpling flash loan attack represents just one of many attacks abusing the same vulnerability, many confirmed to have the same attacker and others such as Hackerdao where the attack pattern lines up perfectly. Small projects such as Space Dumpling trying to keep their feet on the ground are at constant odds with malicious actors. With contract auditing these potential vulnerabilities and pitfalls can be dissolved before crushing project momentum. In the case of Space Dumpling, the Dumpling Swap project appears to have been abandoned with all social channels down or wiped and the only paper trail left being the Medium page which was left untouched since May 18, 2021. It is tough to call where the project would have landed in the event that it was never exploited however it is evident that the exploit did factor in its growth halting days afterward.
 However, the anti-whale fee was not deducted from the transfer amount:
However, the anti-whale fee was not deducted from the transfer amount:
 Which means if the pool wants to transfer the tokens back to the attacker contract, it has to pay more SDUMP.
Which means if the pool wants to transfer the tokens back to the attacker contract, it has to pay more SDUMP.


