
TL;DR
We have seen plenty of hacks on social media this year, over 440 NFT Discords hacks, Bored Ape Yacht Club Instagram hack, Beeple’s Twitter compromised to name a few. However, on 03 July 2022 we saw an unlikely victim to NFT phishing attacks - the British Army. Both the British Army’s Twitter and Youtube were compromised with posts of NFT projects and their YouTube account posting fake Cathie Wood and Elon Musk livestreams.
Event Summary
At around 5:00 PM UTC, the British Army’s official Twitter and Youtube accounts were compromised leading to the posting of two NFT projects. The Chair of the House Defence Committee, an organization that is responsible for examining the administration of the UK armed forces tweeted that “this looks serious”.
So let's break down how the attack took place. Firstly, the hackers changed the headers of the British Army’s Twitter handle to “pssssd” and had a link to @tmw_buidls, the creator of PossessedNFT project.
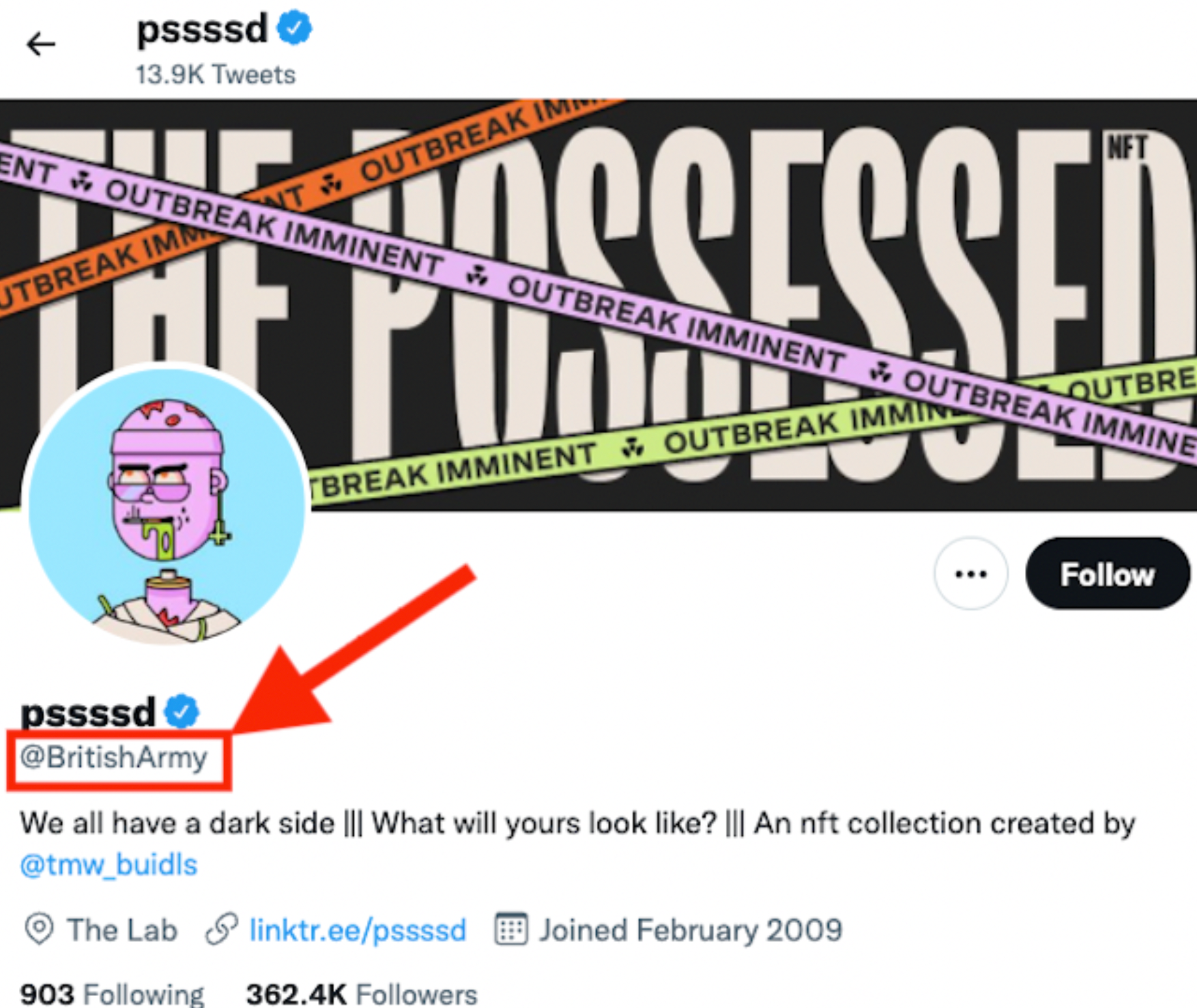
It is highly unlikely that the PossessedNFT founder, or project members in an official capacity had anything to do with this breach. This is due to @tmw_buidls announcing on his Twitter account warning people of the breach, as well as encouraging people to report it. Furthermore, the attackers then changed the British Army Twitter handle to another unrelated project.
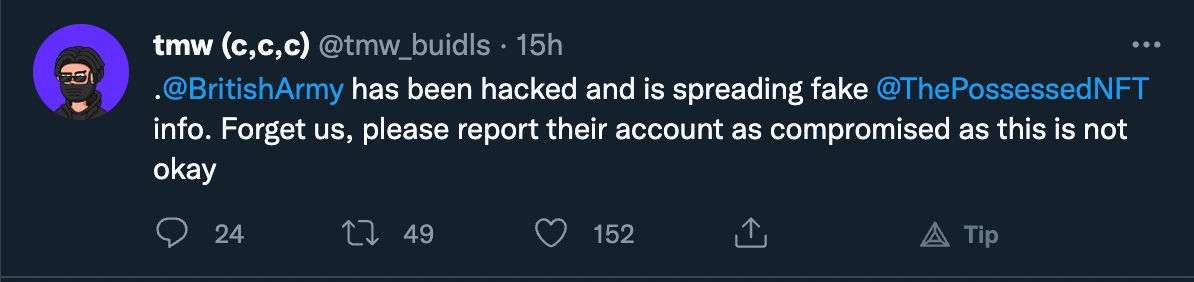
The Twitter handle for the British Army changed to Bapesclan, an NFT project that is run by ChainTech Labs.
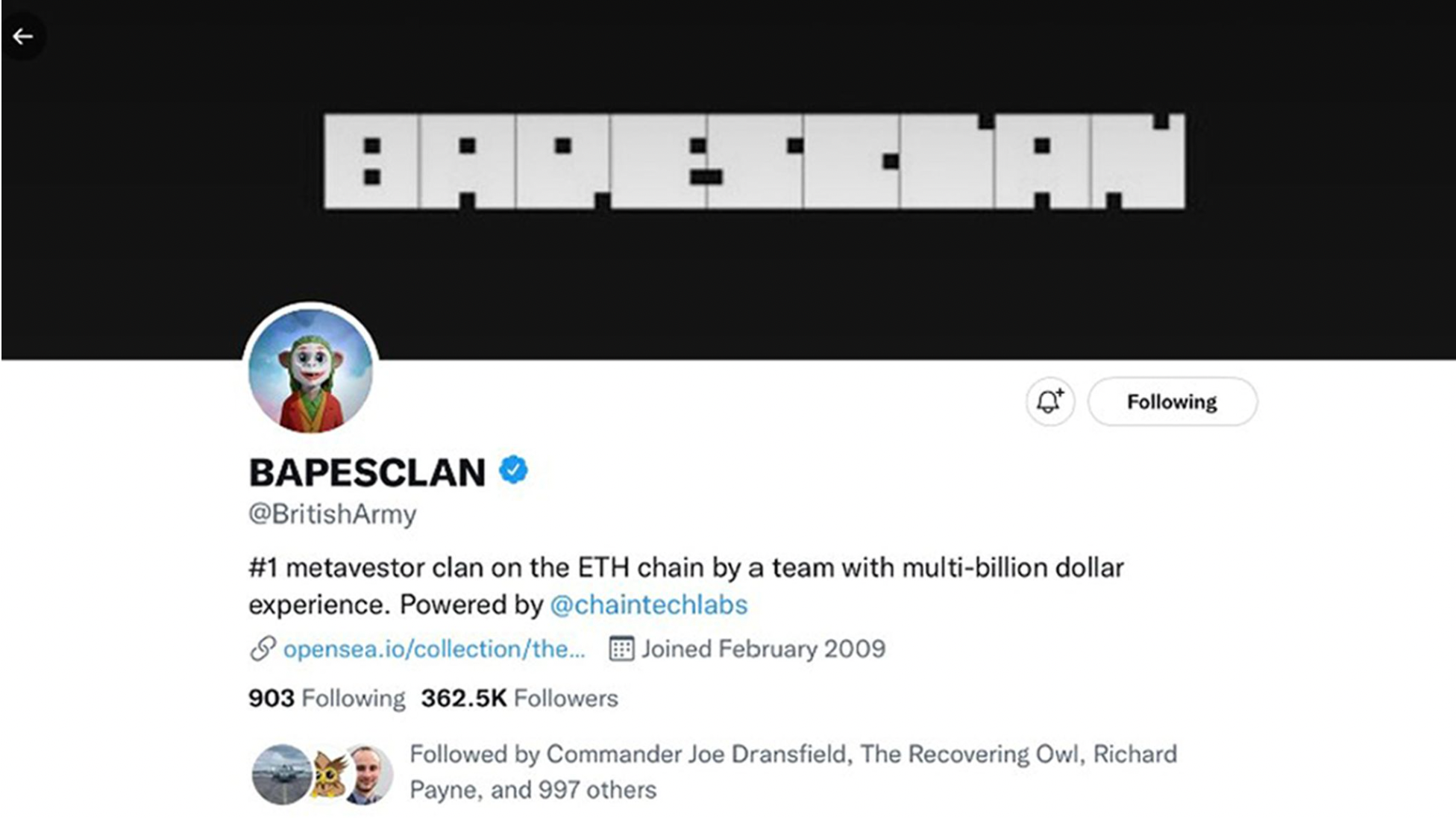
Like with the previous example, it is highly unlikely that the project was involved in the Twitter compromise, although no announcement has surfaced from the team. Furthermore, the hackers retweeted posts from @TFGmykL, who is a “Bapesclan ambassador” in what was likely an attempt to make the compromised account appear to behave as the legitimate Bapesclan account. The hackers also posted a link to OpenSea.
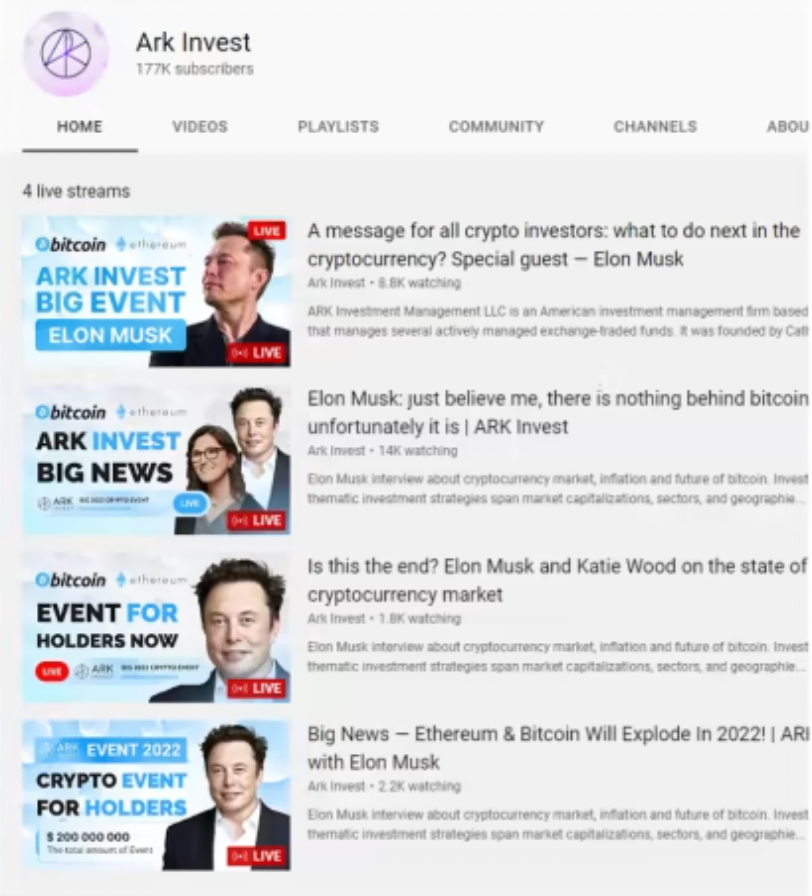
In addition to the Twitter compromise, the British Army YouTube account was also breached. Instead of posting NFT projects, the logo was changed to Ark Investments, an investment management fund run by Cathie Wood. Videos were posted with titles such as “Ethereum & Bitcoin will explode in 2022! | Ark Investment with Elon Musk”. The two individuals are popular personalities for crypto scammers to impersonate with a deep fake video of Elon Musk promoting a scam being an example. In addition, an old video of Elon Musk and Cathie Wood has been used to promote crypto giveaway scams.
Regaining Control
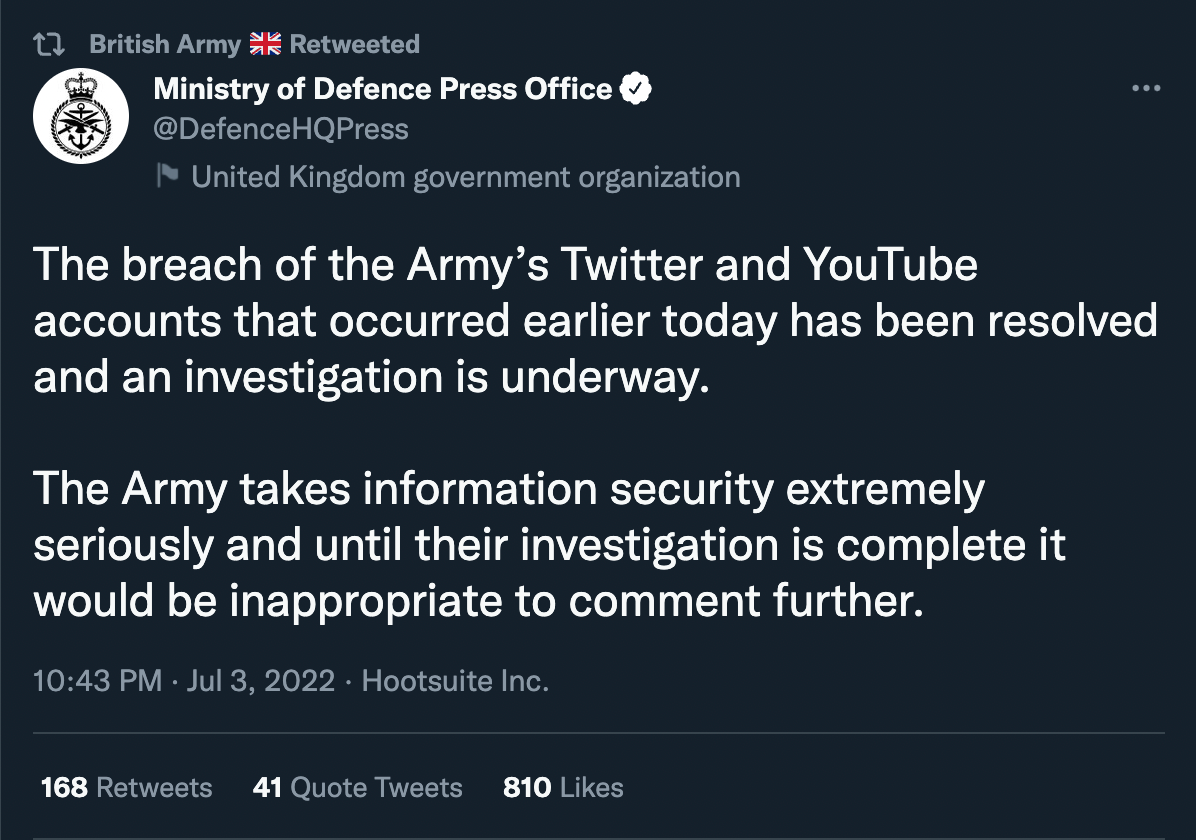
At 08:09 PM UTC, the British Army regained control of their Twitter account and tweeted “Apologies for the temporary interruption to our feed. We will conduct a full investigation and learn from this incident”. In addition, the Ministry of Defence Press Office tweeted that the breach has been resolved and it would be inappropriate to comment until the investigation has concluded.
It’s highly likely that the other branches of the British Armed Forces are frantically reviewing their information security practices to prevent another such attack, as well as other government bodies. If recent international events weren’t an excuse, a successful attack surely would be.
How Much Was Lost?
It can be extremely difficult to determine the amount lost in a phishing attack that has occurred. In this case, there are a few clues that we can point to see what, if any, funds were stolen. When looking at the first instant, instead of posting a link directly to OpenSea, the attackers posted a Linktree URL which appears to be the official PossessedNFT linktree. However, when we search for “The Possessed NFT” we see three fake pages with the same profile image as seen on the compromised British Army Twitter handle, all of which have zero trading volume.
When the British Army’s Twitter posted Bapesclan content, they provided a link to OpenSea. Along with the official Bapesclan OpenSea page, there are three other pages with the title “The Bapesclan Genesis” and an additional page named “The Bapesclan”. Since we assess that ChainTech Labs were not responsible for the breach we can rule out the official page. All of these other projects have zero trading volume.
Therefore it is likely, that no funds were actually stolen from the Twitter compromise, and the primary purpose of the hack is likely to embarrass the British Army.
Conclusion
Most phishing attacks in Web3 typically look to profit off unwitting investors by taking over accounts that are closely associated with the target project. An example of this is Bored Ape Yacht Club discord hack posting malicious links to websites in order to steal Bored Ape and Otherside NFTs. In this case, the British Army has nothing to do with the Web3 industry, and those who follow the account are not doing so to make profits in the crypto space. It is more likely that the purpose of this attack is to embarrass the British Army and UK Government.
This attack does demonstrate how vulnerable Web2 applications are to hacks. We have seen 443 Discord hacks this year alone, as well as high profile compromises such as Beeple’s twitter account. Malicious actors in the Web3 space will continue to exploit these vulnerabilities to profit off investors. Nevertheless, we advise that all organizations ensure that they have robust 2FA, and for individuals to double check a URL before clicking on a site.



