
TL;DR
On 4 January, 2023 we observed the first major exit scam of the year. The scam resulted in a loss of approximately $2.6 million and was attributable to the deployer of FUT. The FUT deployer withdrew approximately 67 million FCS tokens from MasterChef contract which they swapped for FUT tokens. The FUT deployer then swapped the FUT tokens for around $2.6 million USDT (Tether).
Summary
At approximately 10:45 AM +UTC, the FUT token dropped roughly 99% on the FCS/FUT liquidity pool. At roughly the same time, the FUT/USDT liquidity pool slipped by ~84%. Upon investigation, drops in the price of FUT on both liquidity pools were due to the deployer for FUT selling off tokens. Specifically the deployer received FCS from 0x1bb99 which they swapped for FUT, and ultimately swapped for USDT. The FUT deployer transferred the USDT to 0xbdb95 where the funds reside at the time of writing.
0xC0476 created the FUT and FCS tokens and no social media accounts have been identified.
Exit Scam Flow
- On 28 October 2022, ownership of the MasterChef contract (0xFD59), which the FUT deployer created, is set to 0x1bb99. On 14 November, 2022 the FUT deployer (0xC0476) transferred 0.1 BNB (Binance Coin) to 0x1bb99 to cover gas fees.
 Image: 0xC0476 transfers 0.1 BNB to a newly created wallet 0x1bb99. Source: BscScan
Image: 0xC0476 transfers 0.1 BNB to a newly created wallet 0x1bb99. Source: BscScan
-
0x1bb99 calls the set() function from MasterChef contract and they set the pool’s Sushi reward allocation point of FCS/FUT to 45.
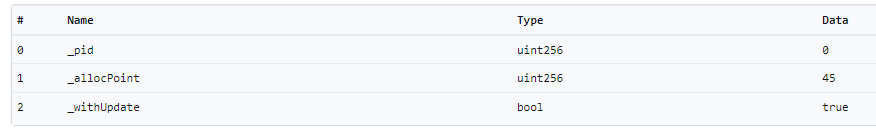 Image: 0x1bb99 calls the set() function from MasterChef contract (0xFD59). Source: BscScan
Image: 0x1bb99 calls the set() function from MasterChef contract (0xFD59). Source: BscScan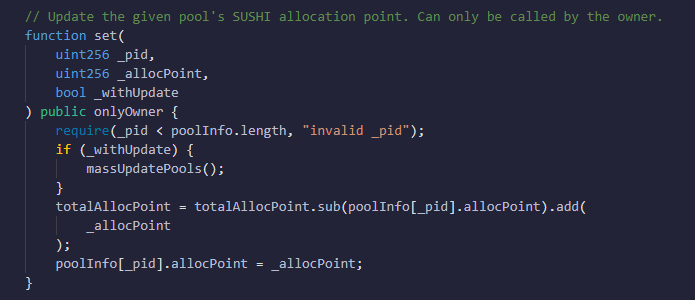 Image: set() function from MasterChef contract (0xFD59). Source: BscScan
Image: set() function from MasterChef contract (0xFD59). Source: BscScan -
On 4 January, 2023 0x1bb99 calls withdrawSushiReward() from the MasterChef contract. This function call transfers 67,293,513 FCS to the FUT deployer.
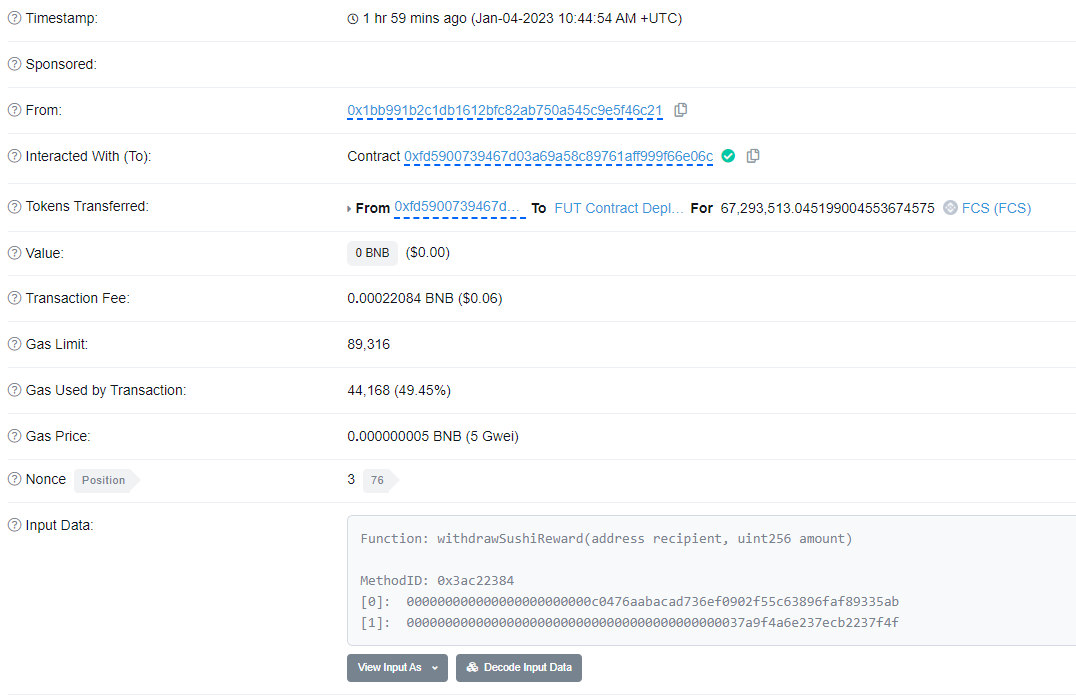 Image: 0x1bb99 calls withdrawSushiReward() and receives FCS. Source: BscScan
Image: 0x1bb99 calls withdrawSushiReward() and receives FCS. Source: BscScan -
The FUT deployer swaps FCS to FUT. In total, the deployer, swaps approximately 46 million FUT for around 7,025 FCS. This caused a 99% slippage in the FCS/FUT pool.
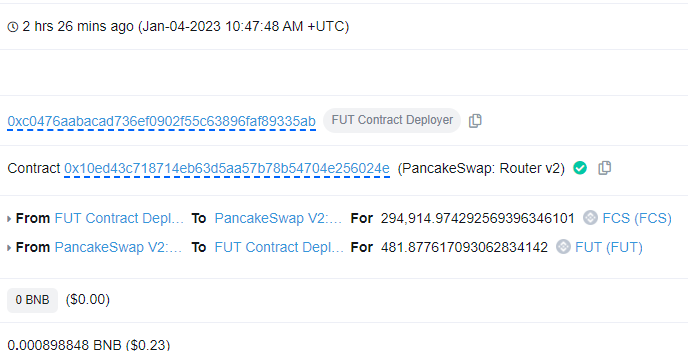 Image: Example of the FUT deployer swapping FCS for FUT. Source: BscScan
Image: Example of the FUT deployer swapping FCS for FUT. Source: BscScan -
The FUT deployer simultaneously swaps FUT for USDT. The deployer gains $2,590,662 USDT which they transfer to EOA 0xbdb95. The FUT/USDT swaps caused an 84% slippage in the respective pool.
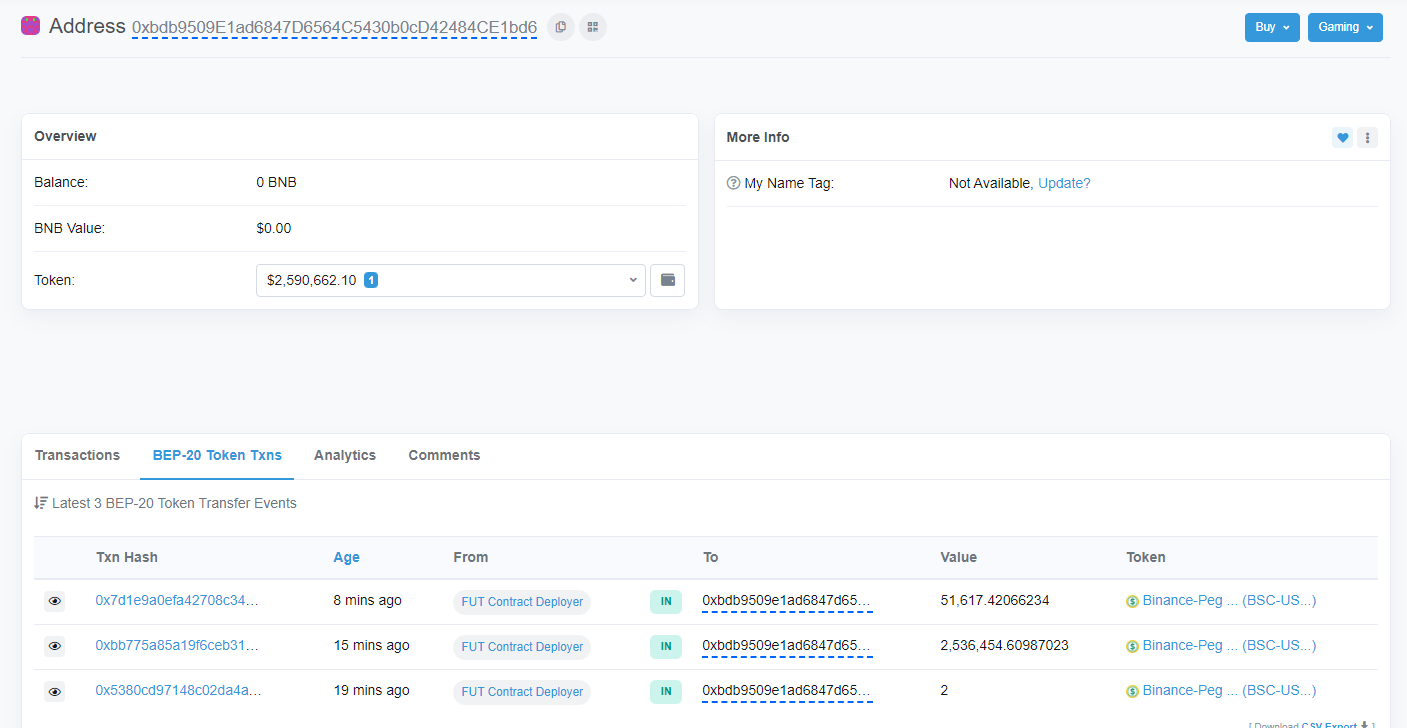 Image: The FUT deployer transfers USDT from the FUT swaps to EOA 0xbdb95. Source: BscScan
Image: The FUT deployer transfers USDT from the FUT swaps to EOA 0xbdb95. Source: BscScan
Transferring Ownership
This particular incident started when the deployer of FUT (0xC0476) transferred ownership of the Master Chef contract from themselves to 0x1bb99. Contracts can either have central ownership whereby an address is likely able to perform privileged functions, or have ownership renounced which typically demonstrates that the contract is decentralized. An owner can also transfer ownership to a new address which was the first step in the FUT incident. While this is not necessarily a malicious act on its own, it can indicate malicious behavior such as a private key compromise. If a contract has an owner address then the ownership can be transferred. If you are invested in a project and you see that the owner of the project has been changed, you should look for any announcements to understand why this has taken place.
Conclusion
Projects such as FCS and FUT were likely scam projects from the onset. Transparency is key in the Web3 space, and a lack of presence on social media means that investors cannot be sure who exactly is behind the project. This means that the overall intentions of those behind the project cannot be fully understood and leaves you at risk of exit scams such as this. Head over to certik.com and search for projects with comprehensive audits and are KYC verified. Furthermore, if you suspect a project of malicious behavior, you can reach out to CertiK’s 24/7 incident response team who will investigate the project for malicious activity.
 Image: 0x1bb99 calls the set() function from MasterChef contract (0xFD59). Source:
Image: 0x1bb99 calls the set() function from MasterChef contract (0xFD59). Source:  Image: set() function from MasterChef contract (0xFD59). Source:
Image: set() function from MasterChef contract (0xFD59). Source:  Image: 0x1bb99 calls withdrawSushiReward() and receives FCS. Source:
Image: 0x1bb99 calls withdrawSushiReward() and receives FCS. Source:  Image: Example of the FUT deployer swapping FCS for FUT. Source:
Image: Example of the FUT deployer swapping FCS for FUT. Source:  Image: The FUT deployer transfers USDT from the FUT swaps to EOA 0xbdb95. Source:
Image: The FUT deployer transfers USDT from the FUT swaps to EOA 0xbdb95. Source: 


