
TL:DR
On May 10, 2022, the project OWNLY experienced an exploit to the "Stake-to-Own Mustachio Marauder NFT" staking contract. A total of 930M OWN tokens were drained during the attack which were then exchanged for roughly 115 BNB worth approximately ~$37K through a pair transaction.
Summary
On May 10, 2022 at 8:15:26 PM +UTC, the OWN staking contract was exploited. The attacker drained all OWN tokens from the staking contract, and subsequently sold the OWN tokens for about 50 WBNB. The attacker deployed a contract which utilized a critical bug in the OWN token staking contract to repeatedly stake OWN tokens and unstake twice the amount until the OWN token balance in the staking contract was drained.
OWNLY announced the incident the day of the attack. In this announcement, OWNLY apologizes and prepared reimbursement OWN tokens for stakers who lost tokens. Soon afterward 15,000,000 OWN was airdropped to all stakers in the Stake-to-Own Mustachio Marauder NFT program. The next day OWNLY tweeted an official recount of the events that happened the day prior. In this recount, they describe the attack vector as being the unstake function not checking the user’s claim status, allowing the attacker to use the unstake function to claim OWN tokens until the contract was drained.
Following the incident, OWNLY has stayed on track as a project and has not let it stop momentum of the project. They announced more smart contract auditing to avoid similar cases and at time of writing are an active project across social channels and project deadlines.
Attack Flow
-
The attack contract utilized a critical bug in the OWN token staking contract to repeatedly stake a certain amount of OWN tokens and unstake twice that amount. This is repeated until the OWN token balance in the staking contract is drained.
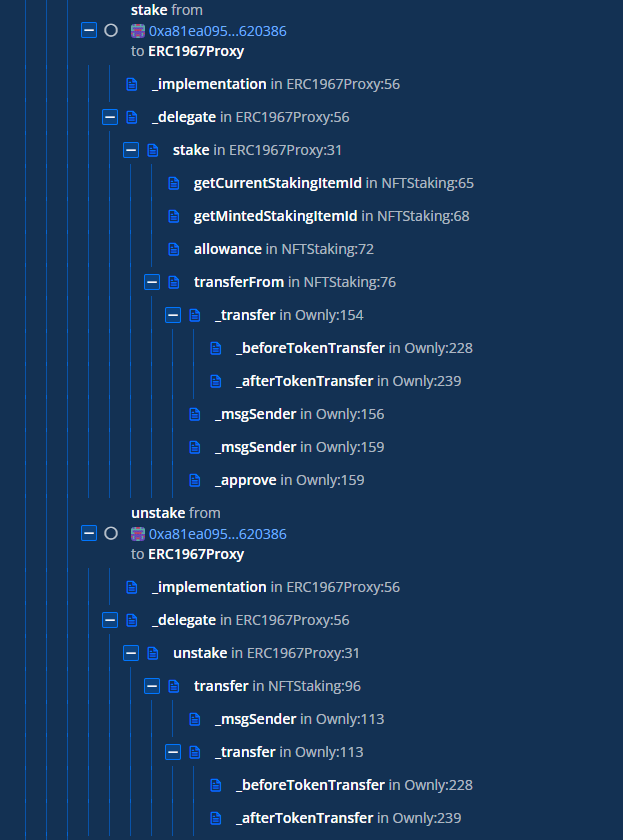
-
Then the attack contract swapped the OWN tokens to WBNB and sent the BNB to the attacker address
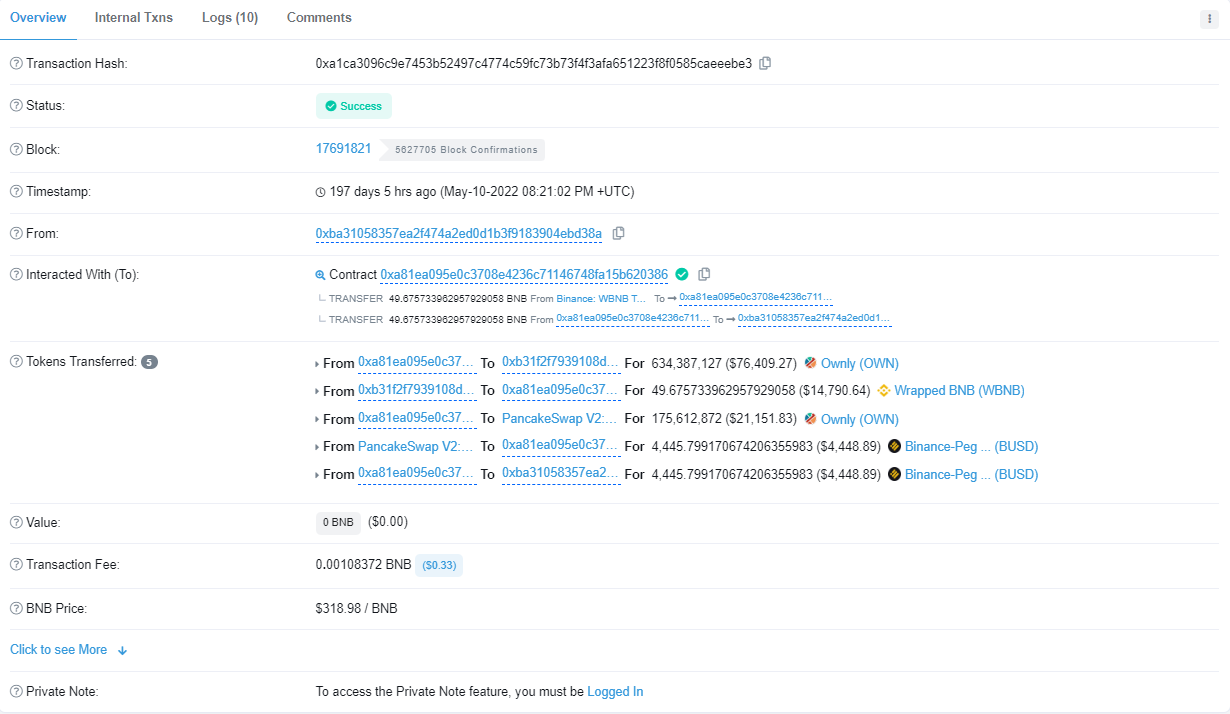
Exploit Transaction
Attack transaction: https://bscscan.com/tx/0x2cbe47edb040c710b7f139cbea7a4bced4d6a0d6c5aa4380f445880437ea072f
Relevant Addresses
Project website that shows the staking contract https://stake.ownly.market/own-marauder
Staking contract proxy contract:: https://bscscan.com/address/0x421f30419D6c1D7573C1F57546A631f2f89D7E92#code
Staking contract implementation contract: https://bscscan.com/address/0x41bf7f818f2dc41c67932e63e87c86d05ab957e8#code
Attacker address: https://bscscan.com/address/0xba31058357ea2f474a2ed0d1b3f9183904ebd38a
Attack contract address: https://bscscan.com/address/0xa81ea095e0c3708e4236c71146748fa15b620386
Contracts Vulnerability Analysis
The staking contract contains a critical error, allowing for a staker to unstake unlimited amount of time, draining tokens from the contract
Specifically, the unstake() function (shown below) does not check if a staker has unstaked already, and/or update the staking amount of the caller, allowing any staker to unstake unlimited number of times, up to the total staking balance of the contract

Conclusion
The OWNLY incident as a whole represents how strong development and community driven projects can help persevere through turbulence of web3 development. The losses to the project were a set back but OWNLY has continued building their projects and keeping momentum, a hopeful beacon for the ecosystem. However, if the project had smart contract auditing for the vulnerable staking contract, the entire incident would have been prevented and the 115 BNB (~$37K) loss would have been entirely negated. Smart contract auditing is the life blood to preventing substantial losses due to contract vulnerability, mitigate loss today and get audited!





