
Summary
On 7 February, 2023 CertiK detected a slippage on the LianGo Protocol’s token (LGT) that dropped 97%. Upon investigation, CertiK discovered that the LGT tokens originated from the LGT Pool contract. Changes were made to the liquidity pool (LP) token address in the LGT Pool contract leading to the conclusion that this incident was likely caused by a private key compromise.
At 03:32:45 PM +UTC on 07 February 2023, the LP token contract was changed from 0x611f7… to 0x621fe… by the owner of the LGT contract. 0x621fe… is a malicious contract that was deployed on 07 Jan 2023 by contract 0xf877C…, which was in turn deployed by the exploiter (0x36d17...)
On 7 February, 2023 at 03:32:27 PM +UTC externally owned account (EOA) 0x36d17… initiated a transaction which drained the LGT pool contract. In total, 6,148,859.35 LGT was transferred out of the LGT pool and into 0x36d17. From there, the LGT was swapped for $1,628,168.69 and was transferred to 0xcb65d. The attack was made possible due to a change in the LGT Pool’s LP token address, which was set to 0x621fe… and was controlled by the exploiter.
 Image: LGT Exploit Transaction. Source: BscScan
Image: LGT Exploit Transaction. Source: BscScan
Since the incident, multiple EOAs have tried to withdraw tokens from the LGT pool contract, but have been reverted due to a complete drainage of funds.
 Image: Failed withdraw transactions on LGT contract. Source: BscScan.
Image: Failed withdraw transactions on LGT contract. Source: BscScan.
Private Key Compromises In 2023
This incident was likely the fifth private key compromise we have seen in 2023 bringing the total lost to such compromises at $9.2 million so far. However, the incident on LianGo appears to be the first incident where a compromised wallet has led to losses for a protocol that exceed $1 million, whereas the other private key incidents appear to be individual investors losing control of their wallet and as a consequence, their funds. In 2022, private key compromises resulted in the loss of over $1.5 billion, and the incident on LianGo demonstrates how devastating these events can be for protocols. Unfortunately, we’re highly likely to see future incidents where millions of dollars are lost to private key compromises.
Attack Flow
This incident can be broken down into a preparation stage and an attack stage.
Preparation Stage
- On 07 Feb 2023 at 03:32:18 PM +UTC the LGT pool owner (0xb5950…) added a malicious pool 0xf84f5… (pid=3 ) with the fake LP token 0x621fe… in transaction 0x29c29. -The fake LP token is controlled by the attacker, therefore allowing the attacker to have unlimited amount of the fake LP tokens.
- At 03:32:21 PM +UTC the attacker then created contract 0x80d36… and deposited 614,885,935,211,982,505,426,257,800,000,000 fake LP tokens to the pid=3 pool in transaction 0xa4b5b. The transferFrom in the fake LP token will always succeed and return true. Therefore, the attacker can deposit any amount amount of fake LP tokens.
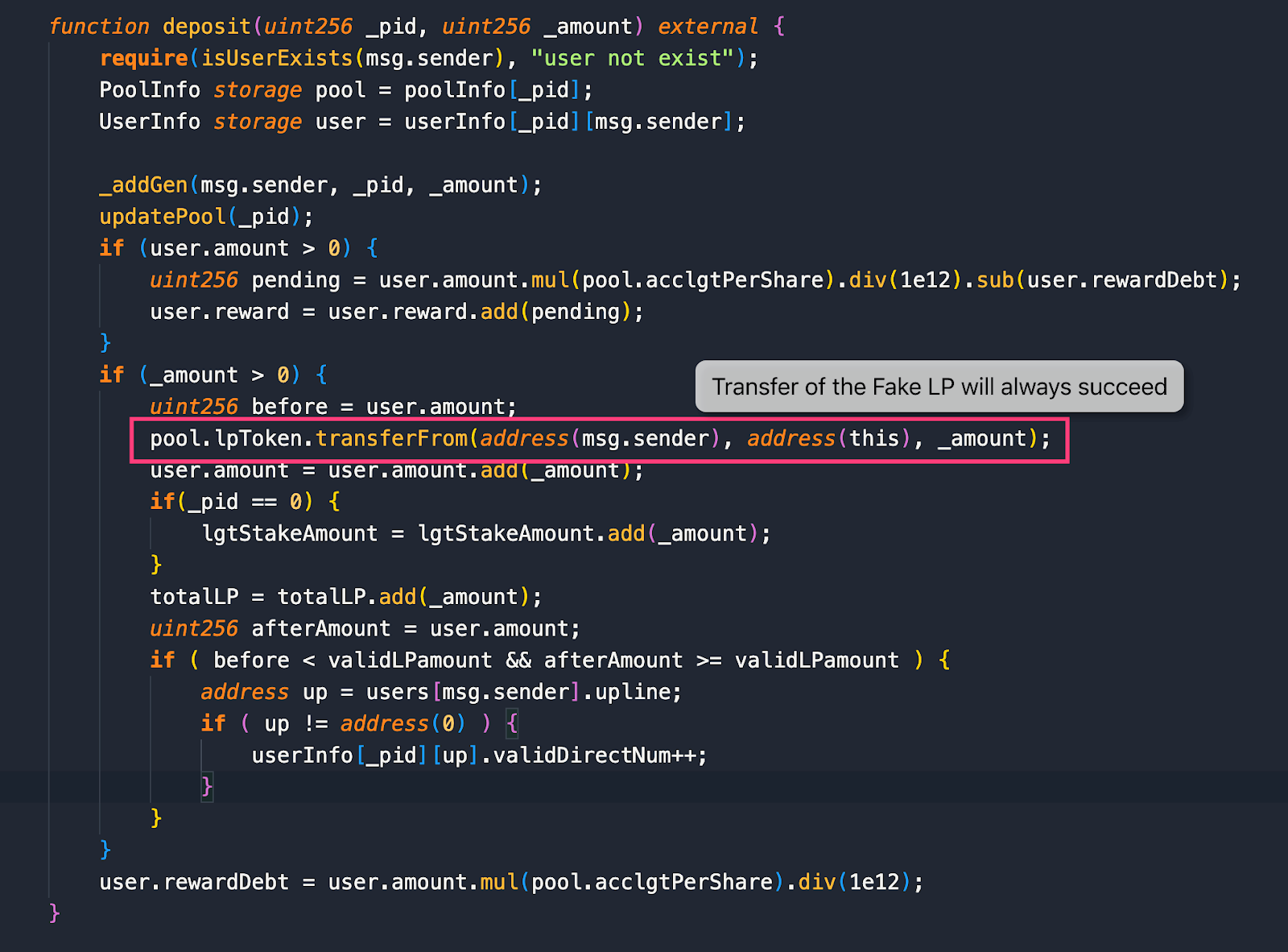 Image: Depositing LP tokens will always result in success. Source: CertiK.
Image: Depositing LP tokens will always result in success. Source: CertiK.
Attack Stage
- At 3:32:27 PM + UTC the attacker minted 137,513,751,375,137,500,000,000 fake LP tokens to the LGT pool to increase the balance of the fake LP token supply.
- With the reward contract updated, the attacker called the withdraw function to drain all the LGT tokens within the contract.
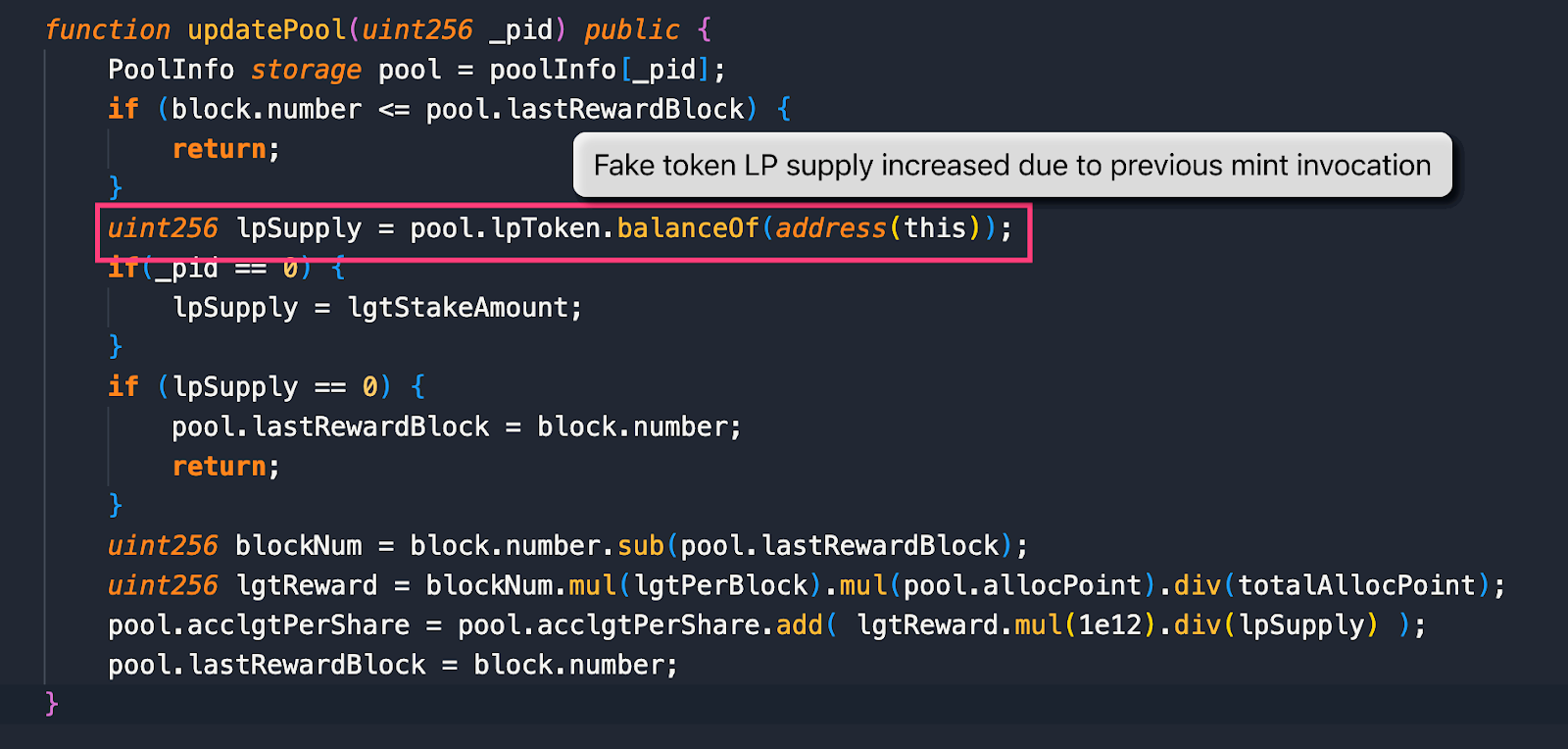 Image: LP Supply increased due to mint. Source: CertiK.
Image: LP Supply increased due to mint. Source: CertiK. - Finally, the attacker swapped all the LGT tokens to BSC-USD using PancakeSwap.
Asset Tracing
At the time of writing, $1,628,168.69 million has been taken so far and remain in wallet 0xCb65d… which was funded by Tornado Cash on 11 Dec 2022 at 09:00:26 PM + UTC.
 Image: Tornado Cash fund. Source: BscScan.
Image: Tornado Cash fund. Source: BscScan.
Conclusion
Evidence points to this exploit being fundamentally caused by a private key compromise on the LGT Pool owner address. This incident points to the broad issue of centralization within smart contracts because the likely compromise of this EOA led to the loss of approximately $1.6 million from the LGT Pool contract. An audit from CertiK can point out centralization issues which we consider to be a major security risk. You can view the protocols that CertiK has audited and check to see if the project you are researching has any centralization risks, and what they’ve done to mitigate such findings by visiting CertiK.com.
 Image: Depositing LP tokens will always result in success. Source: CertiK.
Image: Depositing LP tokens will always result in success. Source: CertiK. Image: LP Supply increased due to mint. Source: CertiK.
Image: LP Supply increased due to mint. Source: CertiK.


