
TL:DR
In this post we look back on the Pragma Money incident which occurred on May 08, 2022 amounting to the loss of approximately ~$3M (1,048.1 ETH and 400,000 DAI). An attacker was able to manipulate the project’s oracle allowing them to borrow a number of different tokens with inflated collateral and swap them thereafter.
Event Summary
On May-08-2022 at 08:34:42 PM +UTC, Fortress Loans was victim of an oracle manipulation and a DAO manipulation attack. 1,048.1 ETH ($2,575,799) & 400,000 DAI ($400,205 USD) were taken and bridged from BSC to ETH and later sent to Tornado Cash. Approximately ~$2,976,004 USD was stolen.
At around 4:30 PM EST Fortress (FTS) suffered a massive drop in their token price. Shortly after, comments on their telegram channel indicated that the team was investigating an incident. At 10:05 PM EST JetFuel Finance made an official announcement about the oracle manipulation and posted links to suspected address and transaction.
However, this attack seems like it possibly started much earlier. The attacker first began to interact with Fortress on Apr-19-2022 05:41:59 PM +UTC and even deployed an unverified custom contract that interacted with Fortress well in advance of the contract the attacker created on May-08-2022 08:31:03 PM +UTC. The attacker was potentially “casing the joint” by running through a series of transactions, interacting with Fortress, and deploying unverified contracts over several weeks that ended a couple days prior to the exploit.
After the attacker deployed their contract they kicked off a series of transactions that allowed them to create and fund an externally owned address to propose to Fortress Governor Alpha contract a malicious proposal that they then voted on themselves (since they had previously manipulated the price, they were able to easily purchase enough FTS – 400k for the necessary votes) to set the FTS token collateral high enough to make FTS extremely valuable. The attacker then borrowed large amounts of a number of other tokens and swapped them into ETH and DAI.
The contract that the attacker deployed had a “self-destruct” clause that was triggered by the attacker once the malicious transactions were complete.
The funds were moved after swapping across the cBridge(Celer Network) bridge and Multichain swap bridge to Ethereum chain and sent to Tornado cash in a series of subsequent transactions.
CertiK detected the movement of funds to Tornado cash with their alerting system. The attacker was also funded via Tornado cash. This vulnerability could have been detected through a comprehensive audit.
Attacker Addresses & Exploit Transactions
Exploit txs : 0x13d19
Other Relevant Addresses
Attacker Address: 0xA6AF2 Attacker Contract(Highly likely) - self destruct: 0xcd337 FortressPriceOracle: 0x00fcf Chain contract: 0xc11b6
Attack Flow
- Attacker created and funded an EoA(0x0db3b) to propose to Fortress Governor Alpha contract (0xe79ecd), and the proposal ID is 11. Proposal 11: 0x12bea
- The attacker then voted this proposal: 0x83a4f
- Proposal 11 is thus executed to add FTS token collateral to 700000000000000000, which allows the attacker to utilize it to make profits in the following steps.
- Attacker also manipulated the oracle by calling
submit()function in the chain smart contract, where therequiredSignaturescan be bypassed and power check is disabled in the deployment. - Attacker then provided the 100 FTS as collateral through attack contract 0xcd337 and borrowed huge amounts of other tokens as return. 0x13d19
- The attacker converted borrowed tokens to ETH and DAI, and deposited them to Tornado Cash.
Contracts Vulnerability
Vulnerability 1
The first vulnerability is a design flaw in the governance contract design. The governance contract can execute succeeded proposal to modify the lending related configuration (i.e., adding a collateral and its corresponding collateral factor).
However, to successfully execute the proposal, the minimum FTS token that is required to vote is 400,000. As the price of the FTS token was low, the attacker swap ~11 ETH for over 400,000 FTS tokens.
With over 400,000 FTS tokens, the attacker can create a malicious proposal and successfully execute it.
Vulnerability 2
The second vulnerability is the “submit” function of the chain contract has a flaw that allows anyone to update the price.
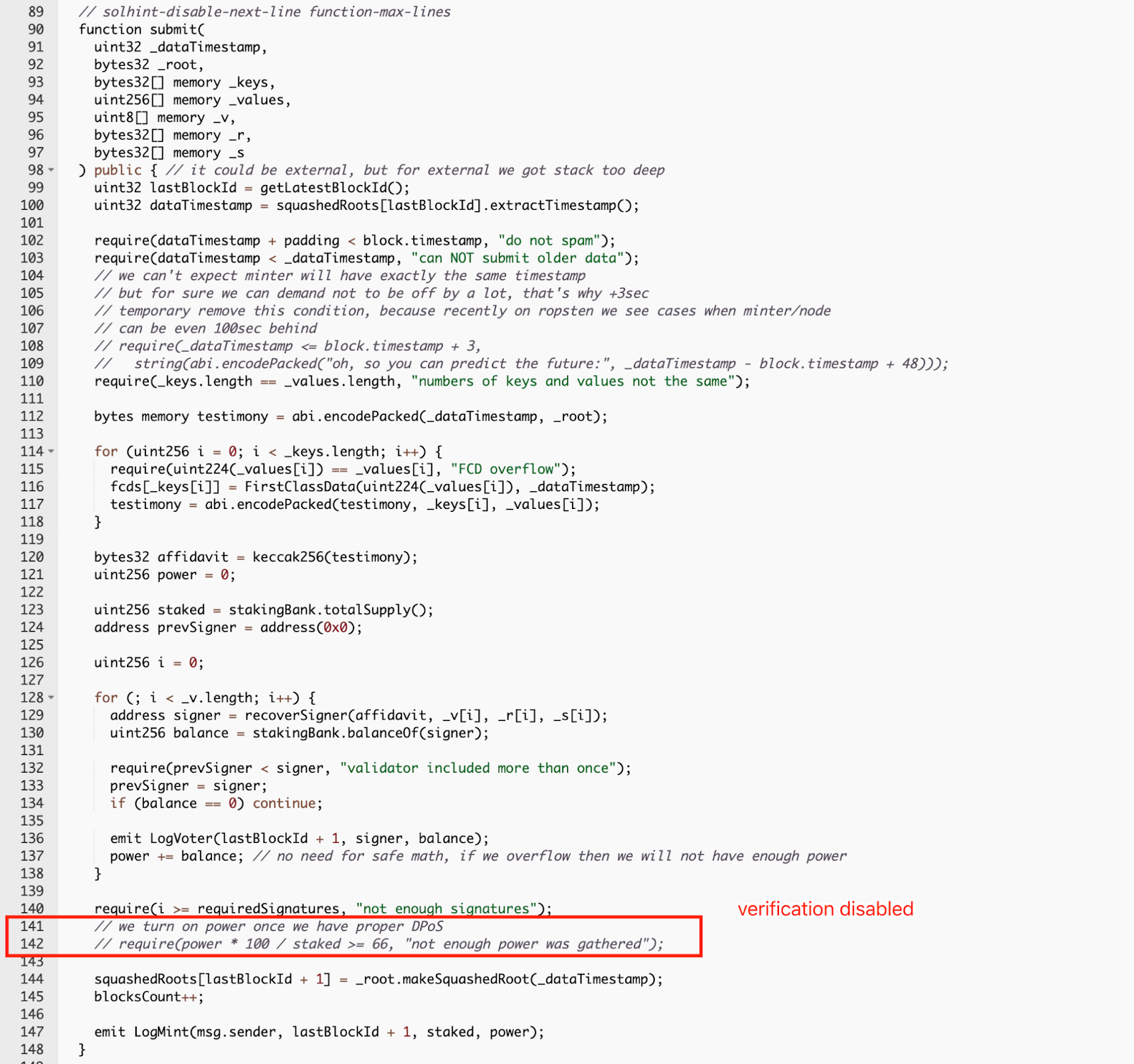
The required statement in L142 was commented out. Therefore, there is no verification to ensure the function call is triggered properly.
Would we spot the issue during the audit?
Yes. For the first vulnerability, as the price of the governance token and how many governance tokens will be in circulation are unknown, it is very difficult to spot this issue. However, we would write a finding to warn of the potential governance attack.
For the second issue, we can spot that the critical verification is missing and anyone can manipulate the price via the submit function.
Conclusion
This incident highlights the need for smart contract auditing as both vulnerabilities stem from the contract itself. These vulnerabilities enabled the attacker to manipulate the project’s pricing oracle allowing them to borrow a number of different tokens with inflated collateral and swap them, thus leading to the drain. CertiK smart contract auditing has been carefully built to detect vulnerabilities such as the aforementioned. Issues like these found in the Fortress Loans contract would be corrected and brought to the project’s attention. Get audited today!



