
TL;DR
On July 28th, 2022, Nirvana Finance was exploited via a flash loan attack with the attacker profiting ~$3,574,635. The stolen funds have been bridged from the Solana network to Ethereum wallet 0xb9a.
Introduction
On July 28th, 2022, adaptive yield protocol Nirvana Finance was exploited via a flash loan attack forcing the protocol’s $ANA token price to collapse ~85%. Nirvana Finance is an adaptive yield platform that utilizes the $ANA token to generate wealth through an adaptive yield, with a built-in rising floor price. The attack happened on decentralized lending platform Solend where the hacker proceeded to borrow amounts USDT and USDC tokens leveraging ANA as collateral. According to Nirvana Finance’s post-mortem, the attack caused a loss of over ~10M in assets.
Attack Flow
The exploit resulted in inaccurate pricing for the $ANA token. The attacker manipulated inputs to the program, then was able to buy the token at an artificially low price. Since the act of purchasing $ANA from Nirvana Finances's native AMM pushes the price upward, the hacker was then able to sell their $ANA for a high price, making a profit.
- The attacker executed the flash loan which netted ~$3,574,635 USDT.
- The attacker borrowed $10,250,000 USDC from the Solend Protocol and used it to buy $ANA. The attacker then manipulates the price of $ANA from $8 to $24 by calling the Buy 3 command in the contract.
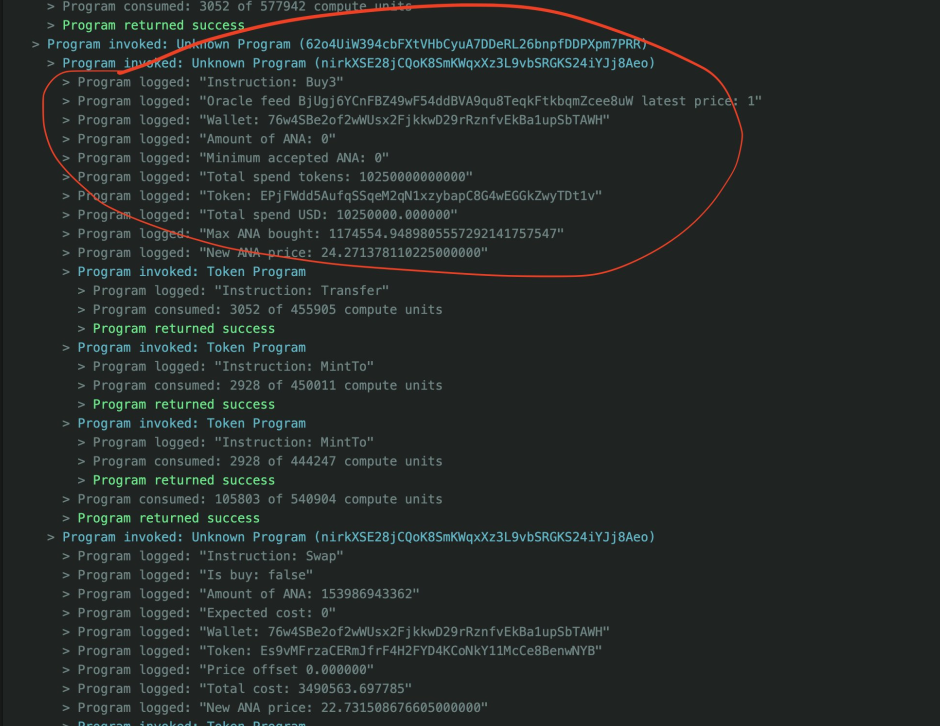
- With the inflated price they then swapped the $ANA for ~$3,490,563 USDT from the Nirvana treasury and the rest back to USDC.
- The attacker was able to repay the $10,250,000 USDC flash loan to the Solend Protocol and retained the rest.
- The attacker converted the full USDT amount into USDCet, transferring the funds into an ETH account (0xB9AE2624Ab08661F010185d72Dd506E199E67C09) through Wormhole.
Exploit Transactions
The execution flow can be clearly found in the program log: Solana transaction details | Solscan
Conversion of USDC to USDCet: Solana transaction details | Solscan
Exit transaction: https://etherscan.io/address/0xb9ae2624ab08661f010185d72dd506e199e67c09
Addresses
Attacker account: 76w4SBe2of2wWUsx2FjkkwD29rRznfvEkBa1upSbTAWH
Nirvana Finance Treasury : CxuuSEv67PzNkMxqCvHeDUr6HKaadoz8NhTfxbQSJnaG
Solend Main Pool Vault: DdZR6zRFiUt4S5mg7AV1uKB2z1f1WzcNYCaTEEWPAuby
_ : 9RuqAN42PTUi9ya59k9suGATrkqzvb9gk2QABJtQzGP5
Program: nirkXSE28jCQoK8SmKWqxXz3L9vbSRGKS24iYJj8Aeo
Profit and Assets Tracing
At the time of exploit the net profit of the attack was approximately $3,547,873.25.
Profit from the exploit is bridged to Ethereum: https://etherscan.io/tx/0xb5a89c01da58ec7ec8a4b0d0361d8f1719966d4deceaa01efc1362601a76339c
Conclusion
At 9:00 PM UTC on July 28th, 2022, Nirvana Finance tweets on behalf of the Nirvana Finance community, that the exploiter return funds that have been taken from their treasury. Nirvana Finance then continues the thread by claiming that they are offering a white hat bounty of $300,000 and a cessation of investigation.

On July 31st, 2022, Nirvana Finance released an official statement on their Medium page regarding the incident. Since the attack, Nirvana Finance claims to have fixed the exploit in the code and flagged wallets involved. Additionally, Nirvana Finance has traced the originating wallet back to Huobi and is currently working with their team to identify the individual responsible. At time of writing, the thread remains pinned and the stolen funds still remain in Ethereum wallet 0xb9a.




