
TL;DR
New Free DAO experienced a malicious flashloan attack where the attacker exploited a vulnerability resulting in the loss of $1.25m. We have identified that the attacker was involved in another malicious flashloan exploit on $N3DR, resulting in the loss of 930.1 WBNB worth ~$296.9k at the time.
Summary
On Sep-08-2022 02:09:25 AM +UTC, CertiK’s Skynet detected a flashloan attack in progress on the BSC blockchain. New Free Dao ($NFD) experienced a flashloan exploit for a profit of ~$1.25M USD (4,481 BNB). 2,081.07 BNB remains in the attacker’s wallet along with 557,224.06 USDT. The token’s price has plummeted over 99% as a result of the attacker dumping a total of 6,838,792 NFD tokens.
The malicious actor took advantage of a vulnerability inside the unverified rewards contract which we have confirmed after decompiling the code.
An Overview of the Attack Flow
-
First, the attacker wallet deployed a malicious contract. In that same transaction, it called the following function, making itself a member of the contract.
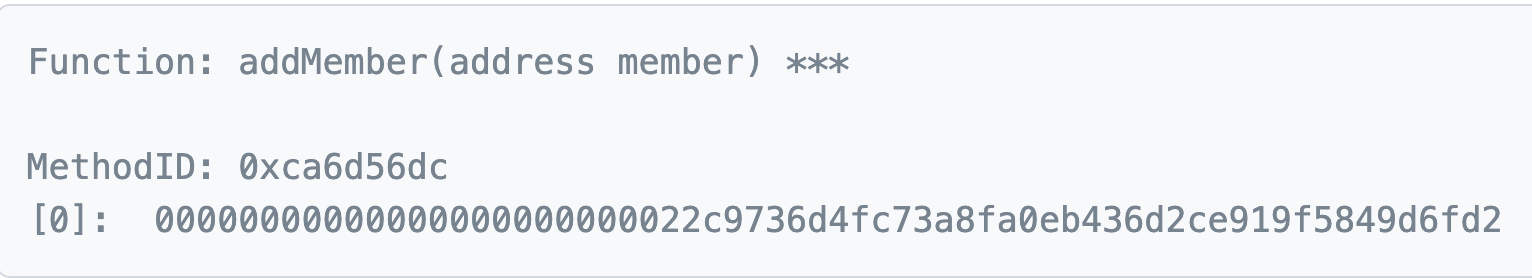
-
The attacker then initiated the first of three flashloans, borrowing 250 WBNB then swapping it for 6,313,508 NFD tokens.
-
They then sent these tokens to an unverified NFD contract.
-
This invoked 0xe2f9d09c with the input as the NFD token address 0x00000000000000000000000038c63a5d3f206314107a7a9fe8cbba29d629d4f9.
-
This triggered another unverified rewarding contract deployed by NFD.
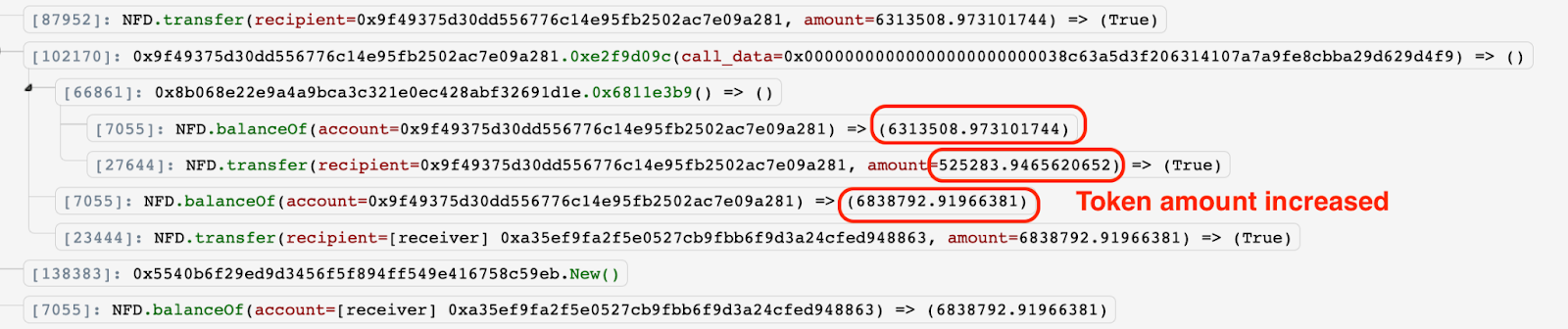
-
The NFD contract erroneously released 525, 283 NFD in the above transaction.
-
By the time the attacker was done, they had taken 343,323,371 NFD tokens, for a profit of 4,481 WBNB after repaying the initial 250 WBNB loan.
-
They then swapped 2,000 WBNB for 556,556.72 USDT in two transactions. The wallet still holds 2,481 WBNB.
-
The NFD deployer (who is also the unverified contract deployer withdrew 37M NFD in this transaction: https://bscscan.com/tx/0xec2cc6bcf82880501a26d64e2efc0a2e7fe4ad4df38563d4769bf740c650730e The deployer then converted the NDF to USDT via PancakeSwap. Only 6.5k NFD remains in the reward contract at time of writing.
Vulnerability
The vulnerability lies in the unverified rewarding contract deployed by the NFD project. After investigating the bytecode of the vulnerable contract, the root cause is the function 0x6811e3b9 shown in the following code snippet.

From the code implementation, there are two main factors that will affect the reward:
- Time interval : the longer time deposit, the more reward can have
- User token balance : more token user holds, more reward user can have
However, there is no guardrail preventing flashloans, meaning an attacker can increase his token balance significantly via flashloan.
Additionally, in L169, the user’s reward start time will be initialized as “store_6”, cause “block.tmestamp - store_6” being a non-zero value. Therefore, with the help of the flashloan, the attacker is able to amplify the reward by borrowing tokens and increase the reward significantly.
Exploit Transactions
https://bscscan.com/tx/0x1fea385acf7ff046d928d4041db017e1d7ead66727ce7aacb3296b9d485d4a26
https://bscscan.com/tx/0xb6f9b5ef1feeadb379a2de8f79bb04dd6920bfb214136d057eed4ce23a0003f8
https://bscscan.com/tx/0x8b77d75efa185295b09bdf2edcb509541fdde40ed5484212331ceac41b2f4ac0
Profit Tracing
The stolen funds were sent to EOA: bsc 0x22C9… with 400 BNB being deposited into Tornado Cash

At the time of writing, ~2,081.07 BNB and 557,113.28 BSC-USD remain in the exploiters wallet. In total this amounts to 1.13m in the attackers wallet with $111,544 being deposited into Tornado Cash.
Conclusion
Due to the recent sanctions by OFAC on Tornado Cash, it is likely that we’ll see the stolen funds make their way through the mixer at a slower pace. Due to the regulatory action by OFAC, a dramatic decrease in transactions has been observed going through the mixer.

Large increases in unique transactions without an increase in unique address could likely give clues as to what wallet redeems the funds on the other end. Needless to say, CertiK’s highly skilled and motivated analysts will continue to monitor the situation.
Furthermore, this attack shows how vulnerable an unsecured protocol is to a flashloan attack. Unverified smart contracts make it extremely difficult in identifying critical vulnerabilities. Before deploying or after verifying the smart contract, audits can be undertaken to identify code susceptible to exploits. CertiK offers industry leading smart contract audits and penetration testing; additionally subscribers to CertiK Skynet are monitored for suspicious flashloans 24/7. By utilizing our services, projects can mitigate the risk of catastrophic exploits impacting their protocol.
Our analysis has been updated to reflect additional analysis after decompiling the bytecode.





