
TL;DR
On June 23, 2022 there was a bridge exploit on Harmony’s Horizon bridge amounting to the loss of approximately $97M. According to Harmony’s official announcement on Twitter, the exploit has not affected Harmony’s One Token ($ONE). The assets, roughly $97M in value, are still being held in the exploiter address.
Incident Summary
On June 23, 2022 at 11:06:46 AM +UTC, the bridge between Harmony chain and Ethereum experienced multiple exploits. Our expert analysis has identified twelve attack transactions and three attack addresses. Across these transactions the attacker netted various tokens on the bridge including ETH, USDC, WBTC, USDT, DAI, BUSD, AAG, FXS, SUSHI, AAVE, WETH, and FRAX. The transactions vary in value but range from $49,178 to upwards of $41,200,000. The attacker accomplished this by somehow controlling the owner of the MultiSigWallet to call the confirmTransaction() directly to transfer large amounts of tokens from the bridge on Harmony, which led to a total loss around $97M worth of asset on the Harmony chain which the attacker has consolidated into one main address.
About Harmony
Harmony is an open and fast layer-1 blockchain offering a two-way Ethereum bridge powered by the Harmony One token (ONE). One of Harmony's keys to providing security is sharding and Effective Proof of Stake. The Harmony sharding splits the network into four sections that work in parallel. The Effective Proof of Stake encourages decentralization of validators while sharding shares the network's load among users. The network was launched in 2019 and features trustless cross-chain bridges and four shards, which process transactions in parallel. The Harmony bridge on Ethereum secured ~$330m worth of tokens prior to the exploit.
Attack Flow
We will take the first exploit transaction with 13,100 ETH as an example.
-
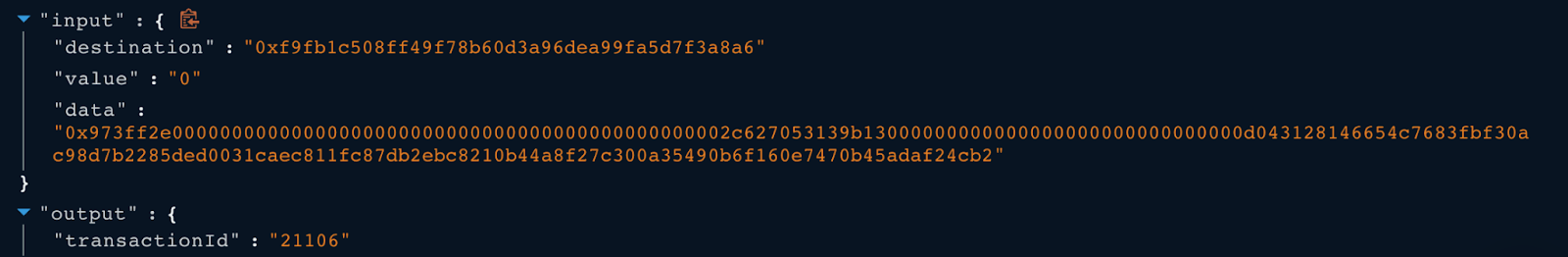
The owner of the MultiSigWallet contract called the submitTransaction() function to submit a transaction with the following payload to generate the transaction id 21106 in the transaction.
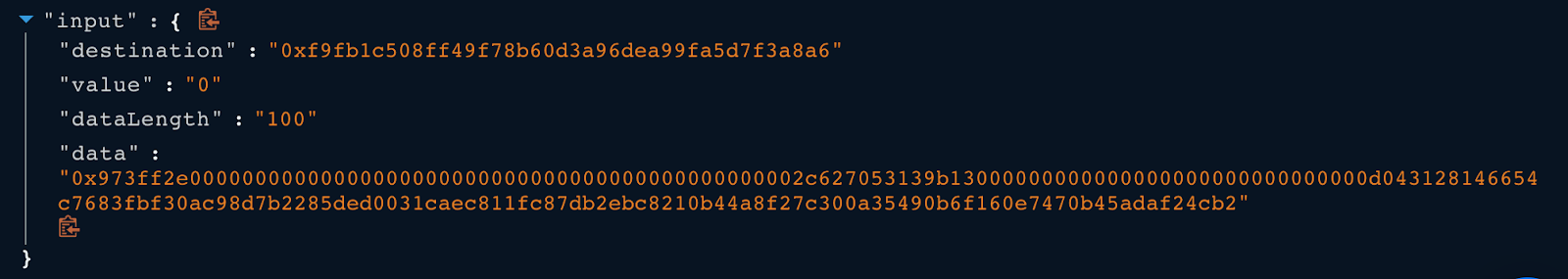
-
To confirm the transaction, the caller must be an owner.
-
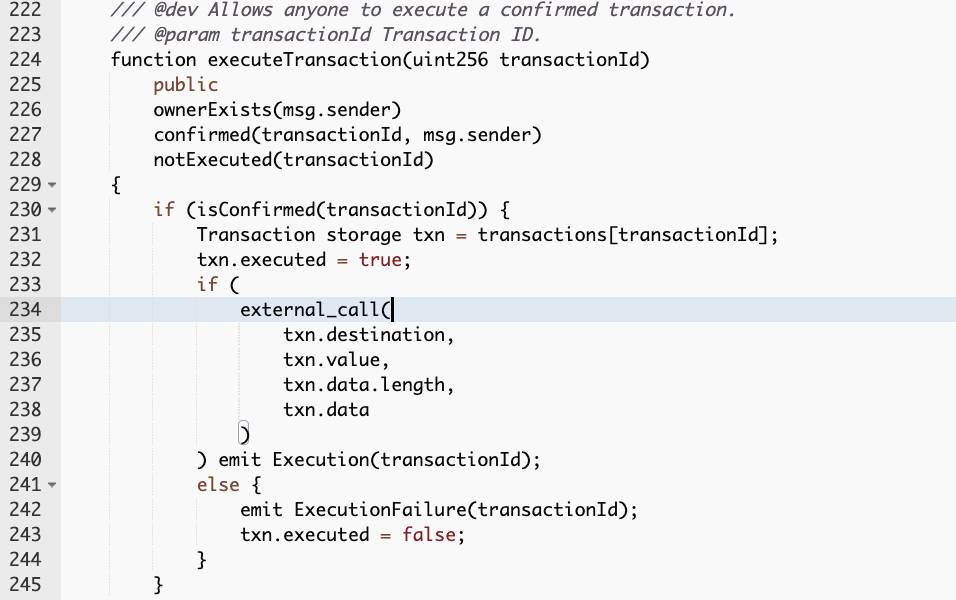
Next, in the exploit transaction, the owner of the MultiSigWallet contract called function confirmTransaction() from the MultiSigWallet with the input transactionId 21106.
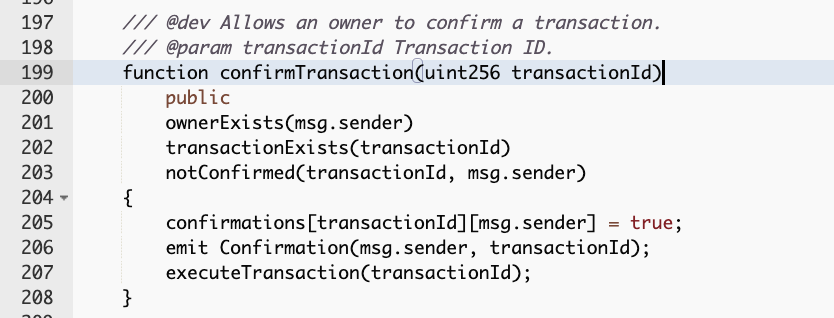
-
To successfully execute the transaction, the caller must be the owner.
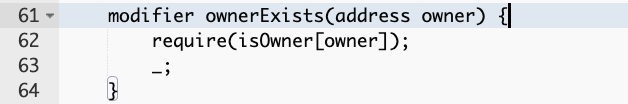
-
The executeTransaction() function invoked an external call with input data that will triggered the unlockEth() function on the Ethmanager contract.
-
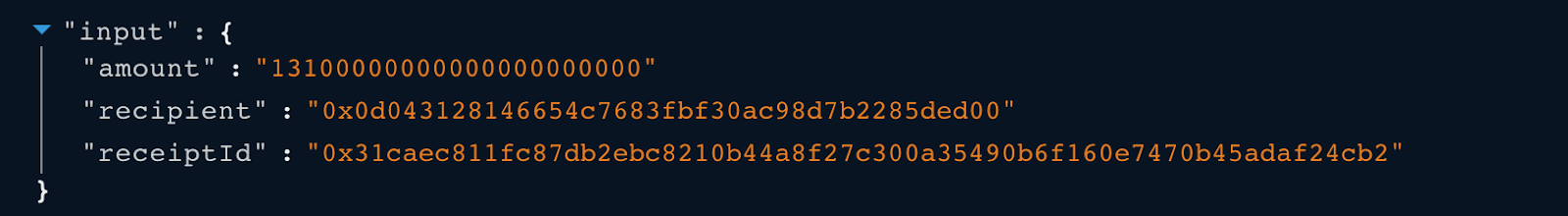
The input data specifies the amount, recipient and the receiptId which will be passed to the unlockEth() function.
-
Since the attacker somehow controlled the owner’s authority, the attacker was able to execute the transaction with id 21106, which transferred 13,100 ETH to the attacker’s address.
-
The attacker repeated the previous process using different transaction ids on other ERC20Manager contracts to transfer a huge amount of ERC20 tokens and stablecoins.
Conclusion
This is yet another major cross chain bridge exploit, earlier this year we had both the Ronin Bridge Exploit and Wormhole Exploit, showing again the need for more decentralization, full scope auditing, pen testing and red-teaming around all aspects of defi protocols. If these private keys were exploited through phishing or other social engineering methods, these attack surfaces and weaknesses also need to be tested when dealing with sums of these amounts, for coming into compliance with regulatory bodies, and building more trust for the evolving Web3 trustless ecosystem.
Reference
https://cointelegraph.com/news/wormhole-hack-illustrates-danger-of-defi-cross-chain-bridges
https://coingeek.com/axie-infinity-ronin-bridge-hacked-for-over-600m-in-eth-and-usdc/










