
TL;DR
On 06 October 2021, MyFarmPet was hit by a malicious flashloan attack which profited 31k BUSD and 100 BNB ($22k) being deposited into Tornado Cash.
Summary
On October 6 2021, a flashloan attack was executed against MyFarmPet, profiting 31k BUSD. The pricing mechanism, PancakeSwap’s MyFarmPet-BUSD pool, used by both the MyFarmPet Marketplace V2 and V3, was exploited using the loan.
The attacker used an attacking contract with a flashloan to exploit the pricing arbitrage between MyFarmPet’s marketplace V2 and V3 using the ChickenFood token. 340k BUSD was swapped for 22k MyFarmPet tokens. 1k MyFarmPet tokens were then used to buy 70k ChickenFood on MyFarmPet Marketplace V2.
The contract then swapped the remaining 21k MyFarmPet tokens to 337k BUSD, increasing the amount of MyFarmPet tokens in the PancakeSwap MyFarmPet-BUSD pool. The 70k ChickenFood tokens were then sold on MyFarmPet V3 for 46k MyFarmPet tokens, which were then swapped for 34k BUSD. After repaying the 340k BUSD loan, the attacker exited with 31k BUSD. The attacker repeated the attack almost immediately, profiting 129 BUSD the second attempt. The funds exited through Tornado Cash.
Addresses:
0x27d6e... (attacker)
noted multiple deposits to Tornado Cash, one valued 100 BNB
0x412e4 (contract)
Following the attack, there was a subsequent attempt using the same contract which only gained $129.98:
Attack Transaction Flow
- Contract gains(flashloan) 340k BUSD from PancakeSwap WBNB-BUSD pool
- Swap all BUSD for 22k MyFarmPet tokens using PancakeSwap MyFarmPet-BUSD pool
- Contract uses 1k MyFarmPet to purchase 70k ChickenFood token on MyFarmPet Marketplace V2, calling function buyFarmTokens()
- Contract swaps 21k MyFarmPet to 337k BUSD using PancakeSwap MyFarmPet-BUSD pool
- pricing mechanism now affected, MyFarmPet tokens in pool increased, price decreased.
- Contract sells 70k ChickenFood tokens for 46k MyFarmPet tokens on MyFarmPet Marketplace V3, calling sellFarmTokens()
- Contract swaps 46k MyFarmPet tokens to 34k BUSD using PancakeSwap MyFarmPet-BUSD pool
- Return loaned amount 340k BUSD to PancakeSwap WBNB-BUSD pool
- Profit gained by attacker is $31,408.94 in BUSD
Contracts Vulnerability Analysis
Call:
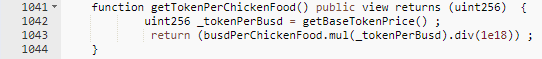
Pricing Mechanism:
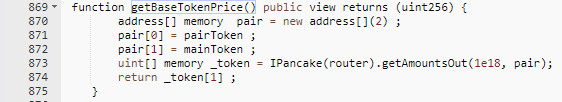
The pricing for the tokens were determined using the amount of MyFarmPet token in the PancakeSwap Pair. This was then multiplied by the recorded price of ChickenFood token. The flashloan was able to increase the MyFarmPet token amount in the pool, which was returned when quoted for a price. This had an affect on the multiplication during the price calculation. This was the same code used for both buying and selling.
Profit and assets tracing
- 31,410.278372393430140659 BUSD was profited
- BUSD profit was swapped to WBNB, withdrawn from contract as BNB, and then transferred to Tornado Cash
Conclusion
Flashloan attacks are a combination of low-risk, low-cost, and high-reward tactics from the standpoint of a criminal. These attacks have been growing in frequency and size since early 2020. Hackers discover new flaws every week before they’re patched. Developers can only cope with this situation by searching for solutions before they are attacked. MyFarmPet’s attack is just one of many flashloan attacks that have happened in 2021. A CertiK audit helps a secure a project from this attack type.



