
Alongside a significant rise in the prominence of phishing scams, we have seen some fraudsters mimicking CertiK. As a leading security organization we would be remiss if we didn’t take the time to warn you about these targeted campaigns so please take a minute while we show you how to detect and protect against these emails.
What Is Phishing?
Phishing is a type of social engineering attack which is often used to steal any type of user data. An attacker sends an email or other message to an unsuspecting victim, pretending to be someone they are not. These messages contain a link, attachment, or contact details for the victim to engage with. A successful phishing attack can result in the victim having their funds taken or their identity used as part of a wider campaign of fraud. To learn more about the different types of phishing attacks see our post What Is a Phishing Attack.
Popular Targets For Phishing
Projects and organizations often have to deal with malicious actors impersonating employees or project members in the Web3 space. This is particularly the case with Discord phishing attacks that target the NFT community.
In these attacks, a trusted account is compromised and then posts a phishing link into the server’s announcements channel leading to the theft of stolen NFTs. Prominent examples this year include the Beeple and JRNYclub Twitter hack, as well as the Bored Ape Yacht Club Discord exploit that stole 32 NFTs from community members.
CertiK analysts have tracked at least 811 incidents in 2022 leading to significant losses.
Email Phishing
Your role in identifying these attacks is crucial, whether it be to your personal online security or the representation of the company you work for. It’s important for the security of your personal information and the security of all systems that you have access to – e.g. company intranets – to be able to identify the common signs of a potential phishing attack. Treating all emails that link you to external sites, especially unsolicited offers and invitations, with caution is the best way to avoid falling victim to a phishing attack.
Here is a real example of an unsolicited scam email from a fraudster masquerading as CertiK.

This fraudulent email displays a number of the hallmarks characteristic of a phishing email:
- The email is not from an official CertiK domain. All official CertiK emails are from @certik.com or @certik.org. Other variants such as @certik.live are not genuine. In most cases, you can check the domain with the official website the sender is claiming to be from. Subtle differences may be applied to hide this, such as turning certik.com into certlk.com - note the I is now an L.
- In the same vein as checking the email, subject headers can be as much of a telltale sign. Vague, provocative and threatening subject headers are a key giveaway that the email is intended to scare the victim into giving up their details.
- This email was sent by somebody claiming to be Cass Morgan. Similar to many companies, at CertiK we have a public team page where you can check the name and position of the person who is purportedly sending you the email. This method is not altogether foolproof – not everybody is on the team page and names on there may be easily mimicked – but it is an indicator nonetheless. You can also join our official Discord server or Telegram group and ask the available mods for clarification.
- Many spam and phishing emails contain broken English. Official emails should be written to a professional standard. Poorly written communication is a red flag, although more sophisticated scammers will be sure to use proper grammar.
- Here the fraudster is claiming to have saved the victim both their money and possibly a brush with the law. The wording is extremely vague to let the victim assume the worst and jump to conclusions. It’s also worth asking yourself: Is this what the real person or company would do? CertiK doesn’t have the authority to block random transactions to so-called illegal platforms or to contact individual wallet owners.
- This small sentence may seem innocuous but it serves the purpose of promoting a sense of urgency, especially after the prior sentence which raised legal concerns. This is done to make the victim panic, become emotional, and think irrationally.
- This is perhaps a minor point, but just like broken English, odd formatting should be cause for concern.
- This email ends with unofficial CertiK branding. This may be done on purpose because anybody that is actively aware of our work would notice that the logo is wrong and thus not fall for the scam in the first place. However, if you didn’t know who CertiK is this may not be an instant red flag leading to you being more prone to fall for the fraudsters' attempts.
The most important thing to do when reading a suspicious email is to slow down. If something sounds suspicious or too good to be true, read it over again. Do NOT click any links suspected to be fraudulent and watch out for hidden hyperlinks where what you think you’re clicking is not what you intend to open.
Discord Phishing
While messenger-app based phishing has been around for a while, Discord phishing is a relatively new form and has seen malicious users target the NFT space in particular. The main goal of a scammer on Discord is to trick an unsuspecting user into granting approval for their tokens to be transferred out of their wallet. Sounds like an impossible goal, right? Well, not exactly…
Phishers have developed highly sophisticated ways of duping users into thinking they’re interacting with a legitimate website, going so far as to clone a project’s official site (in the case of the Bored Ape Yacht Club phishing attack) while making the malicious links and functions subtle enough so as not to arouse suspicion.
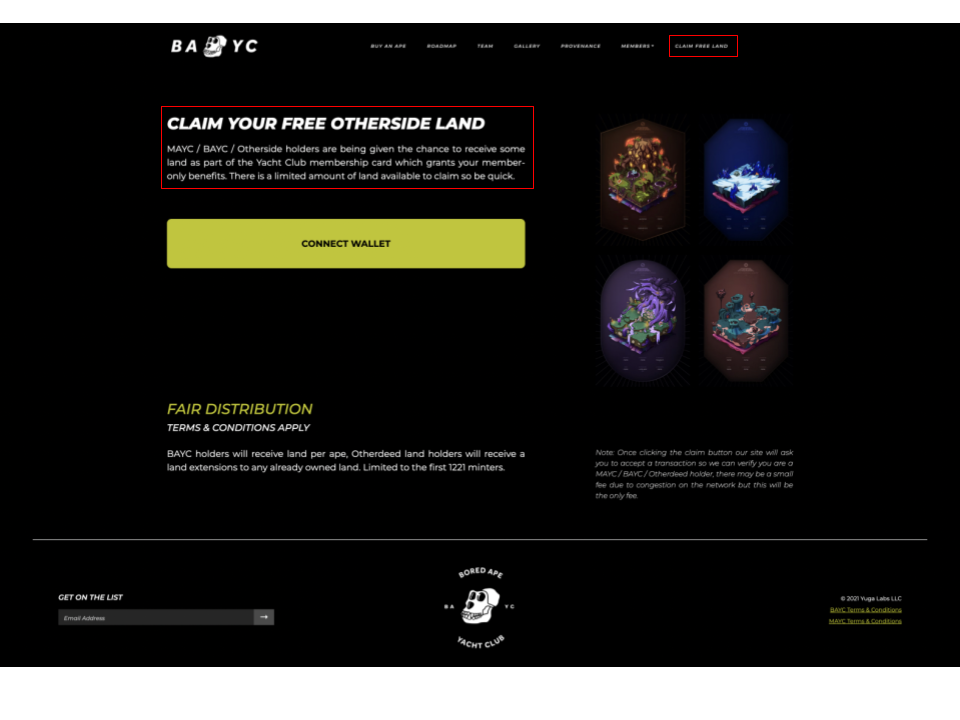 This fake phishing website looked almost identical to the official Bored Ape Yacht Club homepage.
This fake phishing website looked almost identical to the official Bored Ape Yacht Club homepage.
For a full description of the BAYC phishing exploit see our in-depth writeup.
While Discord, Telegram, and other messenger app phishing attacks differ in the details, there are a number of important rules to keep in mind:
- Be very wary of anyone reaching out to you with unsolicited offers that require external links
- If conducting an over-the-counter (OTC) deal, ensure that you trust the escrow service completely. Whether it’s a mutual friend or a respected community member, you’re trusting them with the full value of the NFT or tokens you’re giving them to hold. Never agree to use an escrow service proposed by the counterparty in which you do not have full faith.
- Similar to the technique outlined above in email phishing, scammers will often try to convince you that immediate action is required in order to protect your account or portfolio. 999/1000 times, this is a scam. When it comes to interacting with external websites or granting token approvals, it pays to be conservative.
Cloned Projects
To combat phishing and fraudulent claims we’ve initiated a live feed that genuine projects can implement on their website. This is pulled directly from CertiK's website and is a lot harder to fake. Here are two examples. One is the new methodology, hard to fake and will take you directly to the CertiK leaderboard page.


Next to the Baby Doge example is a real screenshot from a false claim. At face value, this may look real but upon second glance it’s clearly false. Notice the off-color branding and odd phrasing. Most of the time these claims will not link you to a Leaderboard page or audit report. If they do, check for differences as there is a chance the project may be a fraudulent clone. You can often check this by opening the project directly from their leaderboard page under the project's info. This should help circumvent this.

Protecting Yourself
While the platforms that scammers use differ, there are some fundamental ground rules that will help protect you from all sorts of phishing scams, whether they’re delivered to you via email, text message, Telegram, Discord, or any other platform.
- Check links carefully. In particular, make sure that the domain name an email is being sent from matches up with the official website of the company or organization. And be cautious of shortened URLs, since there’s no way to see where they’re taking you before you click on it.
- Verify from alternate sources. If somebody or something is making a claim, try and find an alternate source of information. This could be a crypto project's social media listed elsewhere or outright going directly to the body that the accused fraudster is claiming to be and simply asking. Often submitting evidence to genuine social media, i.e. Twitter and Discord should yield an informed result.
- Think twice before approving any contract. While it’s possible to revoke token permission using tools such as Etherscan or Zapper.fi, in the time it takes you to do this a scammer can transfer every token and NFT out of your wallet.
- If a message smells fishy, it’s probably a phish. While scammers are continuously honing their skills, committing these tips to memory and approaching every interaction with a watchful eye will help you develop an in-built phishing detector. This sense of intuition can be your greatest strength; listen to it. If anything seems off, investigate further before clicking any links.
- Spot and report. The easiest way to protect yourself against spam and phishing is to learn how to spot it, report it and ignore it. Never engage with, provide personal information, or send finances to the fraudster. Every email provider should give the option to mark an email as spam and we strongly recommend doing so.



