
TL:DR
On 23 May, 2022, Legend Coin (LDC) was exploited via a flash loan. The attacker was only able to gain $153, however, the vulnerability itself is worth highlighting. A day after this incident, the same attacker exploited Hackerdao for ~$65k. You can read about that incident in our Hackerdao blog post.
Summary
On 23 May, 2022, a coding error in Legend Coins contract was taken advantage of by an attacker which allowed them to gain $153. Although only $153 was taken in this instance, the coding error that we’ll highlight shows the importance of having smart contracts audited.
Exploit Transaction
Attacker executes flash loan transaction: https://bscscan.com/tx/0xe4c2089468fc5eb115d83e8a89382e53ad3df564f8c1abd02e1d74b40ab4c8de

Attack Flow
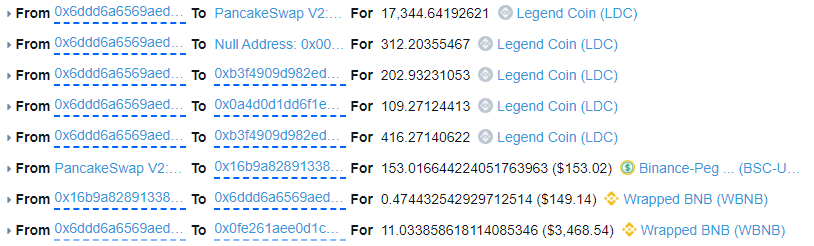
-
In this incident the attacker starts out with an 11 BNB flash loan which they swap for 19,565 LDC tokens. The LDC liquidity pool (LP) now has 11,69 BNB and 1,173 LDC tokens.
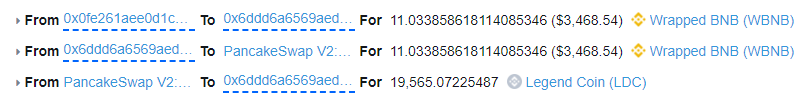
-
The 19,565 LDC tokens are sent to the LDC-WBNB LP and calls skim(to: LP LDC-BUSD). This transfers the 19,565 LDC from the WBNB LP to the BUSD LP which causes an imbalance in WBNB.
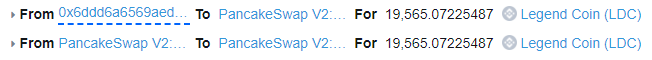
The imbalance is caused by the contracts 6% fee rate which is also applied to the LP (we’ll look at this more in vulnerability analysis below). As a result 1173 LDC tokens were removed (6% fee) from the WBNB pool. The WBNB pool now only contains 0.0049 LDC.
-
With the pool emptied, the attacker calls sync() on the WBNB pool to update the LDC price. LDC is now expensive to buy with BNB.
-
The attacker calls skim(to: attacker) which sends the 19,565 LDC back to the attacker.
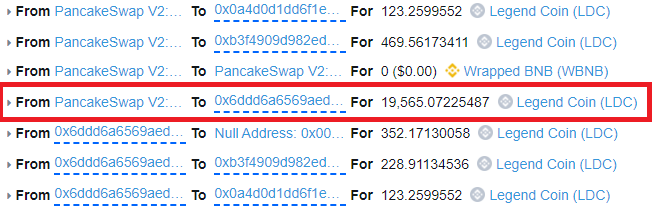
-
The attacker can now use the LDC tokens to get BNB. They swap 18,391 LDC to get the 11 BNB back that they swapped, this swap swings the price manipulation the other way. LDC is now cheap to buy with BNB, you’ll get more LDC for less BNB. The attacker swaps just 0.01 BNB in order to get 18,385 LDC.
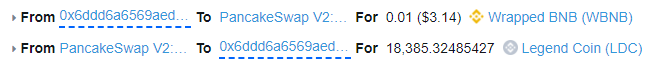
-
17,344 LDC is now sold for $153. The 11 BNB flash loan is repaid and the attacker keeps 0.47 WBNB profit.
Relevant Addresses
LDC 31 WBNB LP: https://bscscan.com/token/0x0a4d0d1dd6f1e25583537acb8fd32d4c10110269?a=0x83e47735bc2d3d665ff8c969b5991abc7c2a4b28
LDC BSC-USD LP: https://bscscan.com/token/0x0a4d0d1dd6f1e25583537acb8fd32d4c10110269?a=0x317a335e1895e941ccc1861fcafc8b545db6114c
Contracts Vulnerability Analysis
The issue with the contract is that the LP address isn’t excluded from the 6% trading fee. When the WBNB LP transfers 19,656 tokens to the BUSD LP the 6% fee is applied, causing an imbalance in the LP. If the swap address is excluded from the fee, the 1173 tokens that were paid, would have remained in the LP.
Conclusion
Although only $153 was taken in this incident it really highlights the need to have smart contracts audited. It is likely a simple oversight that the LP addresses weren’t excluded from transfer fees. On the other hand, what might seem like just a simple omission can have a destructive impact if left vulnerable.








