
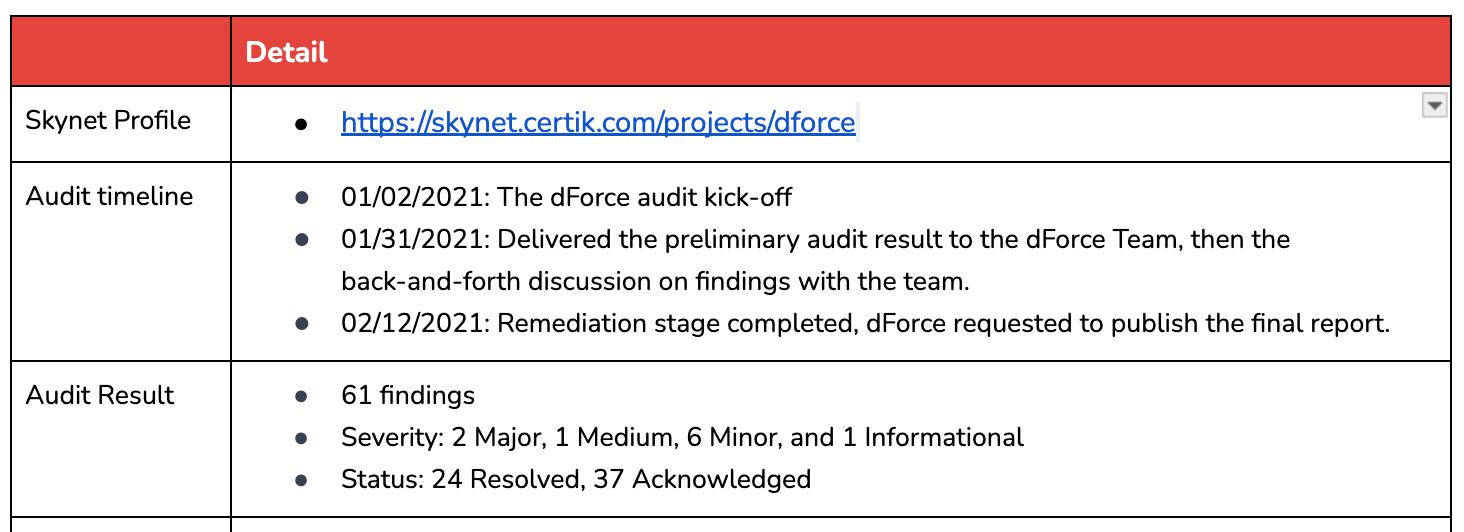
Project name: dForce
Project type: Lending
Date of exploit: Feb 9, 2023
Asset loss: $3.7M
Vulnerability: Price manipulation (Read-only Reentrancy)
Date of audit report publishing: Feb 21, 2021
Conclusion: Out of Audit Scope
Details of the Exploit
Background
dForce is a DeFi project providing services including stablecoin, lending, trading, and governance. In the dForce lending protocol, the amount of tokens a user can borrow depends on the value of their collaterals, which is calculated using external price Oracles. In this exploit, the external price Oracle is a Curve protocol.
Nature of the Vulnerability
- A manipulated asset price incorrectly calculates the attacker's collateral value, so the attacker can borrow more than its collateral to drain the vault.
- The asset price is provided by a Curve protocol, which has a read-only reentrancy issue in its implementation.
- The attacker manipulated the token price by triggering external calls to update its collateral in dForce's lending protocol in the process of withdrawing liquidity from the Curve pool.
CertiK Audit Overview
Conclusion
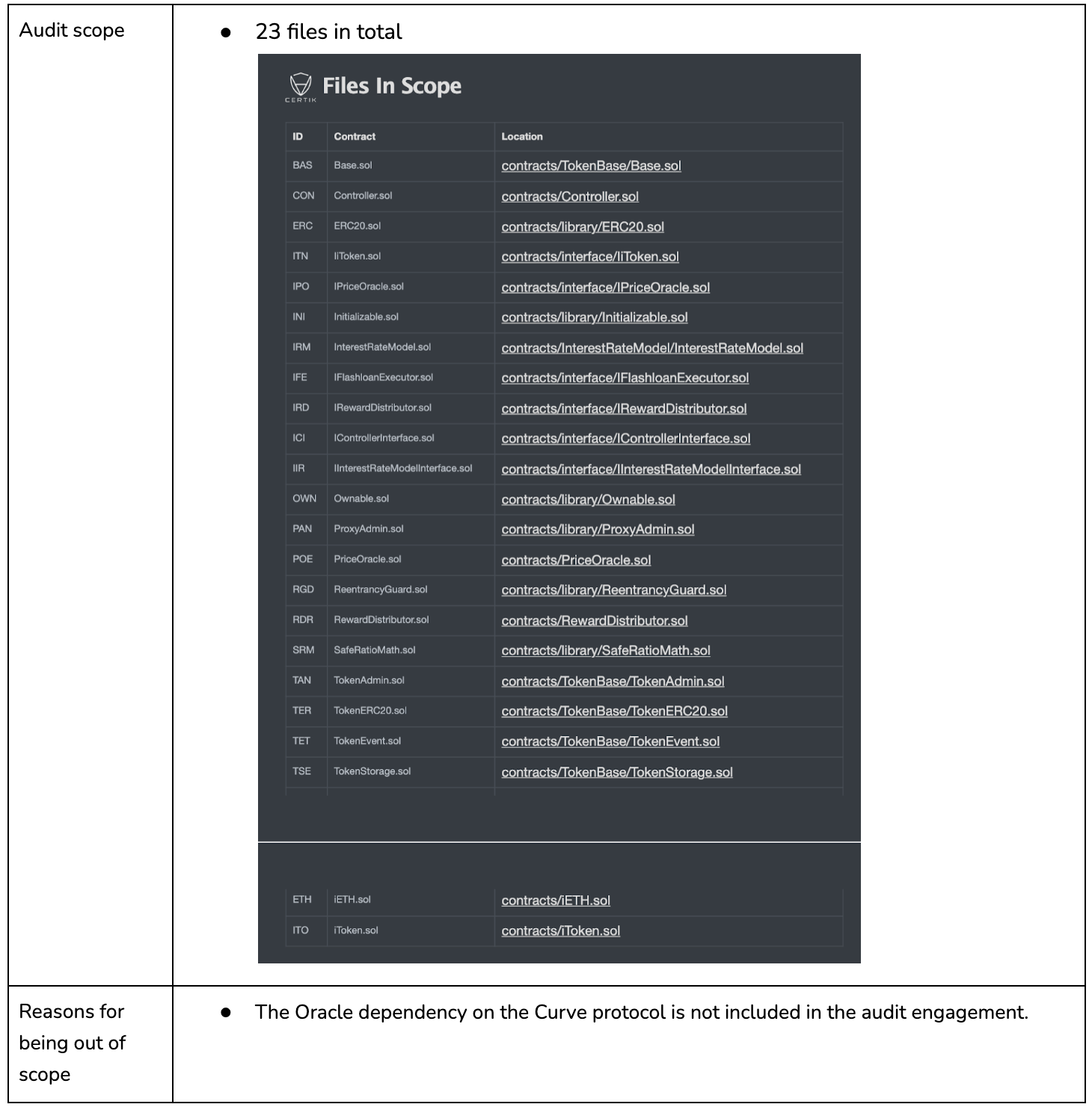
On Feb 9, 2023, dForce's lending protocol was attacked, leading to a loss of $3.7M. The attacker made use of a read-only reentrancy vector to manipulate the price in the lending protocol to drain funds from the pool. The vulnerability lies in the dependency on the Curve protocol, which was used as price Oracles in dForce's lending protocol, and has been widely recognized by the community. The dependency on the Curve protocol is not in CertiK's audit scope.
References
dForce's announcement: https://twitter.com/dForcenet/status/1623904209161830401



