
Introduction
On 24 July, 2023 Palmswap fell victim to a flash loan exploit, resulting in the loss of 901,455 USDT (equivalent to approximately $901,000 USD). The exploit was made possible due to a vulnerability in the project’s PlpManager contract, where the incorrect calculation of USDP created a loophole susceptible to flash loan attacks.
Event Summary
On 24 July, Palmswap was exploited in a flash loan attack resulting in the loss of approximately $901,000. The exploit was first attempted in block 30248637 by externally owned address (EOA) 0x5cf40 which failed due to the attacker running out of gas.
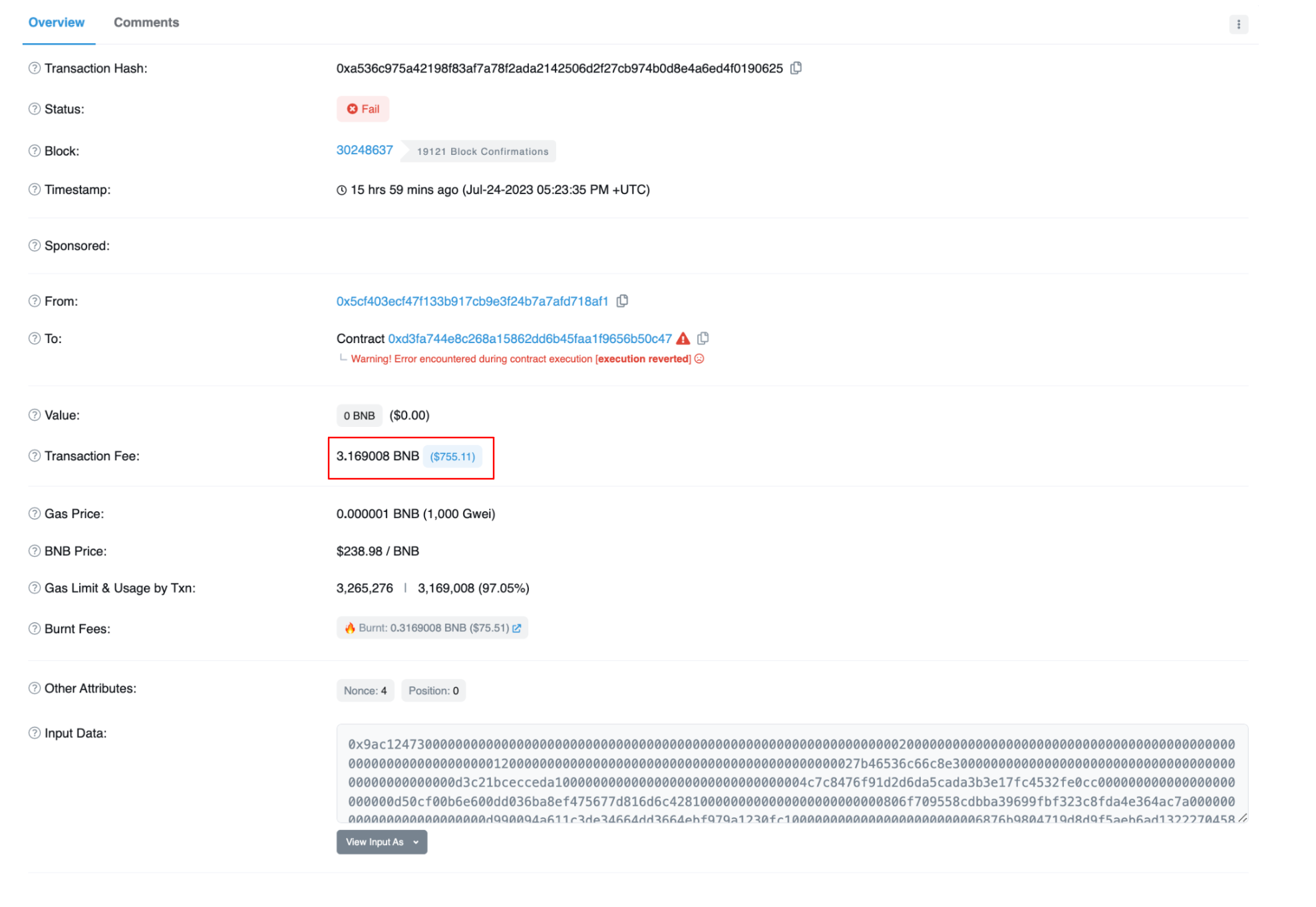 Image: Failed transaction. Source: Bscscan
Image: Failed transaction. Source: Bscscan
The original attacker withdrew 1 ETH from Tornado Cash on the Ethereum network. The 1 ETH was then swapped for USDT and bridged to Binance Smart Chain (BSC). The USDT was then swapped for BNB and used to create the attack contract. Unfortunately for the exploiter, they did not have enough BNB to cover the exploit.
This then allowed EOA 0xf84ef to see the failed transaction, understand and then replicate the transaction in block 30248638 and pay the correct amount of gas.
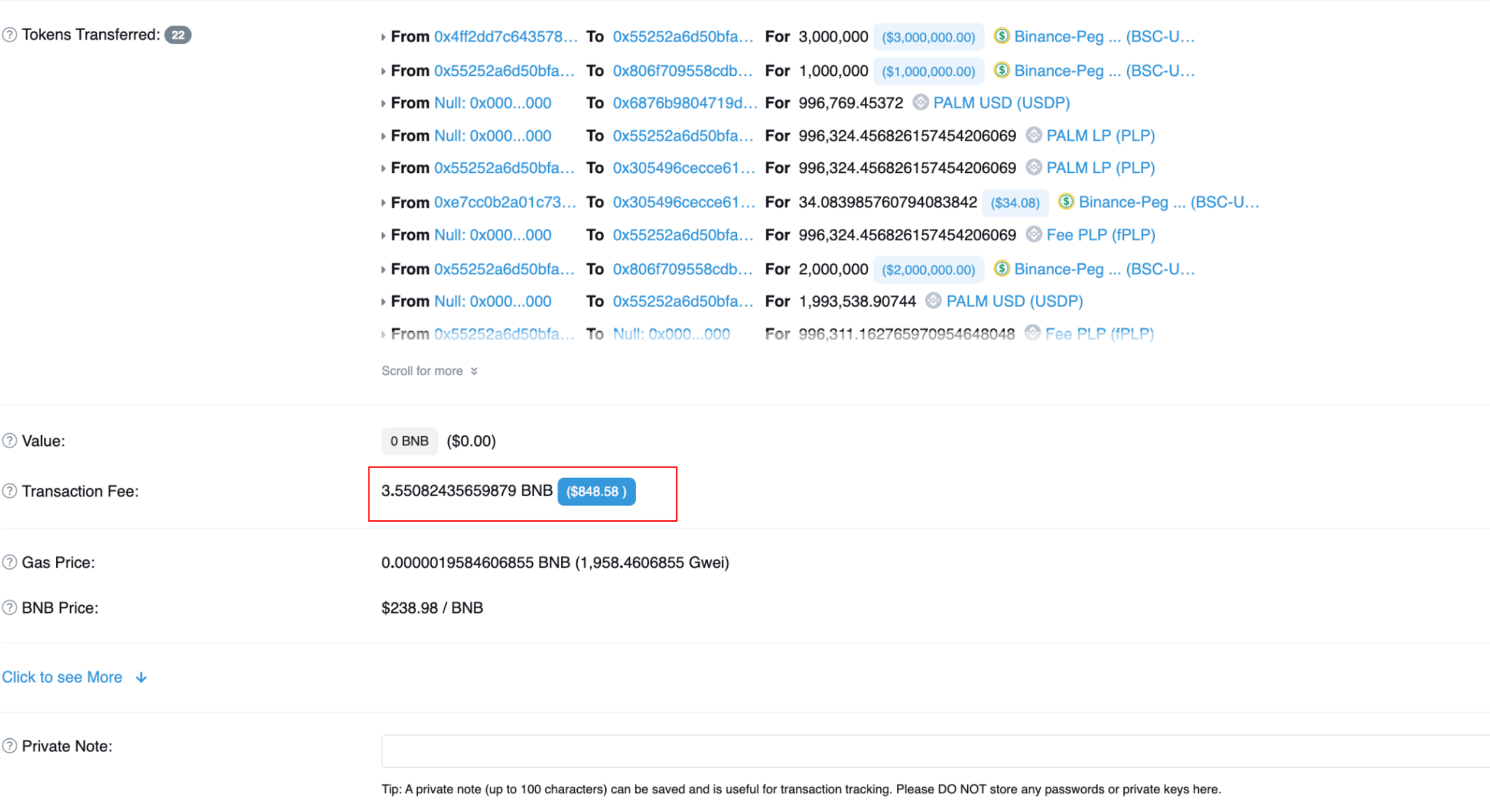 Image: Successful transaction. Source: Bscscan
Image: Successful transaction. Source: Bscscan
It would seem that the original attack was unable to complete because they attacker didn’t have the additional 0.4 BNB required to pay for the transaction.
Once the successful exploit was carried out by EOA 0xf84ef, the stolen funds were transferred to EOA 0x0Fe74 which is where they currently sit.
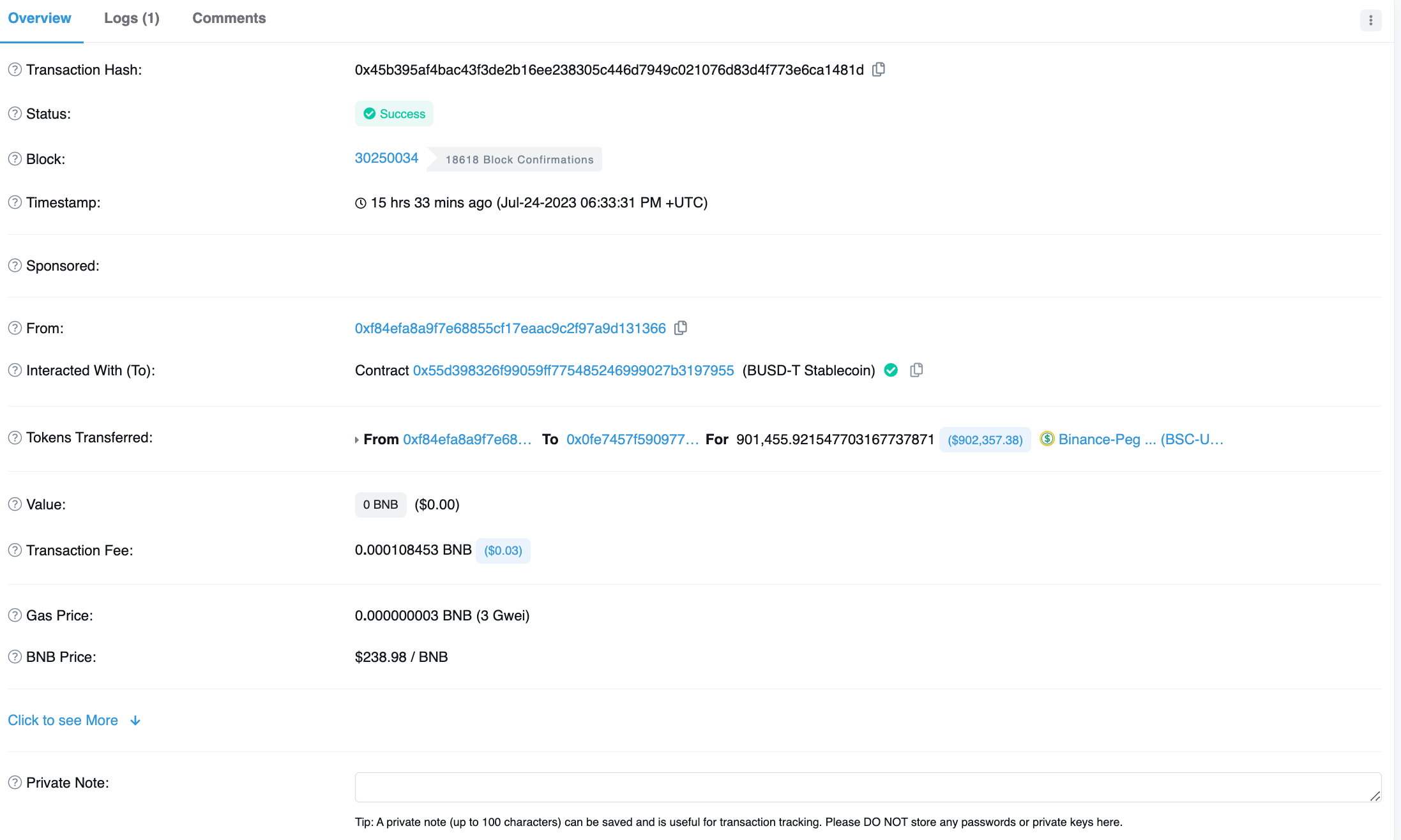 Image: Transfer of stolen funds. Source: Bscscan
Image: Transfer of stolen funds. Source: Bscscan
The Palmswap team reached out to the wallet that is holding the stolen funds and are attempting to negotiate a bounty. However, BSC scan appears to have the wrong wallet labelled as the Palmswap exploiter:
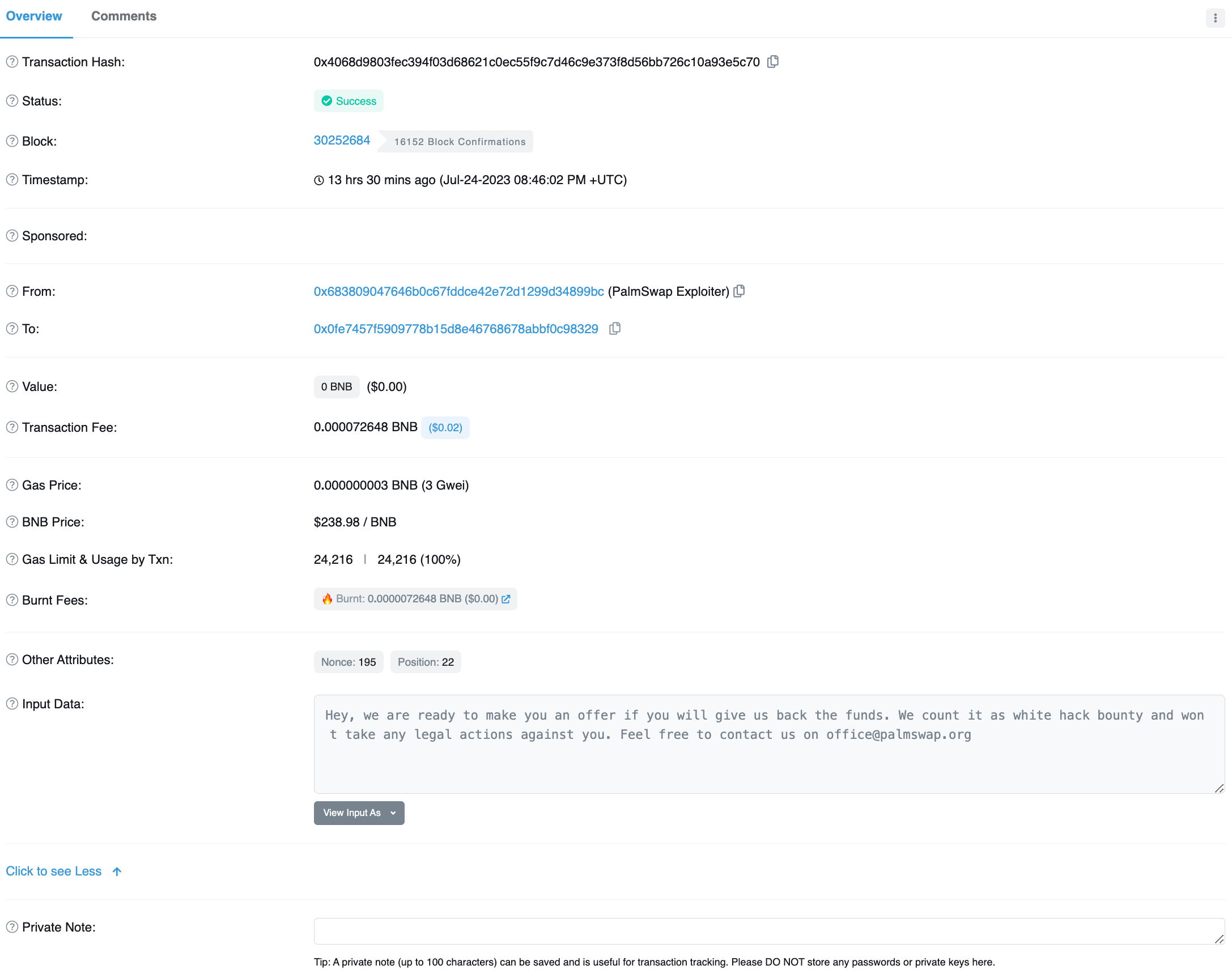 Image. On-chain message offering a bounty. Source: Bscscan
Image. On-chain message offering a bounty. Source: Bscscan
The beginning of negotiations with the hacker was confirmed by Palmswap’s official X account.
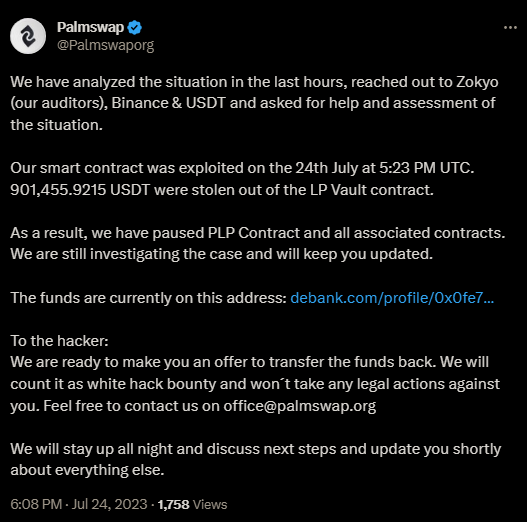 Image: Palmswap X announcement (source: @Palmswaporg)
Image: Palmswap X announcement (source: @Palmswaporg)
The negotiations were successful with the exploiter returning the stolen funds in the this transaction.
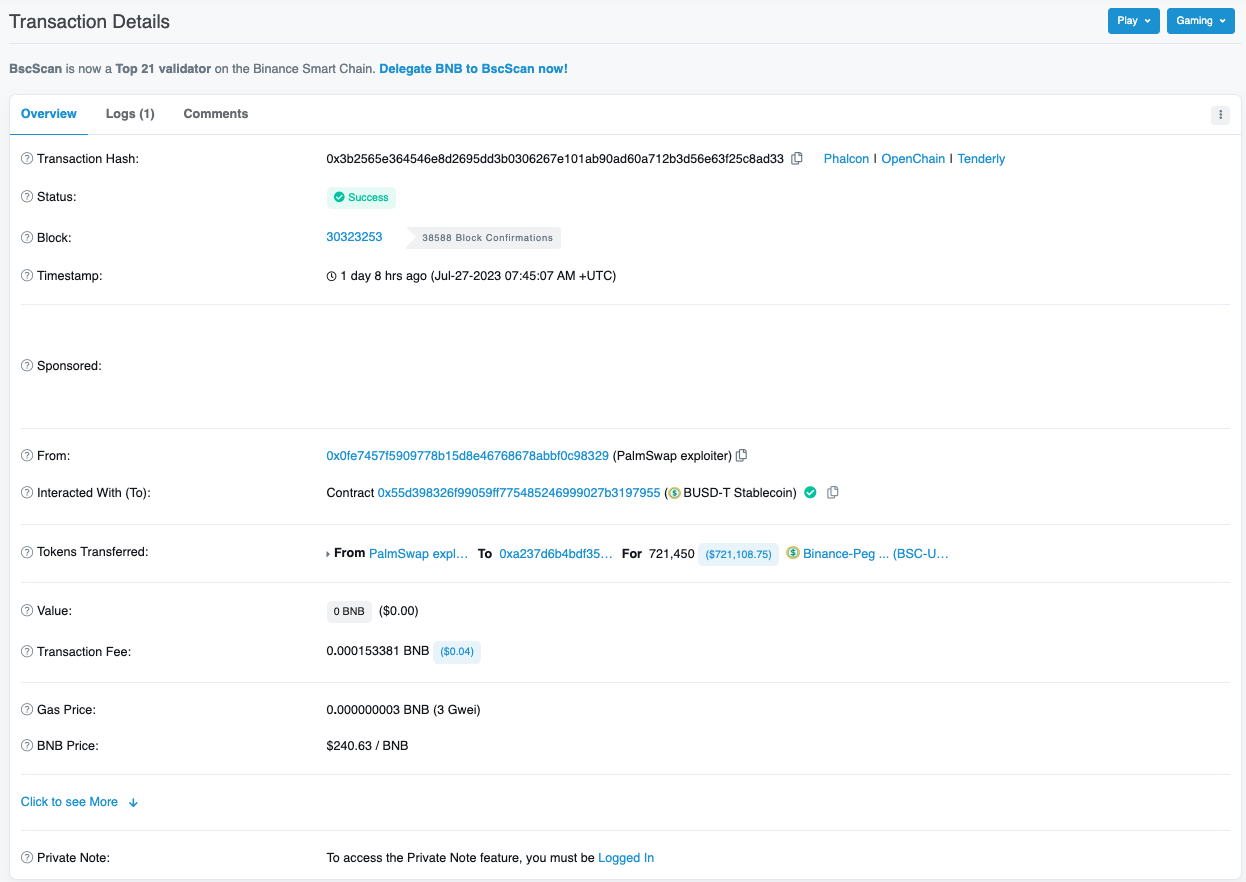 Image: White hat returning funds transaction. Source: Bscscan
Image: White hat returning funds transaction. Source: Bscscan
An official statement from Palmswap regarding the incident.
Attack Flow
Exploit Transaction: 0x62dba55054fa628845fecded658ff5b1ec1c5823f1a5e0118601aa455a30eac9
Attacker: 0xf84efa8a9f7e68855cf17eaac9c2f97a9d131366
Vulnerable Contract: 0xa68f4b2c69c7f991c3237ba9b678d75368ccff8f
-
The attacker flash loaned 3,000,000 USDT ($3,000,691.52).
-
Through the function buyUSDP(), the attacker swapped 1,000,000 USDT for 996,769 Palm USD (USDP) from the Vault and received 996,324 PALM LP (PLP). The attacker then received 996,324 fee PLP (fPLP) after staking the PLP.
-
The attacker swapped the remaining 2,000,000 USDT for 1,993,538 USDP then triggered the removeLiquidity() function which swapped the fPLP from the previous step for 1,962,472 PLP, then subsequently swapped for 1,956,585 USDT ($1,957,036.45). Due to an incorrect USDP calculation in the PlpManager contract, the Vault mistakenly returned more USDT to the attacker.
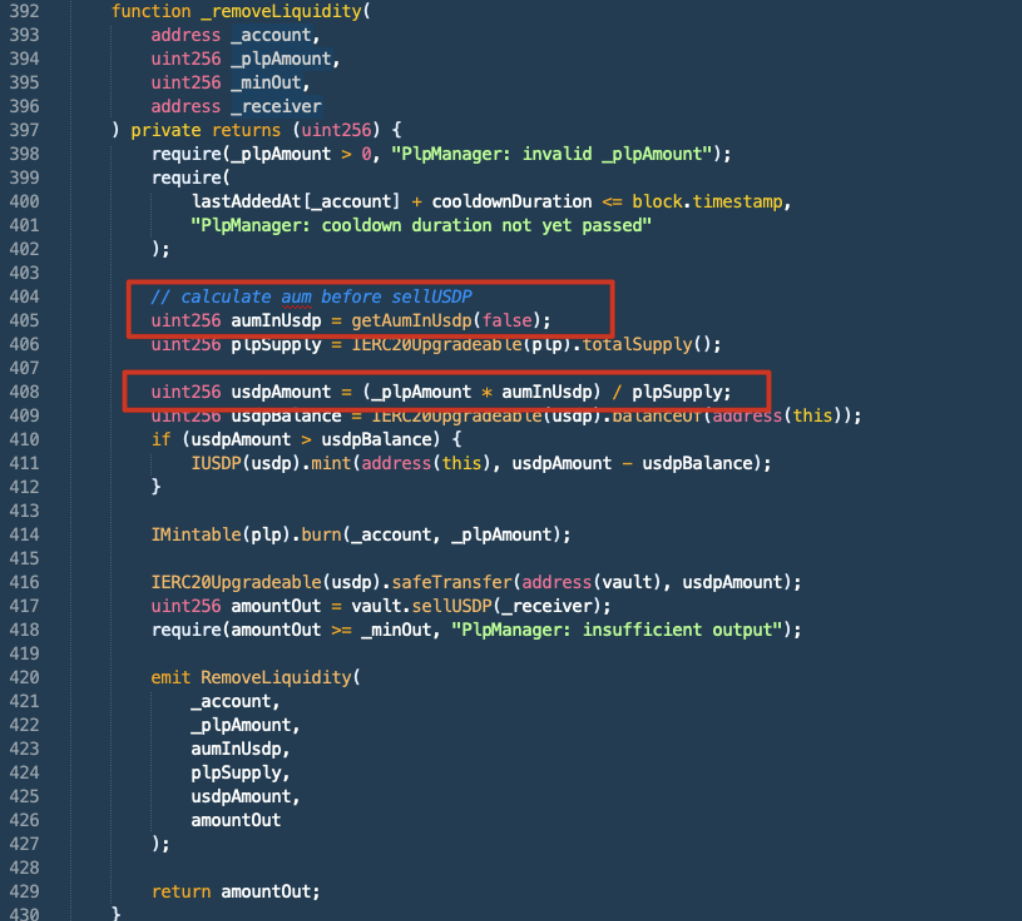 Image: plpmanager.sol Source: BscScan
Image: plpmanager.sol Source: BscScan -
1,953,430 USDP from step 3 was swapped for 1,947,570 USDT ($1,948,019.41).
-
The attacker repaid the initial 3,000,000 USDT borrowed through the flash loan which left $901,445 for the attacker which is still in the attacker’s wallet.
Flash Loan Attacks in 2023
There have been 128 flash loan attacks this year, by comparison we recorded 101 in 2022. Flash loan attacks have become increasingly popular as attackers look to maximize profits from exploiting smart contract vulnerabilities.
At the time of this incident, flash loan exploits have resulted in $255 million in losses, an average of just under $2 million per incident. In the first three weeks of July we have recorded 22 flash loan attacks causing $8.5 million in losses. The average number of flash loan attacks per month in 2023 is 18. July is currently on course to have the most flash loan incidents in a month on record. Currently it is tied with February 2023 which also holds 22 incidents over the course of the month.
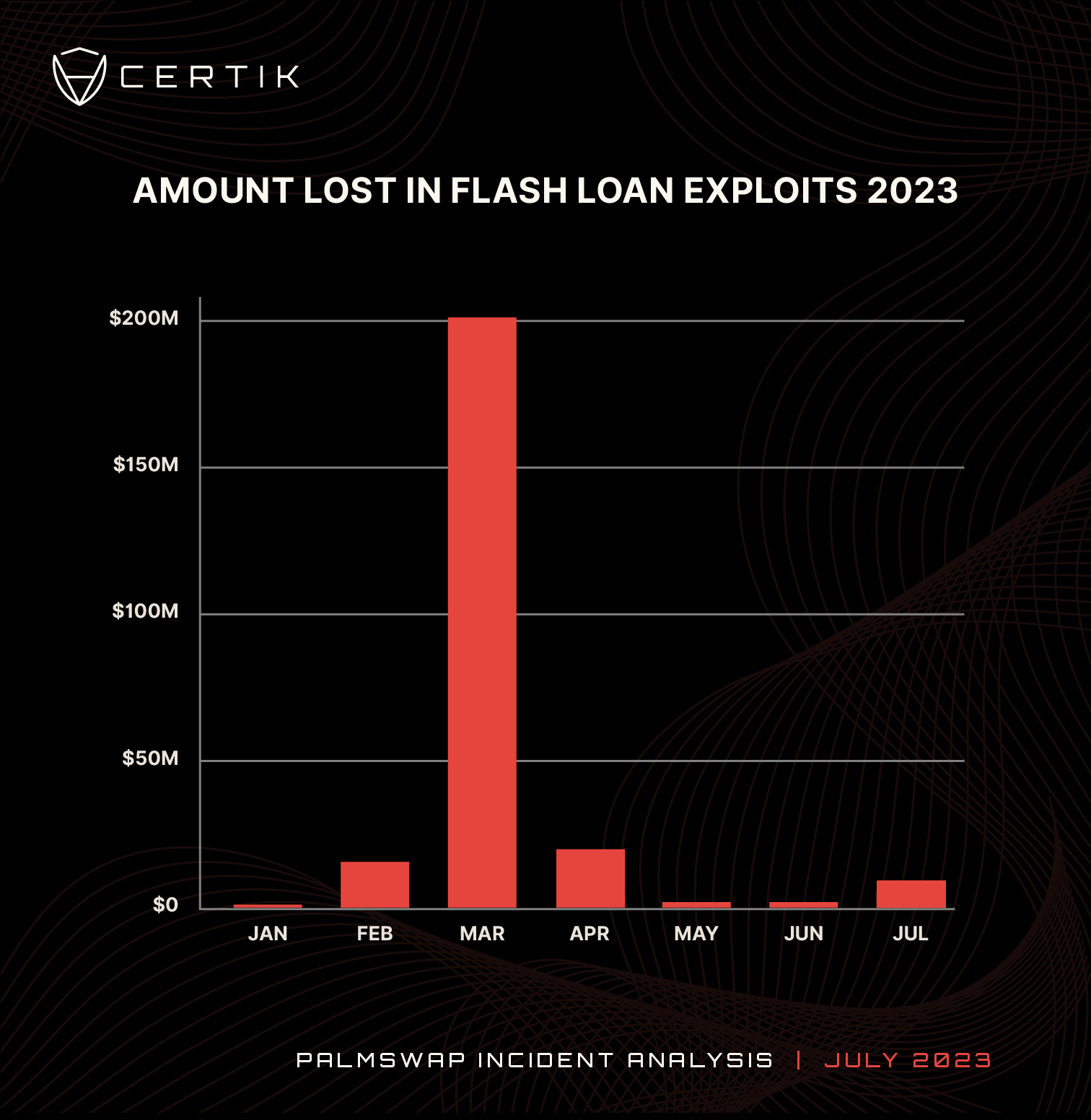 Chart: Funds lost in flash loan exploits in 2023. Source: CertiK
Chart: Funds lost in flash loan exploits in 2023. Source: CertiK
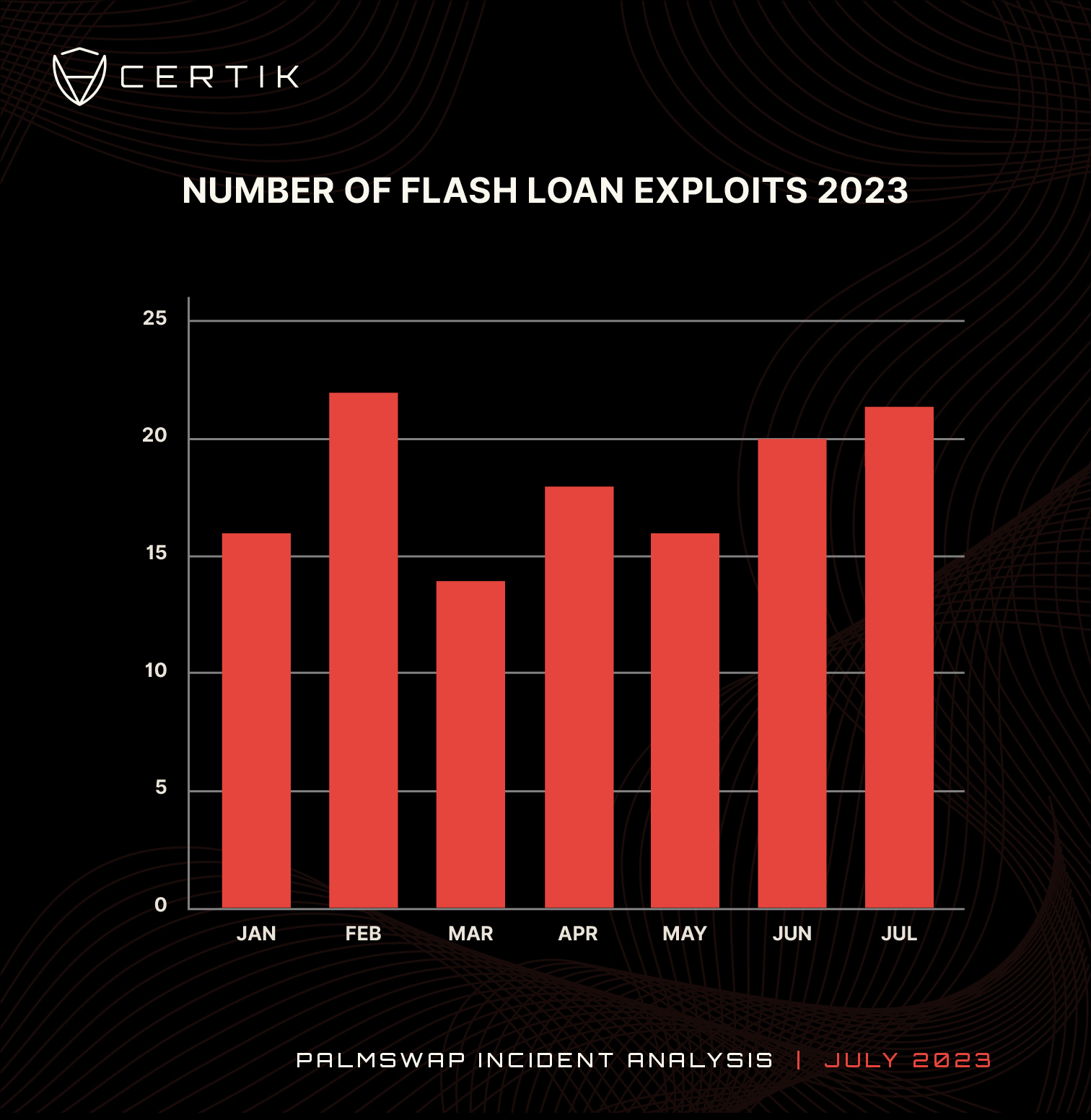 Chart: Number of flash loan attacks in 2023 by month. Source: CertiK
Chart: Number of flash loan attacks in 2023 by month. Source: CertiK
Conclusion
The Palmswap flash loan attack is the second largest malicious flash loan that CertiK have detected in the month of July which has seen a combined total of $5.8 million lost to this type of attack. The attack also comes in at 10th place so far in 2023. Whilst there has been no respite in the volume of flash loan attacks in 2023, which has seen 127 so far this year compared to 101 in 2022, the amount of funds lost is significantly lower. There are likely a couple of reasons for this. First, the market conditions in the first half of 2022 meant that assets stolen were typically worth more in USD value. Second, because flash loans were a relatively new concept the security strategies to defend against them were still being developed meaning that projects holding large amounts of funds were targets. The volume of flash loan attacks in 2023 demonstrates the need for robust security measures and third party audits. Check CertiK Skynet - Web3 Security, Due Diligence and Insights to help you understand the security risks behind projects you wish to engage with.
 Image: plpmanager.sol Source: BscScan
Image: plpmanager.sol Source: BscScan


