
Introduction
From 12 March to 16 March we have seen nine private key compromises (PKC) that have led to a combined loss of at least $22.96 million in March, with five of those incidents incurring losses over $1 million. These incidents showcase the continued devastation that private key leakages can have on the Web3 ecosystem which has already seen approximately $239 million lost to this type of attack in 2024. This demonstrates that the misuse of private keys are still a major issue in Web3 and will likely continue to be a major driver for losses throughout 2024. In this blog, we’re going to break down four of the largest private key compromises over the past 14 days.
Stats
Losses due to private key compromises have already hit $237 million in 2024. By comparison, in Q1 2023 we recorded $18.8m in losses due to the same attack vector, which means 2024 has seen a ~1,160% increase dollar value losses. Furthermore, we have seen an increased number of private key compromises with 24 attacks so far in 2024 compared to 11 in the same time period in 2023.
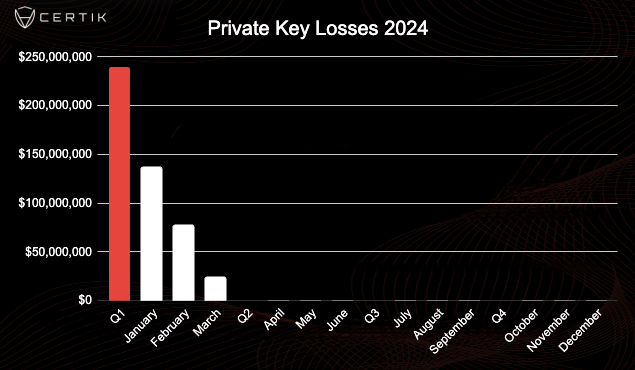
On 31 January 2024, Chris Larsen, Co-founder & Executive Chairman of Ripple, lost approximately $112m worth of assets after his private keys were compromised. The incident accounts for nearly half of all losses to this attack vector so far. We’ve also seen ~$32.3 million and $26 million lost to the PlayDapp and FixedFloat private key compromises that occurred in mid February. However, we have seen approximately 10% of the overall amount lost to private key compromises in 2024 over the last 14 days.
Unfortunately, private key compromises will highly likely continue to be a major driver for losses in the Web3 ecosystem. As asset prices rally centralized entities holdings will grown in value and present a lucrative target for malicious actors. In the following sections, we will outline recent private key compromises that have led to losses of over $1 million.
NFPrompt
NFPrompt announced on X that they had experienced an exploit that had resulted in a unspecified loss. In their post, they state that a group of hackers compromised wallets associated with the team, including NFP contract administrators. However, the announcement does not specify the attacker wallets or the amount of funds they hold. CertiK investigated and determined that at least one of the exploiter wallets is EOA 0x60275d1cC368CF021547a82a51cFb8C055390DA3, which is now designated Fake_Phishing118154 on BSC scan.
Before the designation, CertiK identified unusual activity around this wallet as it became the fourth largest holder of NFP tokens. On the 13th March, the wallet saw a large inflow of NFP tokens which equated to $10 million at the time of the transactions. In total, 2,600 wallets transferred NFP tokens to the suspicious wallet. Currently, we are not suggesting that 2,600 wallets have been compromised but we assess the transfers are associated with the attack
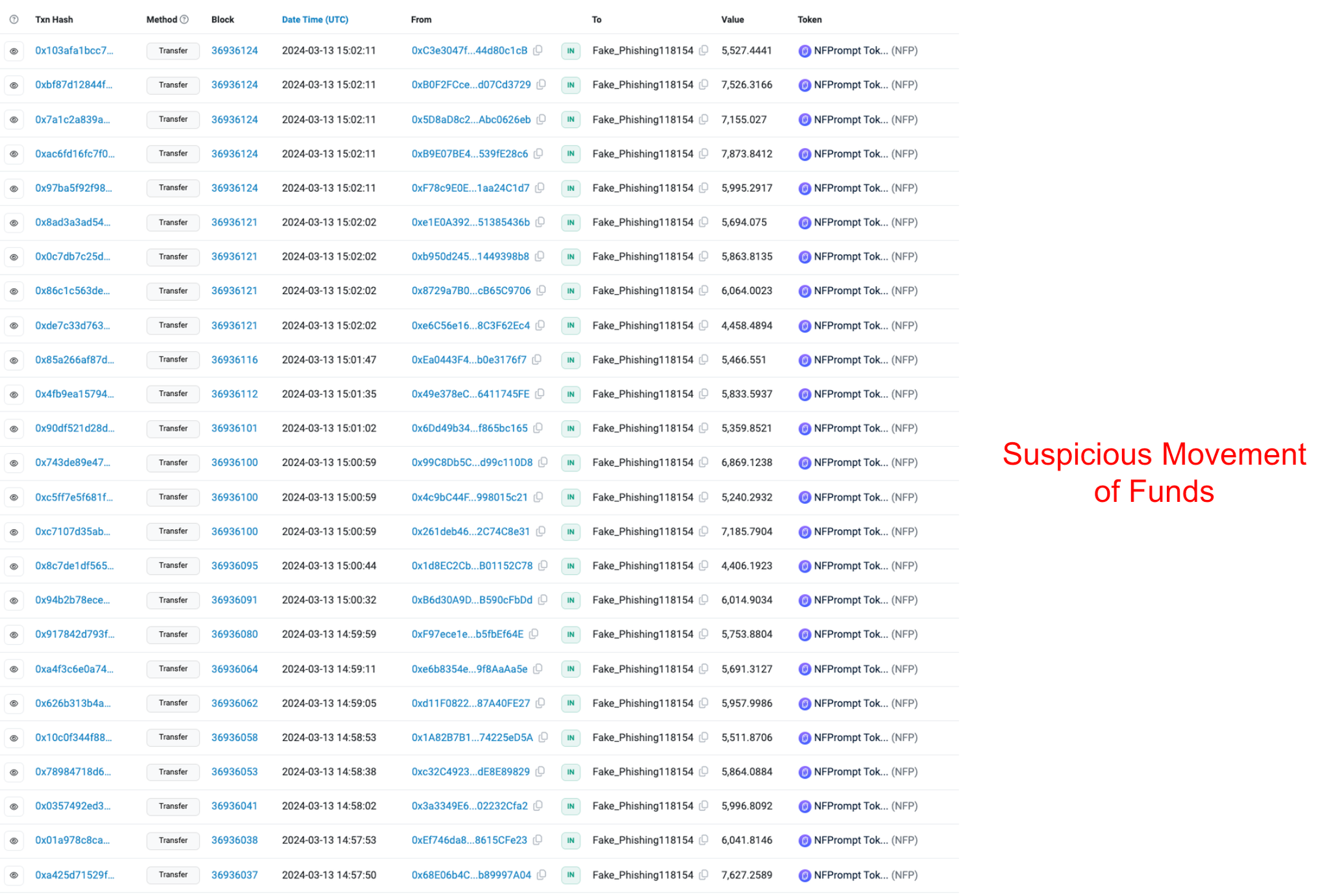
The suspicious wallet created a multisig wallet and transferred approximately $7 million worth of NFP tokens. Additionally, 3.6 million NFP tokens worth approximately $3.4 million at the time of transaction were transferred to MEXC. In total, we have attributed approximately $10.4 million lost to this exploit.
Mozaic Fi
On 15th March, the vaults of Mozaic were drained following a compromise to the Master role wallet. In total, $2.1 million were stolen and transferred to MEXC and Binance. We have since seen reports that Mozaic were able to recover up to 90% of the stolen funds due to prompt reporting to the relevant exchanges.
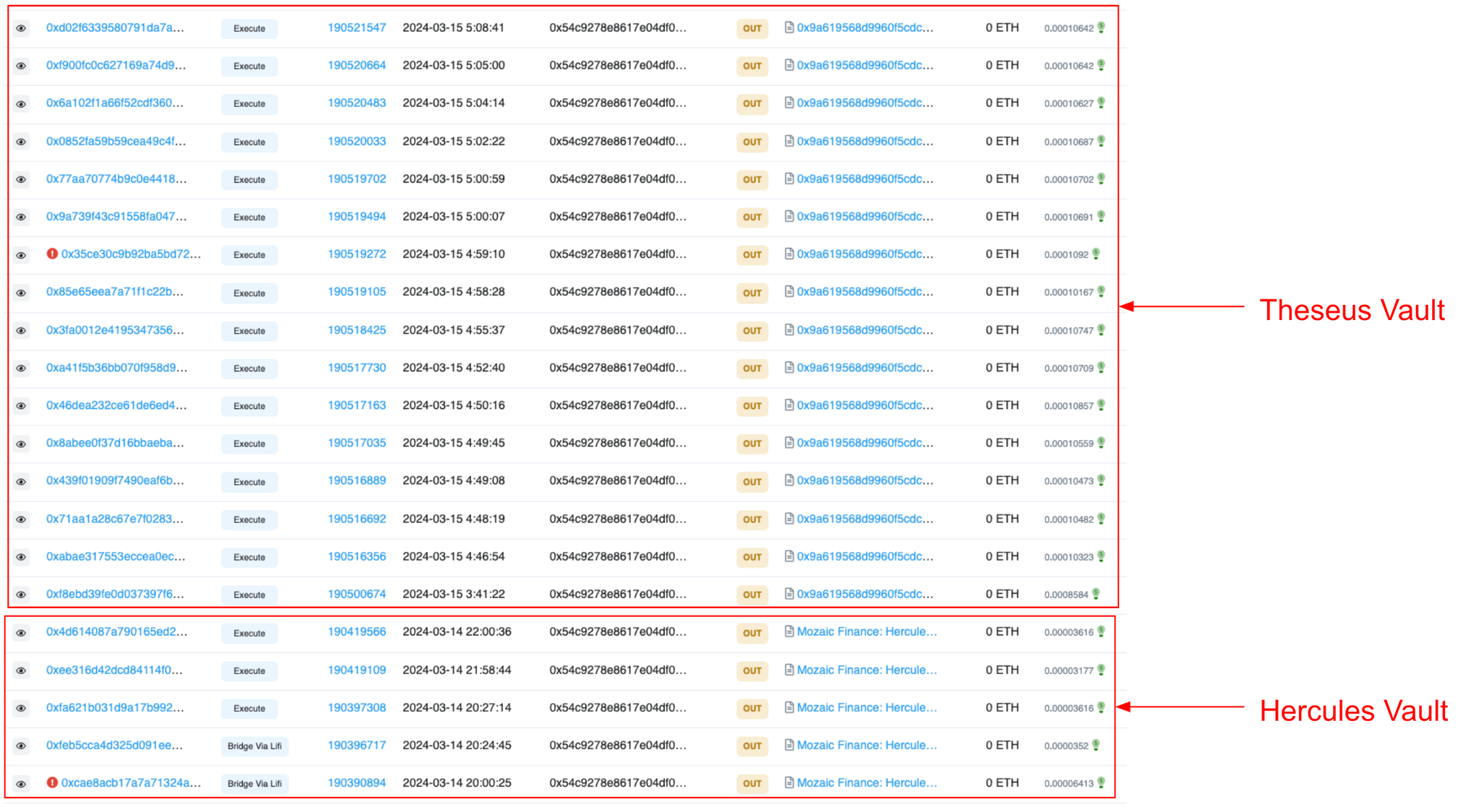
The Moziac Finance project has two vaults named Hercules and Theseus which were both emptied due to the security breach. The Mozaic vault contracts contained privileged functions that only the Master role can call. The two main calls that were abused are bridgeViaLifi and execute.
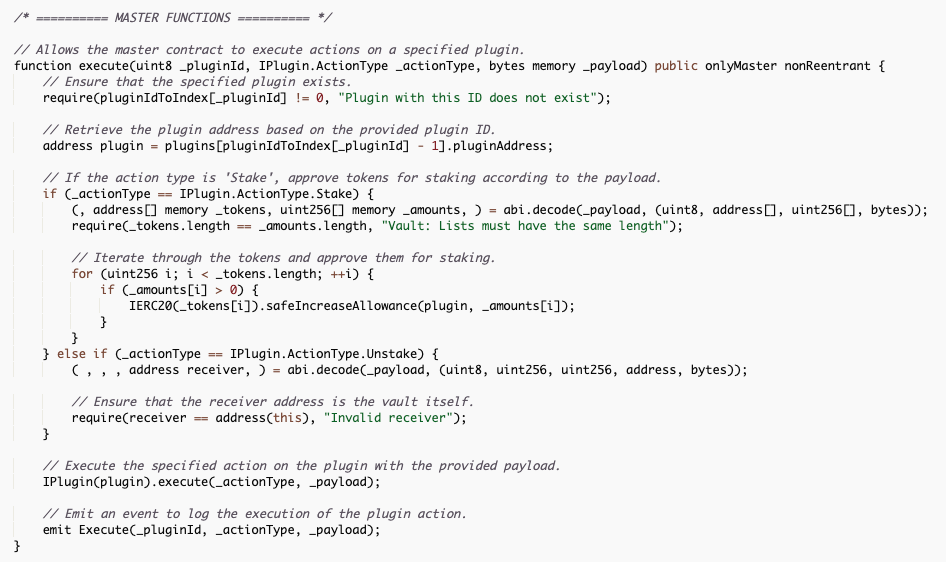
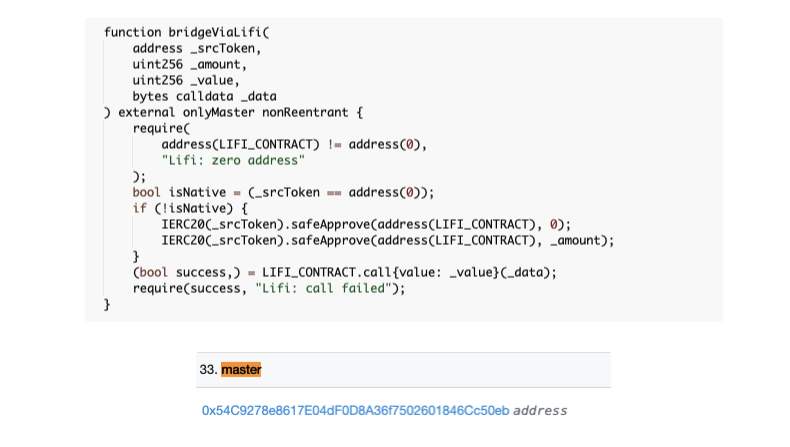
By examining the Master address for the Mozaic vaults, we can see that the exploiters first targeted the Hercules vault and then Theseus vault.
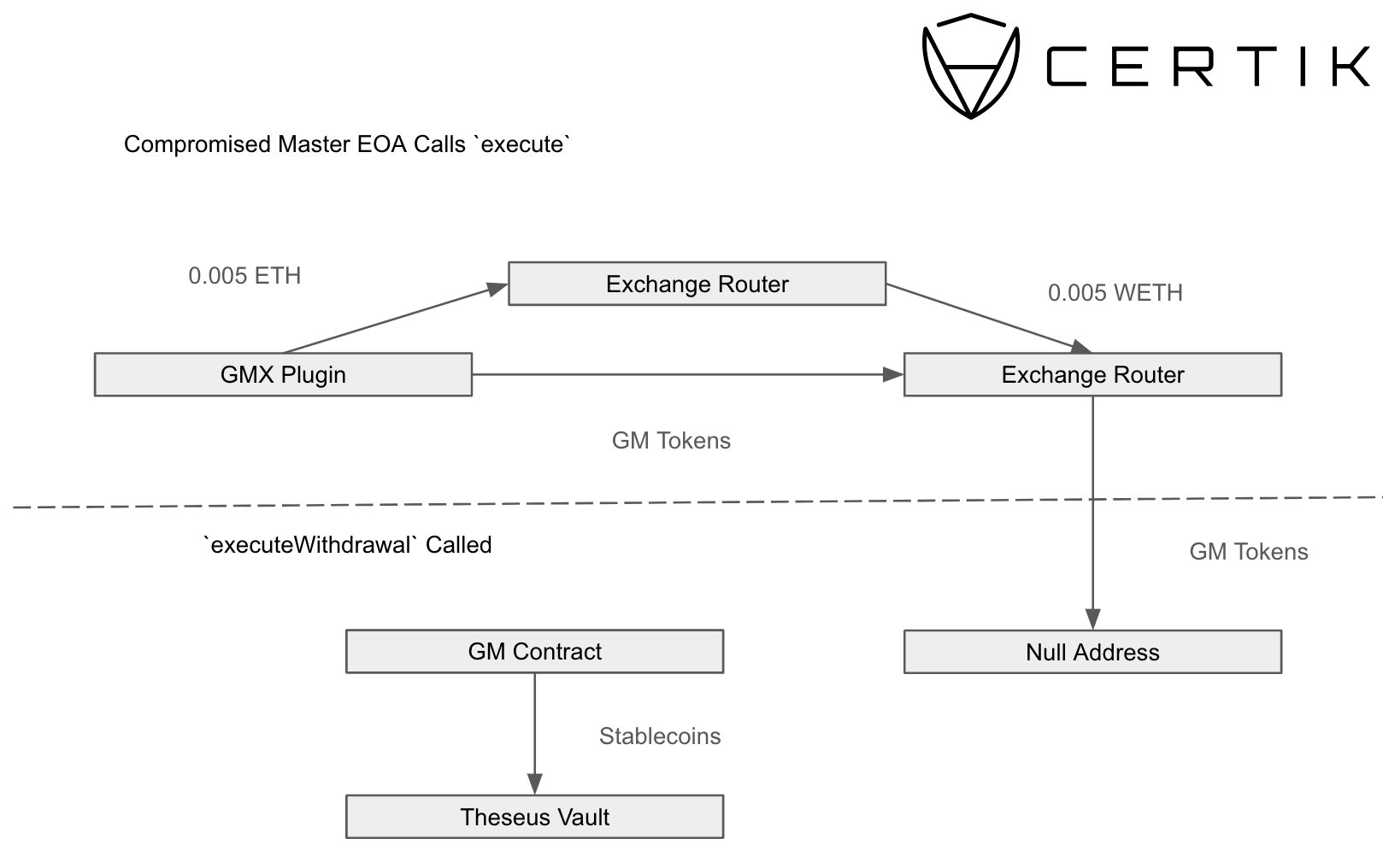
The first stage of the attack leveraged the execute function to unstake USDT from Stargate and place it within the Hercules vault. From there, execute was called on the Theseus vault repeatedly to unstake GMX tokens, and swap them for USDC and place the funds back within the Theseus vault. We can see this process below.
Once the GM tokens were swapped for stablecoins, the exploiters called bridgeViaLifi to empty the vaults and transfer stolen funds to EOA 0xd6d4e8038df50803412d1b1ad2c9845bacf7c52b and 0x76783b5387a3c95cc96442bf609d214547ed0cf4. The majority of the funds were then transferred to MEXC.
According to an announcement from the Mozaic team, up to 90% of the stolen funds have been frozen on the MEXC platform. They have furthermore claimed that the incident was due to a rogue developer with access to the project’s private keys.
Wilder World
On 16 March Wilder World had an unauthorized breach that involved 9 legacy vesting contracts. At 3:07 AM UTC 0x37358Aa5D051B434C23Bad744E56E6A484107272 (Zero Name Service: Deployer) transferred ownership of contract 0x6cA959fbc8e3df1fBeA5d9791De0047E1B3a57C6 (proxy) to 0x6584A486F711eB8aC47aBf78A5C8e218Ee758fa9 (attacker).
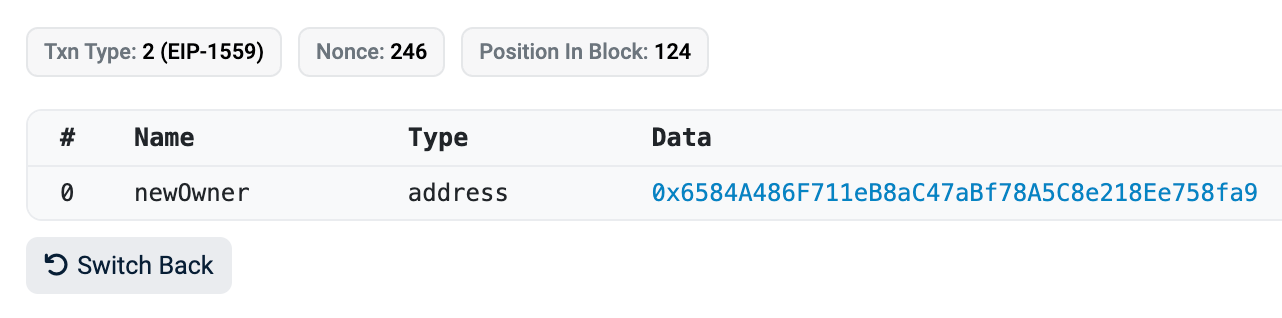
The transfer of ownership then granted the malicious wallet permission as contract owner to upgrade the legacy vault contracts to new implementations that they deployed shortly before upgrading.
The new implementations allowed the attacker to transfer the contract token balances
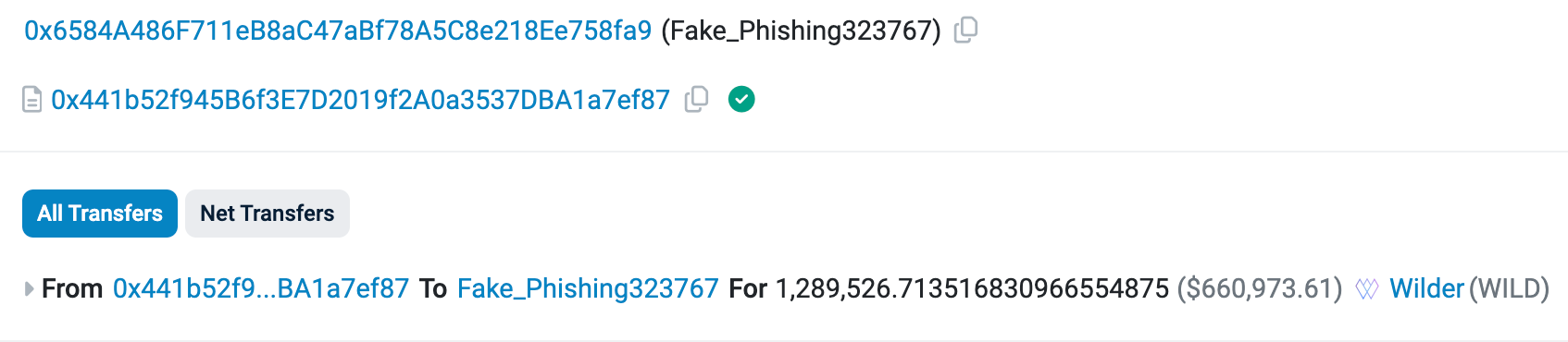
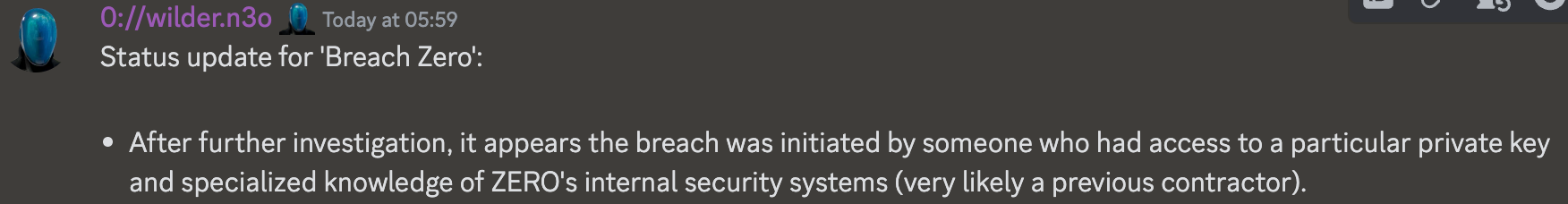
The root cause is likely due to a private key compromise of 0x37358Aa5D051B434C23Bad744E56E6A484107272 (Zero Name Service: Deployer) which was used to change contract ownership. An investigation by Wilder World revealed that it was likely a previous contractor who had access to the private keys.
A total of 515 ETH (~$1,814,583) worth of WILD and MEOW was taken from 9 contracts as follows, amounts are approximate at time of writing:
- 0x441b52f945B6f3E7D2019f2A0a3537DBA1a7ef87 - $660,973
- 0xD393224e6EBbFb46C6a09A6Fd8acc596f6392402 - $575,604
- 0x956234670110D154Abb591FB46FC3b5A455A3c97 - $209,037
- 0xB7dFcb421412F16B25DDd4AD4bdd73D0883136D8 - $164,514
- 0x109f7B8608785201a9AAa4d75dBF03A9Fa663187 - $142,863
- 0x8E4C057032436498817de977Dc1aE10e3Dfd23c1 - $104,127
- 0x5521D7E4D9AE2294ecDf505fd138b8924Ea7A8E2 - $51,179
- 0xE516ef5d103bf567238dB2A5F88781D18214fF6C - $35,021
- 0x6E9c63AF66e1F59137214d51ab7716E8dB9D6467 - $31,231
The stolen assets were transferred to EOA 0x6584A486F711eB8aC47aBf78A5C8e218Ee758fa9. Despite Wilder World issuing a message to the exploiter to return funds the assets were swapped for ETH and transferred to EOA 0x7f0756D3aAAa6E8A34d29e6E8A7a78617d8fF662, where all 515 ETH was deposited into Tornado Cash.
Remilia
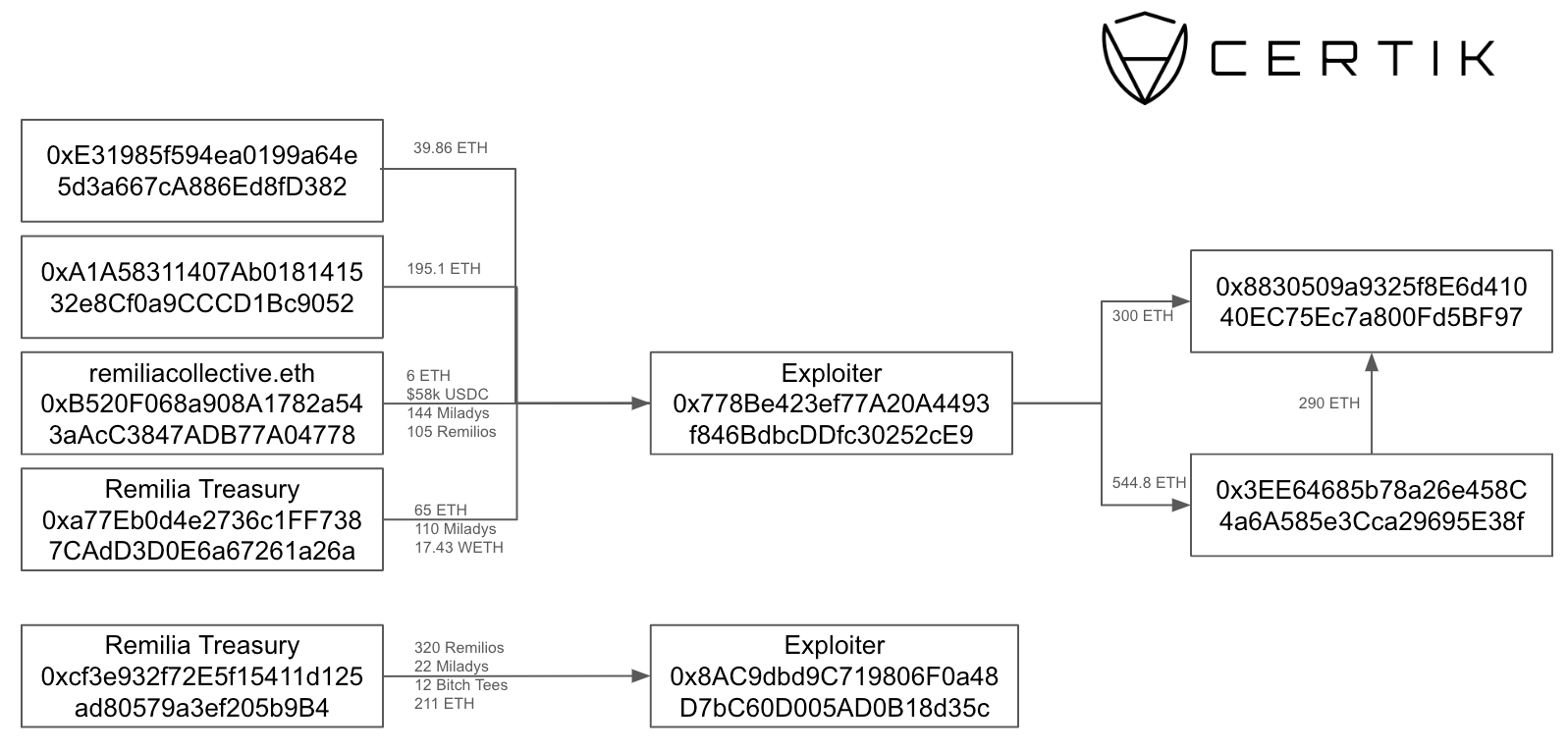
On 16 March, several wallets belonging to Remilia, founder of Milady Maker and other projects, were compromised. Due to the number of compromised wallets, the project believe it is likely their BitWarden account was exploited, giving the attacker access to multiple wallets. 300 ETH and a number of assets worth a further 544 ETH, which included REMIO and MILADY NFTs, were taken from multiple wallets. The list of compromised wallets include:
0xB520F068a908A1782a543aAcC3847ADB77A04778 (remiliacollective.eth)
0x3fAd44f892b986263ac69dB971db8Da172185387 (charlemagnefang.eth)
0x4Cc17f677c1271bAba0d10df83438821B5F8EAf4 (remiliadao.eth)
0xE31985f594ea0199a64e5d3a667cA886Ed8fD382
0xA1A58311407Ab018141532e8Cf0a9CCCD1Bc9052
0xcf3e932f72E5f15411d125ad80579a3ef205b9B4 (Remilia multisig)
The multisig initially required 3/4 signers to approve transactions but was later increased to 4/4 signers. As the attacker had already obtained all the private keys for all 4 signers they were still able to drain the multisig wallet.
As of writing funds are split across three wallets. After selling NFTs, the first exploit wallet 0x778Be423ef77A20A4493f846BdbcDDfc30252cE9 split 844.8 ETH ($3m) across two new wallets, 0x8830509a9325f8E6d41040EC75Ec7a800Fd5BF97 and 0x3EE64685b78a26e458C4a6A585e3Cca29695E38f. The second exploit wallet, 0x8ac, received 211 ETH in addition to selling NFTs for a total combined balance of 492 ETH ($1.7m ).
Conclusion
Unfortunately, private key compromises have continued to be a major driver for the dollar losses in the crypto space. In 2023, only a small number of incidents attributed to private key misuse disproportionately affected the overall losses compared to other attack vectors. The difference so far in 2024 is that private key compromises have been a common occurrence with 24 incidents compared to 26 exit scams. If trends continue, we’ll likely see a higher number of private key incidents compared to 2023, and will continue to be a major driver for losses in the ecosystem.



